Searching for "learning management"
3 Tips for Managing Phone Use in Class
Setting cell phone expectations early is key to accessing the learning potential of these devices and minimizing the distraction factor.
Liz Kolb September 11, 2017
Ask your students questions such as:
- What do you like to do on your cell phone and why? (If they don’t have one, what would they like to do?)
- What are the most popular apps and websites you use?
- What do you think are inappropriate ways that cell phones have been used?
- What is poor cell phone etiquette? Why?
- How can cell phones help you learn?
- How can cell phones distract from your learning?
- How do you feel about your cell phone and the activities you do on your phone?
- What should teachers know about your cell phone use that you worry we do not understand?
- Do you know how to use your cell phone to gather information, to collaborate on academic projects, to evaluate websites?
- How can we work together to create a positive mobile mental health?
Using a Stoplight Management Approach
Post a red button on the classroom door: the cell phone parking lot.
Post a yellow button on the classroom door: Students know their cell phones should be on silent (vibrate) and placed face down in the upper right-hand corner of their desk. They will be using them in class, but not the whole time.
Post a green button on the classroom door: Students know they should have their phones turned on (either silenced or set on vibrate) and placed face up in ready position to use throughout the class.
Establishing a Class Contract
Ask your students to help you develop social norms for what is and is not appropriate cell phone use during green and yellow button times. Should they be allowed to go on their social media networks during class? Why or why not?
Ask them to brainstorm consequences and write them into a class contract.
+++++++++++++++++
more on the use of smart phones in the classroom in this IMS blog
https://blog.stcloudstate.edu/ims?s=phone+classroom
learning from real life experience
Today’s report on the use of Zello (http://www.marketwatch.com/story/houston-residents-and-civilians-turn-to-zello-app-to-coordinate-rescue-efforts-2017-08-29) by Houston residents during Hurricane Harvey has parallels with the organizational efforts of using Zello by the Venezuelan people (https://zello.com/channels/k/b2dDl) in 2014. (https://advox.globalvoices.org/2014/02/23/walkie-talkie-app-zello-blocked-in-venezuela/)
Zello, HeyTell and Voxer Make Your Smartphone a Walkie-Talkie (NYT, 2012) are apps for smart phones and mobile devices.
They are free.
They do much more than a physical walkie-talkie (e.g. send visuals, record messages)
They are more environment friendly, since do not require physical presence and so much battery power: https://www.compareninja.com/tables/single/60573
Yo is a similar messaging app: https://blog.stcloudstate.edu/ims/2014/07/09/social-media-yo/
Library and University use:
In 2014, we proposed to the middle management the consideration of Yo as alarm system:
From: Miltenoff, Plamen
Sent: Tuesday, July 08, 2014 9:17 PM
To: ??????, Mark A. <???????@stcloudstate.edu>
Subject: FW: Yo at LRS
Good evening Mark
Based on the article below:
http://www.businessinsider.com/yo-updates-on-israel-missile-attacks-2014-7
The upper management might consider fire and/or tornado alarm app for SCSU students similarly to the one, which the Israelis are using to back up their alarm system.
I am confident that some other US school is already thinking about the same and developing probably the app.
Thanks for considering…
Plamen
++++++++++++++++++
From: Miltenoff, Plamen
Sent: Tuesday, July 8, 2014 8:59 PM
To: ???????, Colette ?????????
Cc: ??????, Joseph
Subject: Yo at LRS
Collette,
I am not sure if this news
http://www.businessinsider.com/yo-updates-on-israel-missile-attacks-2014-7
will increase your interest toward “Yo” since you said that you are not interested in politics
As shared with Joe several months ago about “Zello” being used in Venezuela (http://www.huffingtonpost.ca/2014/02/21/venezuela-blocks-zello-ap_n_4830452.html ), ingenuity during political events can give us great ideas how to use social media apps in daily work
I would like to ask you again to consider testing Yo and sharing your ideas how we can apply it at LRS
It is worth checking the penetration of Yo among SCSU students and use it.
Thank you and lkng forward to hearing your opinion
Plamen
+++++++++++++++++++
benefits for the library and potentially for the campus:
- reduce financial cost: batteries for the walkie talkies and the wear off of the walkie talkie can be replaced by a virtual app (again, apps for each of the three potential candidates are free)
- environmentally friendly. Apps are virtual. Walkie talkies are physical
- improve productivity. walkie talkie allow only talk. Apps allow: audio, video (images) and text
- raise the level of critical thinking (increase productivity by proxy): the use of several media: text, visuals, audio will allow users to think in a wider diapason when troubleshooting and/or doing their tasks
- the library can be the sandbox to smooth out details of the application and lessons learned can help replace walkie talkies across campus with 21st century tools and increase productivity campus wide.
+++++++++++++++++++
previous posts on Zello in this IMS blog
https://blog.stcloudstate.edu/ims?s=zello
By Phil Hill

+++++++++++++++++
more on LMS in this iMS blog
https://blog.stcloudstate.edu/ims?s=learning+management
NMC Releases Second Horizon Project Strategic Brief on Digital Literacy
NMC Releases Second Horizon Project Strategic Brief on Digital Literacy
The New Media Consortium (NMC) has released Digital Literacy in Higher Education, Part II: An NMC Horizon Project Strategic Brief, a follow-up to its 2016 strategic brief on digital literacy.
PDF available here.
2017-nmc-strategic-brief-digital-literacy-in-higher-education-II-ycykt3
But what does it really mean to be digitally literate, and which standards do we use?” said Dr. Eden Dahlstrom, NMC Executive Director. “This report sheds light on the meaning and impact of digital literacy using cross-cultural and multi-disciplinary approaches, highlighting frameworks and exemplars in practice.
NMC’s report has identified a need for institutions and thought leaders to consider the ways in which content creation is unequally expressed throughout the world. In an examination of digital literacy within European, Middle Eastern, and African nations (EMEA), research has surfaced unequal access to information technology based on inequalities of economics, gender, race, and political divides.
| 2020 |
|
2015 |
|
| 1. |
Complex Problem Solving |
1. |
Complex Problem Solving |
| 2. |
Critical Thinking |
2. |
Coordinating with Others |
| 3. |
Creativity |
3. |
People Management |
| 4. |
People Management |
4. |
Critical Thinking |
| 5. |
Coordinating with Others |
5. |
Negotiation |
| 6. |
Emotional Intelligence |
6. |
Quality Control |
| 7. |
Judgment and Decision Making |
7. |
Service Orientation |
| 8. |
Service Orientation |
8. |
Judgment and Decision Making |
| 9. |
Negotiation |
9. |
Active Listening |
| 10. |
Cognitive Flexibility |
10. |
Creativity |
Digital tools themselves are merely enablers, pushing the envelope of what learners can create. No longer is it acceptable for students to be passive consumers of content; they can contribute to the local and global knowledge ecosystem, learning through the act of producing and discussing rich media, applications, and objects. In the words of many institutional mission statements, students do not have to wait until they graduate to change the world.
Using readily available digital content creation tools (e.g., video production and editing, web and graphic tools), students are evolving into digital storytellers,
digital literacy now encompasses the important skills of being able to coordinate with others to create something truly original that neither mind would fathom independently.
The ability to discern credible from inaccurate resources is foundational to digital literacy. my note: #Fakenews
A lack of broad consensus on the meaning of digital literacy still hinders its uptake, although a growing body of research is helping higher education professionals better navigate the continuous adjustments to the field brought about by emerging pedagogies and technologies.
Information literacy is a nearly universal component within these digital literacy frameworks. Critically finding, assessing, and using digital content within the vast and sometimes chaotic internet appears as a vital skill in almost every account, including those published beyond libraries. In contrast, media literacy is less widely included in digital literacy publications, possibly due to a focus on scholarly, rather than popular, materials. Digital literacies ultimately combine information and media literacy.
United States digital literacy frameworks tend to focus on educational policy details and personal empowerment, the latter encouraging learners to become more effective students, better creators, smarter information consumers, and more influential members of their community.
National policies are vitally important in European digital literacy work, unsurprising for a continent well populated with nation-states and struggling to redefine itself… this recommendation for Balkan digital strategy: “Media and information education (with an emphasis on critical thinking and switching from consumption to action) should start at early ages, but address all ages.”
African digital literacy is more business-oriented. Frameworks often speak to job skills and digital entrepreneurship. New skills and professions are emphasized, symbolized by the call for “new collar” positions.
Middle Eastern nations offer yet another variation, with a strong focus on media literacy. As with other regions, this can be a response to countries with strong state influence or control over local media. It can also represent a drive to produce more locally-sourced content, as opposed to consuming
Digital literacy is a complex phenomenon in 2017, when considered internationally. Nations and regions are creating ways to help their populations grapple with the digital revolution that are shaped by their local situations. In doing so, they cut across the genealogy of digital literacies, touching on its historical components: information literacy, digital skills, and media literacy.
2017-nmc-strategic-brief-digital-literacy-in-higher-education-II-ycykt3 
How Does Digital Literacy Change Pedagogy?
Students are not all digital natives, and do not necessarily have the same level of capabilities. Some need to be taught to use online tools (such as how to navigate a LMS) for learning. However, once digital literacy skills for staff and students are explicitly recognized as important for learning and teaching, critical drivers for pedagogical change are in place.
Pedagogy that uses an inquiry based/problem solving approach is a great framework to enhance the use and practice of digital skills/capabilities in the classroom.
The current gap between students’ information literacy skills and their need to internalize digital literacy competencies creates an opportunity for academic librarians to support students in the pursuit of civic online reasoning at the core of NMC’s multimodal model of three digital literacies. Academic librarians need a new strategy that evolves information literacy to an expanded role educating digitally literate students. Let’s build a new model in which academic librarians are entrepreneurial collaborators with faculty,55 supporting their classroom efforts to help students become responsible sharers and commentators of news on social media.
“Digital literacy is not just about ensuring that students can use the latest technologies, but also developing skills to select the right tools for a particular context to deepen their learning outcomes and engage in creative problem-solving”
There is a disconnect between how students experience and interact with technology in their personal lives and how they use technology in their roles as students. Yes, students are digitally savvy, and yes, universities have a role in questioning (insightfully of course) their sometimes brash digital savviness. We have a situation where students are expecting more, but (as I see it) cannot provide a clear demand, while faculty are unable to walk in the shoes of the students.
+++++++++++++++++++
more on digital literacy in this IMS blog
https://blog.stcloudstate.edu/ims?s=digital+literacy
Privacy & Security in Today’s Library by Amigos Library Services
From: Jodie Borgerding [mailto:Borgerding@amigos.org]
Sent: Wednesday, July 05, 2017 3:07 PM
To: Miltenoff, Plamen <pmiltenoff@stcloudstate.edu>
Cc: Nicole Walsh <WALSH@AMIGOS.ORG>
Subject: Proposal Submission for Privacy & Security Conference
Hi Plamen,
Thank you for your recent presentation proposal for the online conference, Privacy & Security in Today’s Library, presented by Amigos Library Services. Your proposal, The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party,” has been accepted. I just wanted to confirm that you are still available to present on September 21, 2017 and if you have a time preference for your presentation (11 am, 12 pm, or 2 pm Central). If you are no longer able to participate, please let me know.
Nicole will be touch with you shortly with additional details and a speaker’s agreement.
Please let me know if you have any questions.
Thanks!
___________________
Jodie Borgerding Consulting & Education Services Manager Amigos Library Services 1190 Meramec Station Road, Suite 207 | Ballwin, MO 63021-6902 800-843-8482 x2897 | 972-340-2897(direct) http://www.amigos.org | borgerding@amigos.org
+++++++++++++++++
Bio
Dr. Plamen Miltenoff is an Information Specialist and Professor at St. Cloud State University. His education includes several graduate degrees in history and Library and Information Science and terminal degrees in education and psychology.
His professional interests encompass social media, multimedia, Web development and design, gaming and gamification, and learning environments (LEs).
Dr. Miltenoff organized and taught classes such as LIB 290 “Social Media in Global Context” (http://web.stcloudstate.edu/pmiltenoff/lib290/) and LIB 490/590 “Digital Storytelling” (http://web.stcloudstate.edu/pmiltenoff/lib490/) where issues of privacy and security are discussed.
Twitter handle @SCSUtechinstruc
Facebook page: https://www.facebook.com/InforMediaServices/
The virtuality of privacy and security on the modern campus:
The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party software” teaching and learning
Abstract/Summary of Your Proposed Session
The virtualization reality changes rapidly all aspects of learning and teaching: from equipment to methodology, just when faculty have finalized their syllabus, they have to start a new, if they want to keep abreast with content changes and upgrades and engagement of a very different student fabric – Millennials.
Mainframes are replaced by microcomputers, microcomputers by smart phones and tablets, hard drives by cloud storage and wearables by IoT. The pace of hardware, software and application upgrade is becoming unbearable for students and faculty. Content creation and methodology becomes useless by the speed of becoming obsolete. In such environment, faculty students and IT staff barely can devote time and energy to deal with the rapidly increasing vulnerability connected with privacy and security.
In an effort to streamline ever-becoming-scarce resources, campus IT “standardizes” campus use of applications. Those are the applications, which IT chooses to troubleshoot campus-wide. Those are the applications recommended to faculty and students to use.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal, attention on campuses is drown to the fact that cyberattacks shift now from mobile devices to IoT and campus often are struggling even with their capability to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party application might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
Abstract
The pace of changes in teaching and learning is becoming impossible to sustain: equipment evolves in accelerated pace, the methodology of teaching and learning cannot catch up with the equipment changes and atop, there are constant content updates. In an even-shrinking budget, faculty, students and IT staff barely can address the issues above, less time and energy left to address the increasing concerns about privacy and security.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal (https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/), attention on campuses is drawn to the fact of cyberattacks shifting from mobile devices to IoT but campus still struggling to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party applications might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/
Anything else you would like to add
3 take-aways from this session:
- Discuss and form an opinion about the education-pertinent issues of privacy and security from the broad campus perspective, versus the narrow library one
- Discuss and form an opinion about the role of the library on campus in terms of the greater issues of privacy and security
Re-examine the thin red line of the balance between standardization and innovation; between the need for security and privacy protection a
++++++++++++++
presentation:
https://www.slideshare.net/aidemoreto/the-virtuality-of-privacy-and-security-on-the
chat – slide 4, privacy. please take 2 min and share your definition of privacy on campus. Does it differ between faculty and students? what are the main characteristics to determine privacy
chat – slide 5, security. please take 2 min and share your definition of security on campus regarding electronic activities. Who’s responsibility is security? IT issue [only]?
poles: slide 6, technology unsupported by campus IT, is it worth considering? 1. i am a great believer in my freedom of choice 2. I firmly follow rules and this applies to the use of computer tools and applications 3. Whatever…
chat – slide 6, why third party applications? pros and cons. E.g. pros – familiarity with third party versus campus-required
pole, slide 6, appsmashing. App smashing is the ability to combine mobile apps in your teaching process. How do you feel about it? 1. The force is with us 2. Nonsense…
pole slide 7 third party apps and the comfort of faculty. How do you see the freedom of using third party apps? 1. All I want, thank you 2. I would rather follow the rules 3. Indifference is my middle name
pole slide 8 Technology standardization? 1. yes, 2. no, 3. indifferent
chat slide 9 if the two major issues colliding in this instance are: standardization versus third party and they have impact on privacy and security, how would you argue for the one or the other?
++++++++++++++++
notes from the conference
Speaker: Dr. Steve Albrecht – drsteve@drstevealbrecht.com
Follow @DrSteveAlbrecht
Dr. Steve Albrecht, author of Library Security: Better Communication, Safer Facilities, manages a training, coaching, and management consulting firm, using a dedicated and experienced team of subcontractor specialists. He is internationally known for his consulting and training work in workplace violence prevention training programs, school violence prevention, and high-risk human resources. Dr. Albrecht provides HR consulting, site security assessments, coaching, and training workshops in supervisory improvement, workplace violence prevention, harassment prevention, drug and alcohol awareness, team building, and more. He holds a B.A. in English, B.S. in Psychology, M.A. in Security Management, and a doctoral degree in Business Administration (D.B.A.). He has been a trainer for over 26 years and is a certified Professional in Human Resources (PHR), a Certified Protection Professional (CPP), a Board Certified Coach (BCC), and a Certified Threat Manager (CTM).
Session Description: Libraries don’t always need to hire a consultant to review the level of facility security. Using a structured assessment process, librarians can create a report that will help to make their building, staff, and patrons safer.
Chris Markman, MSLIS, MSIT Public Services Librarian Worcester Public Library
https://mycourses.amigos.org/mod/url/view.php?id=19623
Measuring Library Vendor Cyber Security: Seven Easy Questions Every Librarian Can Ask
http://journal.code4lib.org/articles/11413
Bill Walker: http://www.amigos.org/innovating_metadata
+++++++++++++++
more on security in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=security
more on privacy in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=privacy
Survey Highlights Digitization’s Impact on Campus Libraries
By David Raths 05/22/17
https://campustechnology.com/articles/2017/05/22/survey-highlights-digitizations-impact-on-campus-libraries.aspx
nonprofit Ithaka S+R. The study, Ithaka S+R Library Survey 2016, highlighted a number of challenges facing library directors in an era of increased digitization. Future Trends Forum video chat May 19 hosted by Bryan Alexander.
Alexander zeroed in on the finding that library directors feel increasingly less valued by supervisors such as chief academic officers.
Not surprisingly, the survey illustrates a broad shift toward electronic resources, Wolff-Eisenberg noted, with an increasing number of libraries developing policies for de-accessioning print materials that are also available digitally.
library directors are increasingly recognizing that discovery does not always happen in the library. Compared to the 2013 survey results, fewer library directors believe that it is important that the library is seen by its users as the first place that they go to discover content, and fewer believe that the library is always the best place for researchers at their institution to start their research.
There is also a substantial gap between how faculty members and library directors perceive the library’s contribution in supporting student learning. Both tend to agree that students have poor research skills, Wolff-Eisenberg noted. The faculty members see it as more of a problem, but they are less likely than library directors to see librarians contributing to student learning by helping them to develop research skills
The positions for which respondents anticipate the most growth in the next five years are related to instructional design (my note: this is IMS), information literacy and specialized faculty research support involving digital humanities, geographical information systems (GIS) and data management.
++++++++++++++++++++++
more on digitization in academic libraries in this IMS blog
https://blog.stcloudstate.edu/ims?s=digitization+library
The Library in the Life of the User. Engaging with People Where They Live and Learn
p. 18
Library staff
The roles of librarians change with changes in user needs and demands and the technology employed. A survey conducted for Research Libraries UK found skill gaps in nine key areas in which subject librarians could be supporting researchers’ needs. Even though many librarians may want to hire new staff with these skills, a survey found that the reality for most will be training existing staff.
Definitions of library services will change. We need to grow the ways users can engage with whatever they value from libraries, whether papyrus rolls, maker spaces or data management instruction.
p. 19
What is the Unique Selling Point (USP) of libraries vis-à-vis other information service providers?
p. 21
Librarians should measure the effectiveness of services based on the users’ perceptions of success. Librarians also should move beyond surveys of how library space is being used and should conduct structured observations and interviews with the people using the space. It is not enough to know that the various spaces, whether physical or virtual, are busy. Librarians need to understand when and how the spaces are being used.
p. 33 What is Enough? Satisficing Information Needs
Role theory explains that: “When people occupy social positions their behavior is determined mainly by what is expected of that position rather than by their own individual characteristics” (Abercrombie et al., 1994, p. 360).
Rational choice theory is based on the premise that complex social behavior can be understood in terms of elementary individual actions because individual action is the elementary unit of social life. Rational choice theory posits that individuals choose or prefer what is best to achieve their objectives or pursue their interests, acting in their self-interest (Green, 2002). Stated another way, “When faced with several courses of action, people usually do what they believe is likely to have the best overall outcome” (Scott, 2000).
When individuals satisfice, they compare the benefits of obtaining “more information” against the additional cost and effort of continuing to search (Schmid, 2004)
p. 38
This paper examines the theoretical concepts—role theory, rational choice, and satisficing—by attempting to explain the parameters within which users navigate the complex information-rich environment and determine what and how much information will meet their needs.
p. 39
The information-seeking and -searching research that explicitly addresses the topic of “what is good enough” is scant, though several studies make oblique references to the stopping stage, or to the shifting of directions for want of adequate information. Kraft and Lee (1979, p. 50) propose three stopping rules:
1. The satiation rule, “where the scan is terminated only when the user becomes satiated by finding all the desired number of relevant documents”;
2. The disgust rule, which “allows the scan to be terminated only when the user becomes disgusted by having to examine too many irrelevant documents”; and
3. The combination rule, “which allows the user to be seen as stopping the scan if he/she is satiated by finding the desired number of relevant documents or disgusted by having to examine too many irrelevant documents, whichever comes first.”
p. 42
Ellis characterizes six different types of information activities: starting, chaining, browsing, differentiating, monitoring and extracting. He emphasizes the information- seeking activities, rather than the nature of the problems or criteria used for determining when to stop the information search process. In a subsequent article, Ellis (1997) observes that even in the final stages of writing, individuals may continue the search for information in an attempt to answer unresolved questions or to look for new literature.
p. 43
Undergraduate and graduate students
Situations creating the need to look for information (meeting assignment requirements):
• Writing research reports; and
• Preparing presentations.
Criteria used for stopping the information search (fulfilling assignment requirements):
1. Quantitative criteria:
— Required number of citations was gathered;
— Required number of pages was reached;
— All the research questions were answered; and
— Time available for preparing.
2. Qualitative criteria:
— Accuracy of information;
— Same information repeated in several sources;
— Sufficient information was gathered; and
— Concept understood.
Criteria used for stopping the information search (fulfilling assignment requirements):
1. Quantitative criteria:
— Required number of citations was gathered;
— Required number of pages was reached;
— All the research questions were answered; and
— Time available for preparing.
2. Qualitative criteria:
— Accuracy of information;
— Same information repeated in several sources;
— Sufficient information was gathered; and
— Concept understood.
p. 44
Faculty
Situations creating the need to look for information (meeting teaching needs):
• Preparing lectures and presentations;
• Delivering lectures and presentations;
• Designing and conducting workshops;
• Meeting scholarly and research needs; and
• Writing journal articles, books and grant proposals.
Criteria used for stopping the information search (fulfilling teaching needs):
1. Quantitative criteria:
— Time available for: preparing lectures and presentations; delivering lectures
— And presentations; and designing and conducting workshops; and
— Fulfilling scholarly and research needs.
2. Qualitative criteria:
— Every possible synonym and every combination were searched;
— Representative sample of research was identified;
— Current or cutting-edge research was found;
— Same information was repeated;
— Exhaustive collection of information sources was discovered;
— Colleagues’ feedback was addressed;
— Journal reviewers’ comments were addressed; and
— Publisher’s requirements were met.
1. Quantitative criteria for stopping:
— Requirements are met;
— Time constraints are limited; and
— Coverage of material for publication is verified by colleagues or reviewers.
2. Qualitative criteria for stopping:
— Trustworthy information was located;
— A representative sample of sources was gathered;
— Current information was located;
— Cutting-edge material was located;
— Exhaustive search was performed; and
— Exhaustive collection of information sources was discovered.
p. 53
“Screenagers” and Live Chat Reference: Living Up to the Promise
p. 81
Sense-Making and Synchronicity: Information-Seeking Behaviors of Millennials and Baby Boomers
p. 84 Millennials specific generational features pertinent to libraries and information-seeking include the following:
Immediacy. Collaboration. Experiential learning. Visual orientation. Results orientation. Confidence.
Rushkoff (1996) described the non-linearity of the thinking patterns of those he terms “children of chaos,” coining the term “screenagers” to describe those who grew up surrounded by television and computers (p. 3).
p. 85
Rational choice theory describes a purposive action whereby individuals judge the costs and benefits of achieving a desired goal (Allingham 1999; Cook and Levi 1990; Coleman and Fararo 1992). Humans, as rational actors, are capable of recognizing and desiring a certain outcome, and of taking action to achieve it. This suggests that information seekers rationally evaluate the benefits of information’s usefulness and credibility, versus the costs in time and effort to find and access it.
Role theory offers a person-in-context framework within the information-seeking situation which situates behaviors in the context of a social system (Mead 1934; Marks 1996). Abercrombie, et al. (1994, p. 360) state, “When people occupy social positions their behavior is determined mainly by what is expected of that position rather than by their own individual characteristics.” Thus the roles of information-seekers in the academic environment influence the expectations for performance and outcomes. For example, faculty would be expected to look for information differently than undergraduate students. Faculty members are considered researchers and experts in their disciplines, while undergraduate students are novices and protégés, roles that place them differently within the organizational structure of the academy (Blumer, 2004; Biddle, 1979; Mead, 1934; Marks, 1996; Marks, 1977).
+++++++++++++++++
more on research in this IMS blog
https://blog.stcloudstate.edu/ims?s=research
A Strategist’s Guide to Industry 4.0. Global businesses are about to integrate their operations into a seamless digital whole, and thereby change the world.
Industrial revolutions are momentous events. By most reckonings, there have been only three. The first was triggered in the 1700s by the commercial steam engine and the mechanical loom. The harnessing of electricity and mass production sparked the second, around the start of the 20th century. The computer set the third in motion after World War II.
Henning Kagermann, the head of the German National Academy of Science and Engineering (Acatech), did exactly that in 2011, when he used the term Industrie 4.0 to describe a proposed government-sponsored industrial initiative.
The term Industry 4.0 refers to the combination of several major innovations in digital technology
These technologies include advanced robotics and artificial intelligence; sophisticated sensors; cloud computing; the Internet of Things; data capture and analytics; digital fabrication (including 3D printing); software-as-a-service and other new marketing models; smartphones and other mobile devices; platforms that use algorithms to direct motor vehicles (including navigation tools, ride-sharing apps, delivery and ride services, and autonomous vehicles); and the embedding of all these elements in an interoperable global value chain, shared by many companies from many countries.
Companies that embrace Industry 4.0 are beginning to track everything they produce from cradle to grave, sending out upgrades for complex products after they are sold (in the same way that software has come to be updated). These companies are learning mass customization: the ability to make products in batches of one as inexpensively as they could make a mass-produced product in the 20th century, while fully tailoring the product to the specifications of the purchaser
.
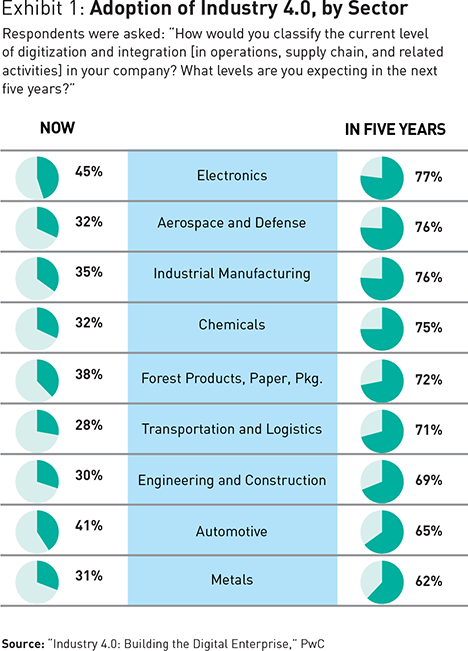
Three aspects of digitization form the heart of an Industry 4.0 approach.
• The full digitization of a company’s operations
• The redesign of products and services
• Closer interaction with customers
Making Industry 4.0 work requires major shifts in organizational practices and structures. These shifts include new forms of IT architecture and data management, new approaches to regulatory and tax compliance, new organizational structures, and — most importantly — a new digitally oriented culture, which must embrace data analytics as a core enterprise capability.
Klaus Schwab put it in his recent book The Fourth Industrial Revolution (World Economic Forum, 2016), “Contrary to the previous industrial revolutions, this one is evolving at an exponential rather than linear pace.… It is not only changing the ‘what’ and the ‘how’ of doing things, but also ‘who’ we are.”
This great integrating force is gaining strength at a time of political fragmentation — when many governments are considering making international trade more difficult. It may indeed become harder to move people and products across some national borders. But Industry 4.0 could overcome those barriers by enabling companies to transfer just their intellectual property, including their software, while letting each nation maintain its own manufacturing networks.
+++++++++++++++++++++++++++
more on the Internet of Things in this IMS blog
https://blog.stcloudstate.edu/ims?s=internet+of+things
also Digital Learning
https://blog.stcloudstate.edu/ims/2017/03/28/digital-learning/
NMC Horizon Report > 2017 Library Edition
http://www.nmc.org/publication/nmc-horizon-report-2017-library-edition/
PDF file 2017-nmc-horizon-report-library-EN-20ml00b
p. 26 Improving Digital Literacy
As social networking platforms proliferate and more interactions take place digitally, there are more opportunities for propagation of misinformation, copyright infringement, and privacy breaches.
p. 34 Embracing the need for radical change
40% of faculty report that their students ” rarely” interact with campus librarians.
Empathy as the Leader’s Path to Change | Leading From the Library, By Steven Bell on October 27, 2016, http://lj.libraryjournal.com/2016/10/opinion/leading-from-the-library/empathy-as-the-leaders-path-to-change-leading-from-the-library/
Empathy as a critical quality for leaders was popularized in Daniel Goleman’s work about emotional intelligence. It is also a core component of Karol Wasylyshyn’s formula for achieving remarkable leadership. Elizabeth Borges, a women’s leadership program organizer and leadership consultant, recommends a particular practice, cognitive empathy.
Leadership in disruptive times, James M. Matarazzo, Toby Pearlstein, First Published September 27, 2016, http://journals.sagepub.com/doi/full/10.1177/0340035216658911
What is library leadership? a library leader is defined as the individual who articulates a vision for the organization/task and is able to inspire support and action to achieve the vision. A manager, on the other hand, is the individual tasked with organizing and carrying out the day-to-day operational activities to achieve the vision.Work places are organized in hierarchical and in team structures. Managers are appointed to administer business units or organizations whereas leaders may emerge from all levels of the hierarchical structures. Within a volatile climate the need for strong leadership is essential.
Leaders are developed and educated within the working environment where they act and co-work with their partners and colleagues. Effective leadership complies with the mission and goals of the organization. Several assets distinguish qualitative leadership:
Mentoring. Motivation. Personal development and skills. Inspiration and collaboration. Engagement. Success and failure. Risk taking. Attributes of leaders.
Leaders require having creative minds in shaping strategies and solving problems. They are mentors for the staff, work hard and inspire them to do more with less and to start small and grow big. Staff need to be motivated to work at their optimum performance level. Leadership entails awareness of the responsibilities inherent to the roles of a leader. However, effective leadership requires the support of the upper management.
p. 36. Developments in Technology for Academic and Research Libraries
http://horizon.wiki.nmc.org/Horizon+Topics
- consumer technologies
- Digital strategies are not so much technologies as they are ways of using devices and software to enrich teaching, learning, research and information management, whether inside or outside the library. Effective Digital strategies can be used in both information and formal learning; what makes them interesting is that they transcended conventional ideas to create something that feels new, meaningful, and 21st century.
- enabling technologies
this group of technologies is where substantive technological innovation begins to be visible.
- Internet technologies.
- learning technologies
- social media technologies. could have been subsumed under the consumer technology category, but they have become so ever-present and so widely used in every part of society that they have been elevated to their own category. As well-established as social media is, it continues to evolve at a rapid pace, with new ideas, tools, and developments coming online constantly.
- Visualization technologies. from simple infographics to complex forms of visual data analysis. What they have in common is that they tap the brain’s inherent ability to rapidly process visual information, identify patterns, and sense order in complex situations. These technologies are a growing cluster of tools and processes for mining large data sets, exploring dynamic processes, and generally making the complex simple.

p. 38 Big Data
Big data has significant implications for academic libraries in their roles as facilitators and supporters of the research process. big data use in the form of digital humanities research. Libraries are increasingly seeking to recruit for positions such as research data librarians, data curation specialists, or data visualization specialists
p. 40 Digital Scholarship Technologies
digital humanities scholars are leveraging new tools to aid in their work. ubiquity of new forms of communication including social media, text analysis software such as Umigon is helping researchers gauge public sentiment. The tool aggregates and classifies tweets as negative, positive, or neutral.
p. 42 Library Services Platforms
Diversity of format and materials, in turn, required new approaches to content collection and curation that were unavailable in the incumbent integrated library systems (ILS), which are primarily designed for print materials. LSP is different from ILS in numerous ways. Conceptually, LSPs are modeled on the idea of software as a service (SaaS),which entails delivering software applications over the internet.
p. 44 Online Identity.
incorporated the management of digital footprints into their programming and resources
simplify the idea of digital footprint as“data about the data” that people are searching or using online. As resident champions for advancing digital literacy,304 academic and research libraries are well-positioned to guide the process of understanding and crafting online identities.
Libraries are becoming integral players in helping students understand how to create and manage their online identities. website includes a social media skills portal that enables students to view their digital presence through the lens in which others see them, and then learn how they compare to their peers.
p. 46 Artificial Intelligence
https://www.semanticscholar.org/
p. 48 IoT
beacons are another iteration of the IoT that libraries have adopted; these small wireless devices transmit a small package of data continuously so that when devices come into proximity of the beacon’s transmission, functions are triggered based on a related application.340 Aruba Bluetooth low-energy beacons to link digital resources to physical locations, guiding patrons to these resources through their custom navigation app and augmenting the user experience with location-based information, tutorials, and videos.
students and their computer science professor have partnered with Bavaria’s State Library to develop a library app that triggers supplementary information about its art collection or other points of interest as users explore the space
+++++++++++++++++++++++++++
more on Horizon Reports in this IMS blog
https://blog.stcloudstate.edu/ims?s=horizon+report
Susan Grajek at Bryan Alexander on IT and education
Forum takes a deep dive into higher education and technology. On Thursday, March 23rd, from 2-3 pm EST we will be joined by Susan Grajek, the vice president for communities and research at EDUCAUSE
+++++++++++++++++++
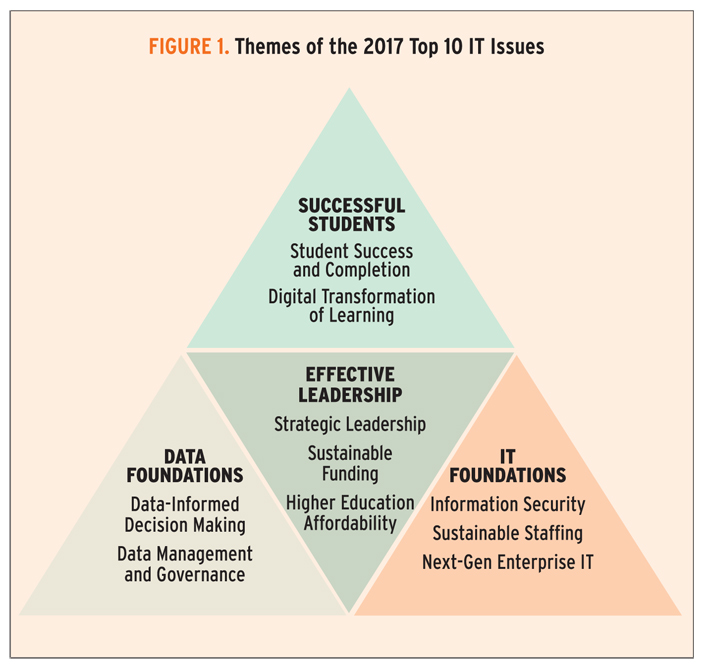
Top 10 IT Issues, 2017: Foundations for Student Success
- Susan Grajek and the 2016–2017 EDUCAUSE IT Issues Panel Tuesday, January 17, 2017http://er.educause.edu/articles/2017/1/top-10-it-issues-2017-foundations-for-student-successThe 2017 EDUCAUSE Top 10 IT Issues are all about student success
EDUCAUSE supports early adopters in this area through the Integrated Planning and Advising for Student Success (iPASS) grant challenge, a program in which EDUCAUSE helps develop models for the field by working closely with a small number of institutions that are pioneering iPASS systems.
Issue #1: Information Security
Developing a holistic, agile approach to reduce institutional exposure to information security threats
That program should encompass people, process, and technologies:
- Educate users
- Develop processes to identify and protect the most sensitive data
- Implement technologies to encrypt data and find and block advanced threats coming from outside the network via from any type of device
Who Outside the IT Department Should Care Most about This Issue?
- End-users, to understand how to avoid exposing their credentials
- Unit heads, to protect institutional data
- Senior leaders, to hold people accountable
- Institutional leadership, to endorse, fund, and advocate for good information security
Issue #2: Student Success and Completion
Effectively applying data and predictive analytics to improve student success and completion
Predictive analytics allows us to track trends, discover gaps and inefficiencies, and displace “best guess” scenarios based on implicitly developed stories about students.
Issue #3: Data-Informed Decision Making
Ensuring that business intelligence, reporting, and analytics are relevant, convenient, and used by administrators, faculty, and students
Higher education information systems generate vast amounts of data daily (including the classroom/LMS). This potentially rich source of information is underused. Even though most institutions have created reports, dashboards, and other distillations of data, these are not necessarily useful or used to inform strategic objectives such as student success or institutional efficiency.
Issue #4: Strategic Leadership
Repositioning or reinforcing the role of IT leadership as a strategic partner with institutional leadership
CIOs have two challenges in this regard. The first is getting to the table. Contemporary requirements for IT leaders position them well for strategic leadership.18 Those requirements include expertise in management and business practices, project portfolio management, negotiation, and change leadership. However, business-savvy CIOs can alienate some academics, particularly those opposed to administrators as leaders. Worse, not all CIOs are well-equipped for a position at the executive table.
Issue #5: Sustainable Funding
Developing IT funding models that sustain core services, support innovation, and facilitate growth
Two complications have deepened the IT funding challenge in recent years. The first is that information technology is now incontrovertibly core to the mission and function of colleges and universities. The second complication is that at most institutions, digital investments and technology refreshes have been funded with capital expenditures. Yet IT services and infrastructure are moving outside the institution, generally to the cloud, and cloud funding depends on ongoing expenditures rather than one-time investments.
Issue #6: Data Management and Governance
Improving the management of institutional data through data standards, integration, protection, and governance
Data management and governance is not an IT issue. It requires a broad, top-down approach because all departments need to buy in and agree. All stakeholders (data owners as well as IR, IT, and institutional leaders) must collaboratively develop a common set of data definitions and a common understanding of what data is needed, in what format, and for what purposes. This coordination, or governance, will enable constituents to communicate with confidence about the data (e.g., “the single version of truth”) and the standards (e.g., APLU, IPEDS, CDS) under which it is collected.
Institutions often choose to approach data management from three perspectives: (1) accuracy, (2) usability, and (3) privacy. The IT organization has a role to play in creating and maintaining data warehouses, integrating systems to facilitate data exchange, and maintaining standards for data privacy and security.
Issue #7: Higher Education Affordability
Prioritizing IT investments and resources in the context of increasing demand and limited resources
Uncoordinated, redundant expenditures supplant other needed investments, such as consistent classroom technology or dedicated information security staff. Planning needs to occur at the institutional or departmental level, but it also needs a place to coalesce and be assessed regionally, nationally, and in some cases, globally, because there isn’t enough money to do everything that institutional leaders, faculty, and others want or even need to do. Public systems are making some headway in sharing services, but for the most part, local optimization supersedes collaboration and compromise.
Issue #8: Sustainable Staffing
Ensuring adequate staffing capacity and staff retention as budgets shrink or remain flat and as external competition grows
As institutions become more dependent on their IT organizations, IT organizations are more dependent on the expertise and quality of their workforce. New hires need to be great hires, and great staff need to want to stay. Each new hire can change the culture and effectiveness of the IT organizations
Issue #9: Next-Gen Enterprise IT
Developing and implementing enterprise IT applications, architectures, and sourcing strategies to achieve agility, scalability, cost-effectiveness, and effective analytics
Buildings should outlive alumni; technology shouldn’t. IT leaders are examining core enterprise applications, including ERPs (traditionally, suites of financial, HR, and student information systems) and LMSs, for their ability to meet current and future needs.
Issue #10: Digital Transformation of Learning
Collaborating with faculty and academic leadership to apply technology to teaching and learning in ways that reflect innovations in pedagogy and the institutional mission
According to Michael Feldstein and Phil Hill, personalized learning applies technology to three processes: content (moving content delivery out of the classroom and allowing students to set their pace of learning); tutoring (allowing interactive feedback to both students and faculty); and contact time (enabling faculty to observe students’ work and coach them more).
+++++++++++++++++++++
more on IT in this IMS blog
https://blog.stcloudstate.edu/ims?s=information+technology




