VR in education

+++++++++++++++++
more on virtual reality in this IMS blog
Digital Literacy for St. Cloud State University

+++++++++++++++++
more on virtual reality in this IMS blog

+++++++++++++++++++++++
More on Vine in this IMS blog:
By Dian Schaffhauser 10/20/16
https://campustechnology.com/articles/2016/10/20/yik-yak-users-not-so-anonymous-after-all.aspx
yakkers had add personal handles and profiles starting last August. users of mobile app Yik Yak face the ignominy of being truly discoverable. At least that’s what a research team at New York University’s Tandon School of Engineering suggests in a new paper.
“You Can Yak but You Can’t Hide: Localizing Anonymous Social Network Users,” being presented at the upcoming ACM Internet Measurements Conference next month, describes how the research team was able to determine the geographical origin of a comment or “yak” and possibly even the person who made the post, thereby making the program susceptible to “localization attacks,” putting the user at risk of being identified.
if a student posted a disparaging remark about a fellow student or a faculty member, “it wouldn’t be difficult” for the victim of the insult to figure out where the offensive commentary was posted from and then pinpoint the probable yakker from there.
++++++++++++++++
more on privacy in this IMS blog
https://blog.stcloudstate.edu/ims?s=privacy
Mark your calendars:
Title: Mobile Device Management – Strategies for Success
Date: Wed. 11/09 | 02:00 PM EST // 11:00 AM PDT
Register now
++++++++++++++
more on BYOD in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=byod
By Matt Leonard Oct 18, 2016
https://fcw.com/articles/2016/10/18/hayden-email-espionage.aspx?
The Department of Homeland Security and the Office of the Director of National Intelligence issued a joint statement earlier this month that condemned Russia for the attacks.
“Do not drop this in the cyber problem box, drop this in the Russia problem box,” Hayden suggested, saying the focus should be on the actor, not the means. “And by the way, that Russian problem box needs a bigger box, there’s a lot of stuff going on.”
Though there are aspects of cybersecurity that only government can handle, most of it will be driven by the private industry, Hayden said. Government can help the private sector by getting out of the way — removing liability, enabling legal protections, sharing information and redoing the classification system.
And since the government too depends on the private sector for security innovation, Hayden said he sides with Apple regarding whether the company should have to create a back door for the FBI to bypass iPhone encryption.
+++++++++++++++++
more on surveillance, government in this IMS blog:
Who better to learn about incorporating 3D printing into instruction than from an instructor who taught the curriculum?
Join us on October 26th to hear directly from Assistant Professor Steve Chomyszak who used Stratasys 3D Printing Curriculum to teach a “Special Topics” 3D printing course at the Wentworth Institute of Technology.
During this complimentary webcast, you’ll gain valuable insight into the successes and lessons learned, including:
|
https://www.facebook.com/techinsider/videos/595046657360361/
+++++++++++++++++++++++++++++++
more on game consoles in this IMS blog
The first step to becoming an IoT Product Manager is to understand the 5 layers of the IoT technology stack.
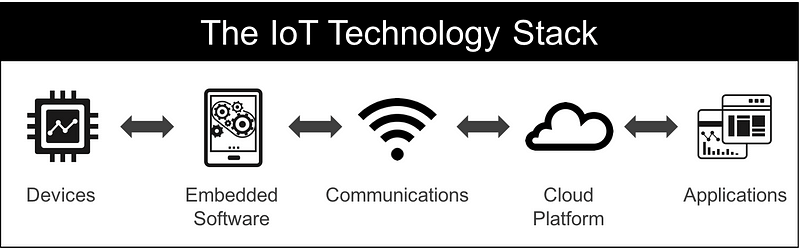
Devices constitute the “things” in the Internet of Things. They act as the interface between the real and digital worlds.
Embedded software is the part that turns a device into a “smart device”. This part of the IoT technology stack enables the concept of “software-defined hardware”, meaning that a particular hardware device can serve multiple applications depending on the embedded software it is running.
The complexity of your IoT solution will determine the type of embedded Operating System (OS) you need. Some of the key considerations include whether your application needs a real-time OS, the type of I/O support you need, and whether you need support for the full TCP/IP stack.
Common examples of embedded OS include Linux, Brillo (scaled-down Android), Windows Embedded, and VxWorks, to name a few.
This is the application(s) that run on top of the embedded OS and provide the functionality that’s specific to your IoT solution.
Communications refers to all the different ways your device will exchange information with the rest of the world. This includes both physical networks and the protocols you will use.
The cloud platform is the backbone of your IoT solution. If you are familiar with managing SaaS offerings, then you are well aware of everything that is entailed here. Your infrastructure will serve as the platform for these key areas:
Your smart devices will stream information to the cloud. As you define the requirements of your solution, you need to have a good idea of the type and amount of data you’ll be collecting on a daily, monthly, and yearly basis.
Analytics are one of they key components of any IoT solution. By analytics, I’m referring to the ability to crunch data, find patterns, perform forecasts, integrate machine learning, etc. It is the ability to find insights from your data and not the data alone that makes your solution valuable.
The Internet of Things is all about connecting devices and sharing data. This is usually done by exposing APIs at either the Cloud level or the device level. Cloud APIs allow your customers and partners to either interact with your devices or to exchange data. Remember that opening an API is not a technical decision, it’s a business decision.
Related post: The Business of APIs: What Product Managers Need to Plan For
This is the part of the stack that is most easily understood by Product teams and Executives. Your end-user applications are the part of the system that your customer will see and interact with. These applications will most likely be Web-based, and depending on your user needs, you might need separate apps for desktop, mobile, and even wearables.
As the Internet of Things continues to grow, the world will need an army of IoT-savvy Product Managers. And those Product Managers will need to understand each layer of the stack, and how they all fit together into a complete IoT solution.
++++++++++++++
more on Internet of Things in this blog:
https://www.facebook.com/trustmewebdesigner/posts/1018089721650451