https://www.freetech4teachers.com/2020/10/addressing-two-common-copyright.html
Stanford University Library’s Measuring Fair Use
unless the images the person is using are so unique that there is nothing else like them and she’s using them in a critique or as an instructive example (for example, explaining an aspect of a Picasso painting) that’s not fair use.
Copyright for Teachers was a free webinar that Dr. Beth Holland and I hosted a few years ago. We addressed a slew of copyright questions and scenarios during presentation. You can watch the recording here.
In Three Lessons to Learn From the $9.2m Copyright Ruling Against Houston ISD I summarized what went wrong and how to avoid making the same mistakes.
fair use. You can watch that segment here.
Richard Stim, a major contributor to the Stanford site mentioned above, has a book called Getting Permission: How to License & Clear Copyrighted Materials Online & Off.
+++++++++++++++++++
more about copyright in IMS blog:
https://blog.stcloudstate.edu/ims?s=copyright
http://blogs.edweek.org/edweek/DigitalEducation/2020/11/student_data_future_criminals_pasco_privacy.html
Using Student Data to Identify Future Criminals: A Privacy Debacle
Under the federal Family Educational Rights and Privacy Act (FERPA), schools can share student records with a contractor or outside party to whom the school has outsourced certain functions, if that outside party (like a designated school resource officer) meets all three of these conditions:
- The outside party is performing a service that would otherwise be performed by school employees.
- The outside party’s use of education records is under the direct control of the school.
- The outside party does not use the education records for anything other than the reason they were originally shared, and does not share the education record with anyone else unless it secures written consent from the parent of the student.
Information Overload Helps Fake News Spread, and Social Media Knows It
Understanding how algorithm manipulators exploit our cognitive vulnerabilities empowers us to fight back
https://www.scientificamerican.com/article/information-overload-helps-fake-news-spread-and-social-media-knows-it/
a minefield of cognitive biases.
People who behaved in accordance with them—for example, by staying away from the overgrown pond bank where someone said there was a viper—were more likely to survive than those who did not.
Compounding the problem is the proliferation of online information. Viewing and producing blogs, videos, tweets and other units of information called memes has become so cheap and easy that the information marketplace is inundated. My note: folksonomy in its worst.
At the University of Warwick in England and at Indiana University Bloomington’s Observatory on Social Media (OSoMe, pronounced “awesome”), our teams are using cognitive experiments, simulations, data mining and artificial intelligence to comprehend the cognitive vulnerabilities of social media users.
developing analytical and machine-learning aids to fight social media manipulation.
As Nobel Prize–winning economist and psychologist Herbert A. Simon noted, “What information consumes is rather obvious: it consumes the attention of its recipients.”
attention economy
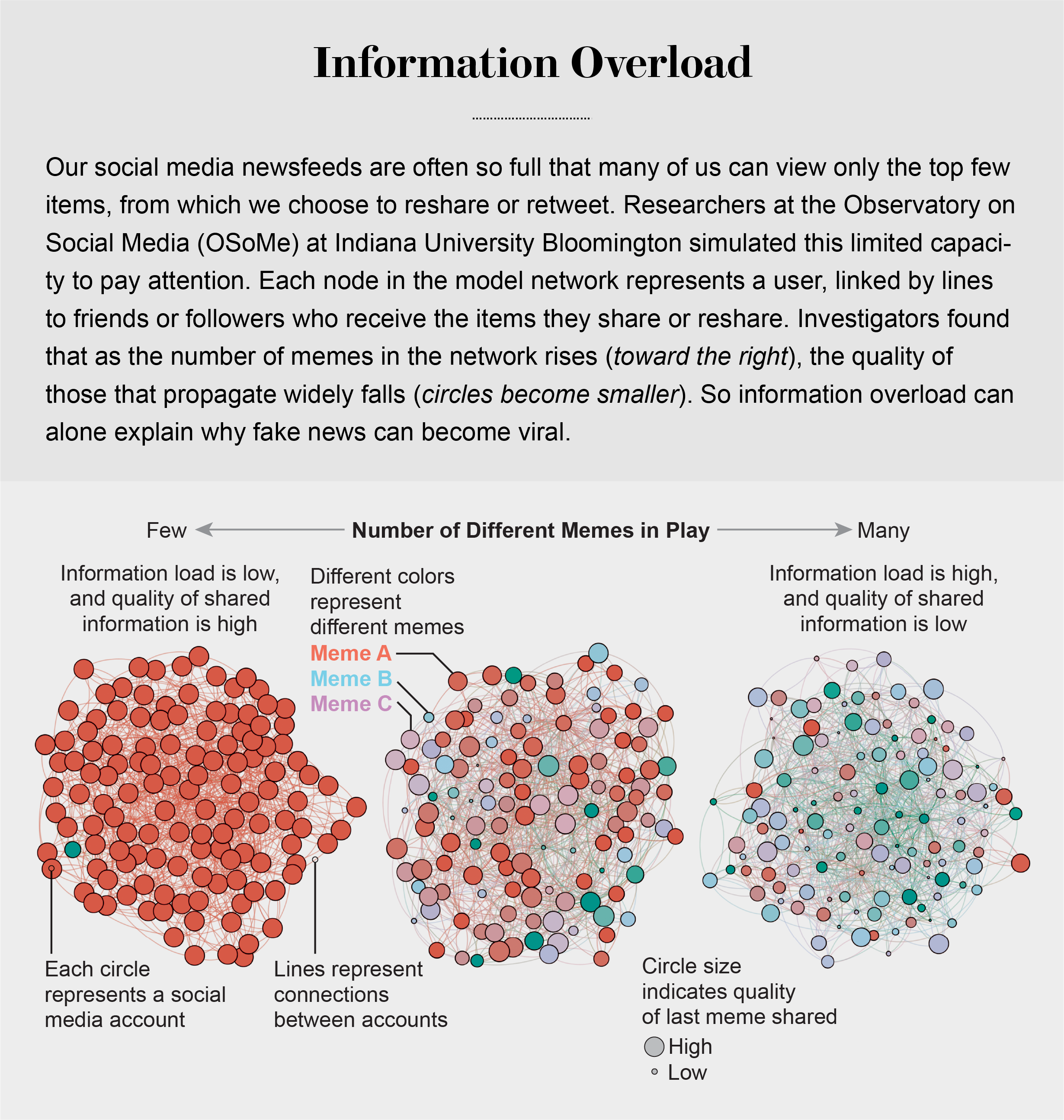
Our models revealed that even when we want to see and share high-quality information, our inability to view everything in our news feeds inevitably leads us to share things that are partly or completely untrue.
Frederic Bartlett
Cognitive biases greatly worsen the problem.
We now know that our minds do this all the time: they adjust our understanding of new information so that it fits in with what we already know. One consequence of this so-called confirmation bias is that people often seek out, recall and understand information that best confirms what they already believe.
This tendency is extremely difficult to correct.
Making matters worse, search engines and social media platforms provide personalized recommendations based on the vast amounts of data they have about users’ past preferences.
pollution by bots
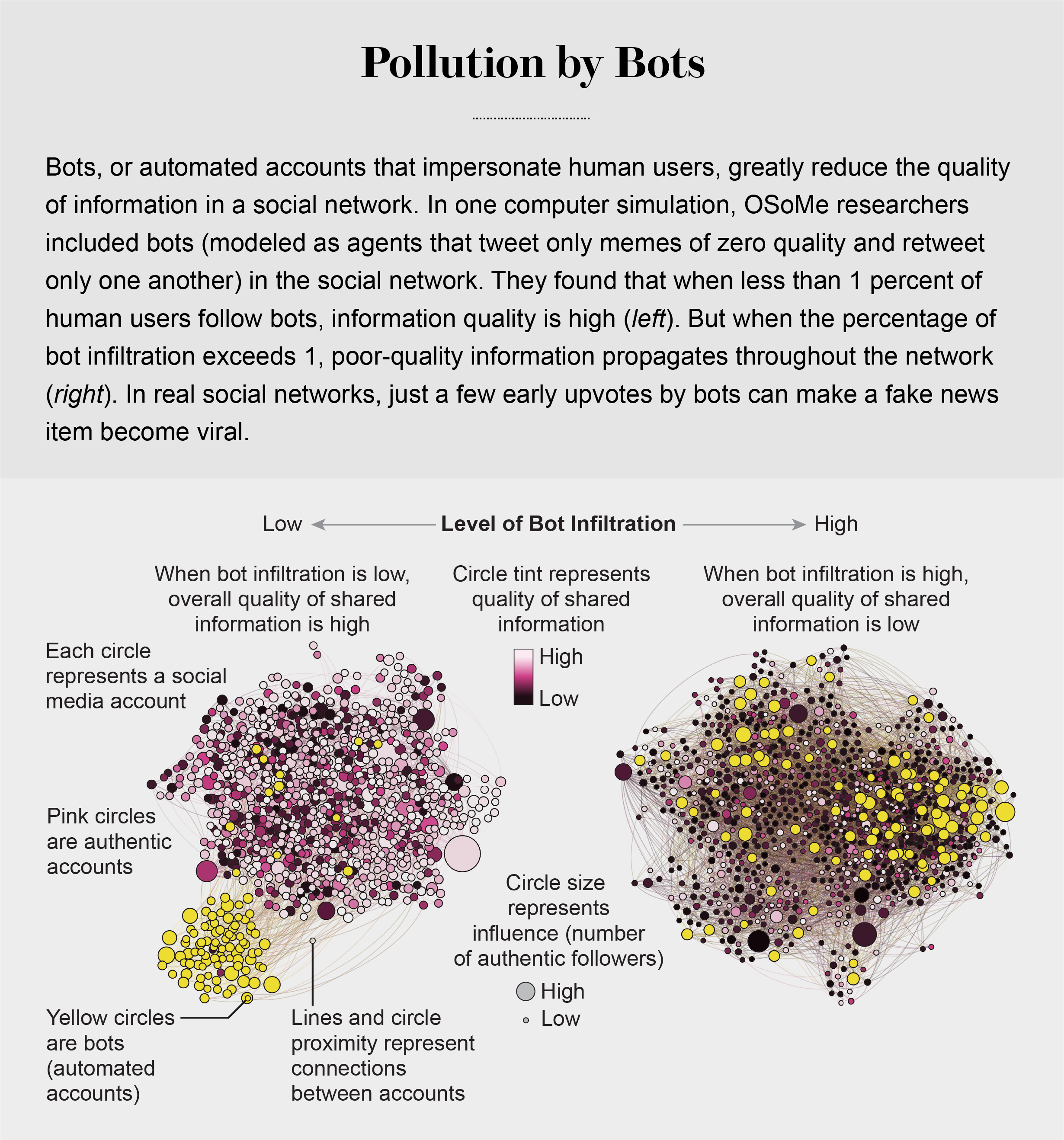
Social Herding
social groups create a pressure toward conformity so powerful that it can overcome individual preferences, and by amplifying random early differences, it can cause segregated groups to diverge to extremes.
Social media follows a similar dynamic. We confuse popularity with quality and end up copying the behavior we observe.
information is transmitted via “complex contagion”: when we are repeatedly exposed to an idea, typically from many sources, we are more likely to adopt and reshare it.
In addition to showing us items that conform with our views, social media platforms such as Facebook, Twitter, YouTube and Instagram place popular content at the top of our screens and show us how many people have liked and shared something. Few of us realize that these cues do not provide independent assessments of quality.
programmers who design the algorithms for ranking memes on social media assume that the “wisdom of crowds” will quickly identify high-quality items; they use popularity as a proxy for quality. My note: again, ill-conceived folksonomy.
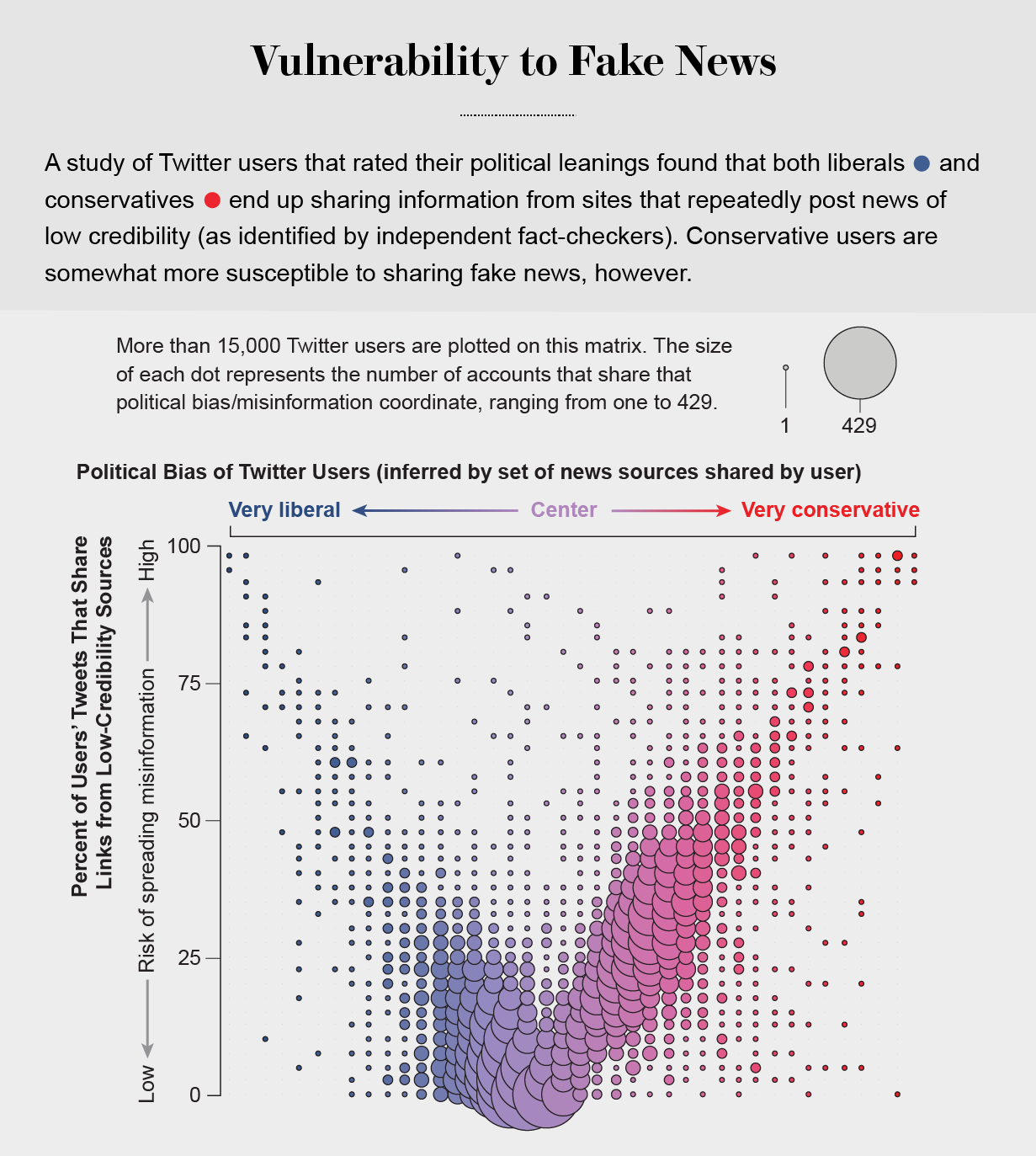
Echo Chambers
the political echo chambers on Twitter are so extreme that individual users’ political leanings can be predicted with high accuracy: you have the same opinions as the majority of your connections. This chambered structure efficiently spreads information within a community while insulating that community from other groups.
socially shared information not only bolsters our biases but also becomes more resilient to correction.
machine-learning algorithms to detect social bots. One of these, Botometer, is a public tool that extracts 1,200 features from a given Twitter account to characterize its profile, friends, social network structure, temporal activity patterns, language and other features. The program compares these characteristics with those of tens of thousands of previously identified bots to give the Twitter account a score for its likely use of automation.
Some manipulators play both sides of a divide through separate fake news sites and bots, driving political polarization or monetization by ads.
recently uncovered a network of inauthentic accounts on Twitter that were all coordinated by the same entity. Some pretended to be pro-Trump supporters of the Make America Great Again campaign, whereas others posed as Trump “resisters”; all asked for political donations.
a mobile app called Fakey that helps users learn how to spot misinformation. The game simulates a social media news feed, showing actual articles from low- and high-credibility sources. Users must decide what they can or should not share and what to fact-check. Analysis of data from Fakey confirms the prevalence of online social herding: users are more likely to share low-credibility articles when they believe that many other people have shared them.
Hoaxy, shows how any extant meme spreads through Twitter. In this visualization, nodes represent actual Twitter accounts, and links depict how retweets, quotes, mentions and replies propagate the meme from account to account.
Free communication is not free. By decreasing the cost of information, we have decreased its value and invited its adulteration.
https://www.npr.org/2020/11/14/934833214/conservatives-flock-to-mercer-funded-parler-claim-censorship-on-facebook-and-twi
Parler, founded in 2018, touts itself as “the world’s premier free speech platform.” On Saturday, CEO and co-founder John Matze said one of the privately owned company’s early investors is Rebekah Mercer, who along with her father, hedge fund billionaire Robert Mercer, has been a backer of President Trump and is also a major donor to conservative causes, including Breitbart News and former White House strategist Steve Bannon.
It has hit 10 million members — more than double the 4.5 million it had last week, according to Jeffrey Wernick, the company’s chief operating officer.
Still, that is just a tiny fraction of Twitter’s 187 million daily users and Facebook’s nearly 2 billion.
Experts say “free speech” approach lets false claims flourish
Gab, an alternative social network that has become notorious for hosting anti-Semitic and white nationalist content. It was used by the accused 2018 shooter at a Pittsburgh synagogue.
+++++++++++
more on echo chambers in this IMS blog
https://blog.stcloudstate.edu/ims?s=echo+chamber
https://mondediplo.com/2020/11/10huawei
Ren, a former engineer with the People’s Liberation Army who went into consumer electronics, played the patriotic card, cautioning Jiang that ‘switching equipment technology was related to national security, and that a nation that did not have its own switching equipment was like one that lacked its own military’ (1). A quarter of a century later, other countries, led by the US, have belatedly grasped the wisdom of Ren’s remarks; the technology in question today is 5G
The company operates networks in 170 countries and employs more than 194,000 people.
This summer it overtook Samsung as the world’s biggest seller of smartphones… boast some of the most advanced artificial intelligence capabilities on the market.
spending more than 10% of its annual profits on research and development. In 2019 it spent over $15bn — more than Apple and Microsoft — and the budget for 2020 is $20bn. (For comparison, the R&D spend of the entire German car industry in 2018 was roughly $30bn.)
Huawei and 5G are only a small part of a much larger geoeconomic and geopolitical struggle in which China is trying to gain the upper hand over the US.
Washington’s campaign against Chinese tech includes firms such as the state-owned ZTE, another important player in the 5G field, WeChat and TikTok and many other lesser-known companies. But Huawei is its main target.
Washington sees Huawei as an arch-example of China’s rogue behaviour (widely mistaken for meritocratic market success) — stealing intellectual property, bullying partners and undercutting competitors
The EU has failed to agree a common policy on 5G.
++++++++++++++
more on Huawei in this IMS blog
https://blog.stcloudstate.edu/ims?s=huawei
Real-time technology like Epic Games’ Unreal Engine has emerged as a successful tool and resource to implement this type of teaching and learning.
Storytelling is a major component of so many professions.
use digital portfolios and our critique process by viewing a StoryMap I made using Geographic Information Systems (GIS)
_++++++++++++++++++
more on Unreal Engine in this IMS blog
https://blog.stcloudstate.edu/ims?s=unreal+engine


