Archive of ‘Digital literacy’ category
AcrGIS Living Atlas
https://www.esri.com/arcgis-blog/products/arcgis/imagery/new-pretrained-models-available-may-2022/
Edtech Trends 2022
7 Edtech Trends to Watch in 2022: a Startup Guide for Entrepreneurs
1. Data is abundant and the key to today’s edtech solutions
2. Artificial intelligence (AI) and machine learning (ML) are powering the latest generation of edtechs
3. Game-based learning is transforming how students learn
4. Edtechs are at the forefront of digital transformation in the classroom
5. Workforce upskilling is being supplemented by edtech solutions
6. Edtechs are being called upon to help with student wellbeing
7. Augmented reality (AR) and virtual reality are top of mind
Designing Online Assessment
Designing Online Assessment. Solutions that are Rigorous, Trusted, Flexible and Scalable
3 new techologies
Technologies That Are Going To Change Everything
The future is looking bright.
Vanadium Flow Batteries
limited to mostly stationary applications.
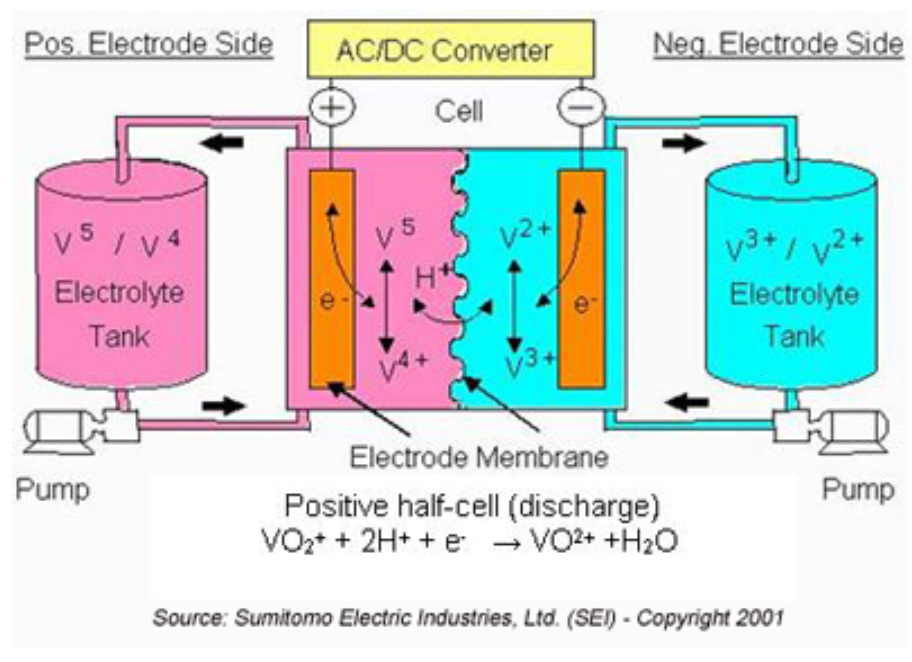
The main issue with Lithium batteries is the lack of profitability for recycling. The elements such as cobalt, nickel, and lithium all need to be extracted and separated, and then reassembled into new batterie
Programmable cells
Xenobots” and have essentially become living nanobots.