Nov
2016
hacking voting
A Voice Cuts Through, and Adds to, the Intrigue of Russia’s Cyberattacks
++++++++++++++++++++
more on Eastern European hackers in this IMS blog:
https://blog.stcloudstate.edu/ims/2016/06/22/ukrainian-hacker-and-fbi/
Digital Literacy for St. Cloud State University
++++++++++++++++++++
more on Eastern European hackers in this IMS blog:
https://blog.stcloudstate.edu/ims/2016/06/22/ukrainian-hacker-and-fbi/
http://2017.code4lib.org/workshops/proposed-workshops.html
Introduction to functional programming principles, including immutability, higher-order functions, and recursion using the Clojure programming language. This workshop will cover getting started with the Clojure REPL, building programs through function composition, testing, and web-development using ClojureScript.
This workshop will do a deep dive into approaches and recommend best practices for customizing Blacklight applications. We will discuss a range of topics, including styling and theming, customizing discovery experiences, and working with Solr.
We all encounter failure in our professional lives: failed projects, failed systems, failed organizations. We often think of failure as a negative, but it has intrinsic value — and since it’s inevitable that we’ll eventually experience failure ourselves, it’s important to know how to accept it, how to take lessons from it, and how to grow from it professionally. Fail4Lib, now in its 5th year, is the perennial Code4Lib preconference dedicated to discussing and coming to terms with the failures that we all face in our professional lives. It is a safe space for us to explore failure, to talk about our own experiences with failure, and to encourage enlightened risk taking. The goal of Fail4Lib is for participants to be adept at failing gracefully, so that when we do fail, we do so in a way that moves us forward. This half-day preconference will consist of case studies, round-table discussions, and, for those interested in sharing, lightning talks on failures we’ve dealt with in our own work.
Intro to programming in Ruby on Rails
Amazon Web Services currently offers 58 services ranging from the familiar compute and storage systems to game development and the internet of things. We will focus on the 20-some services that you should be aware of as you move your applications to their cloud.
The morning session will be mostly overview and the afternoon session will be more practical examples and discussion. This could be broken into two sessions.
FOLIO is a library services platform — infrastructure that allows cooperating library apps to share data. This workshop is a hands-on introduction to FOLIO for developers of library apps. In this tutorial you will work with your own Vagrant image through a series of exercises designed to demonstrate how to install an app on the platform and use the data sources and design elements the platform provides.
REQUIREMENTS Laptop (4GB) with Vagrant installed.
Have an idea for an app? Want to work with FOLIO developers and others in the community on the FOLIO platform to make it happen. Come to this half-day hack-a-thon! Ideas for new developers will be posted in the project Jira, or bring your own concepts and work with others to make them reality.
REQUIREMENTS Laptop (4GB) with Vagrant installed. Attending the FOLIO Tutorial is recommended, but not required.
Google Apps script is a server-side implementation of JavaScript which supports API calls to Google Services. This can provide an excellent platform for developing simple library applications. The libraries at Georgetown University and the University of Dayton have successfully deployed applications built with Google App Script.
In this workshop, we will step through the various types of applications that can be built with Google Apps Script.
(1) Custom cell formulas
(2) Spreadsheet Add On Functions (menu items, time based triggers)
(3) Google Apps Script as a Web Service
(4) Google Apps Script Add-Ons that can be shared globally or by domain
In this workshop, we will build sample instances of each of these types of applications (wifi-permitting) and spend some time brainstorming additional applications that would be useful for the library community.
Sample Applications: http://georgetown-university-libraries.github.io/#google-sheets
Calls to mindfulness and self care can have mixed reception in our field. While some view this important work as navel-gazing or unnecessary, it is integral to being present and avoiding burnout. Often this skewed attention to output comes at the expense of our personal lives, our organizations, our health, our relationships, and our mental well-being. Learning to prioritize self-care is an ongoing project among those who perform emotional labor. While some view the work of mindfulness as self-indulgent, it has proven to keep many on the track of being present and avoiding burnout.*
The purpose of this preconference is to provide a short introduction to self care and mindfulness with practical work we can use regardless of setting. We’ll discuss microaggressions and allyship (microaggressions being the brief and commonplace verbal, behavioral, or environmental indignities that marginalized people of various groups experience daily and allyship referring to the powerful role that individuals from privileged groups can play in supporting marginalized individuals). We will then transition to a modified unconference setting where participants can practice scenarios and learn practical solutions. Each of the presenters has different set of skills and experiences that allow for many techniques and strategies to be explored. Preconference attendees will participate in sessions like “Mentor Speed Dating” where they get to talk to and question potential mentors/mentees. They may be coached through a guided meditation or walked through a calming breathing exercise. For those looking to a more physical space, office yoga and stretching techniques may be shared depending on the outcomes of the unconference interest.
Foundational materials and articles will be shared with the registrants prior to the meeting with the option of further discussion at the workshop. An open access guide to all the resources and readings will be available after the preconference, and people will be encouraged to share additional their tools on a website.
Suggested Hashtag #c4lselfcare
* Abenavoli, R.M., Jennings, P.A., Greenberg, M.T., Harris, A.R., & Katz, D.A. (2013). The protective effects of mindfulness against burnout among educators. Psychology of Education Review, 37(2), 57-69
In this preconference, participants will be introduced to Virtual Reality uses in library settings, notably, by way of the VR Reading Room. Within the VR Reading Room prototype, users can collaboratively explore digital collections (e.g. HathiTrust) by way of VR headsets. Participants of this workshop will have the opportunity to experience HTC Vive functionality. The system will be setup with a prototype e-book experiment in order to model several VR affordances. Once attendees have been introduced to the HTC Vive hardware and sample project, groups of participants will have an opportunity to further brainstorm novel uses cases.
Python[1] has become one of the dominant languages in scientific computing and is used by researchers around the world. Its popularity is due in large part to a rich set of libraries for data analysis like Pandas[2] and NumPy[3] and tools for exploring scientific code like Jupyter notebooks[4]. Join us for this half-day workshop on the basics of using Pandas within a Jupyter notebook. We will cover importing data, selecting and subsetting data, grouping data, and generating simple visualizations. All are welcome, but some familiarity with Python is recommended, e.g. the concepts covered in the Codecademy[5] or Google[6] Python courses.
[1] https://www.python.org/
[2] http://pandas.pydata.org/
[3] http://www.numpy.org/
[4] http://jupyter.org/
[5] https://www.codecademy.com/learn/python
[6] https://developers.google.com/edu/python/
Learn about the features and capabilities of Sufia, a Hydra-based repository solution. Attendees will participate in a hand-on demonstration where they deposit content, edit metadata, create collections, and explore access control options. Attendees should bring laptops with Chrome, Firefox, or Safari installed. Please plan on bringing at least one image, document, or other digital content that you’re comfortable uploading and using for demo and experimentation purposes 🙂
The web can be a trove of openly accessible data, but it is not always readily available in a format that allows it to be downloaded for analysis and reuse. This workshop aims to introduce attendees to web scraping, a technique to automate extracting data from websites.
Part one of the workshop will use browser extensions and web tools to get started with web scraping quickly, give examples where this technique can be useful, and introduce how to use XPath queries to select elements on a page.
Part two will introduce how to write a spider in Python to follow hyperlinks and scrape several web pages using the Scrapy framework. We will conclude with an overview of the legal aspects of web scraping and an open discussion.
You don’t need to be a coder to enjoy this workshop! Anyone wishing to learn web scraping is welcome, although some familiarity with HTML will be helpful. Part two will require some experience with Python, attendees unfamiliar with this language are welcome to stay only for part one and still learn useful web scraping skills!
Paper prototyping is a low-cost, structured brainstorming technique that uses materials such as paper and pencils to better understand the way users interact with physical, visual, and textual information. It can help us learn how to better think through workflows, space design, and information architecture. Session attendees will learn about the ways low-fidelity prototyping and wireframing can be used to develop ideas, troubleshoot workflows, and improve learning and interaction.
In the first half of the workshop, participants will step through activities in icon design, persona development, and task development. In the second half they will develop a low fidelity prototype and step through a guerilla usability testing process with it.
The conference welcomes proposals for papers and interactive presentations about research or teaching approaches using digital methods. For the first time in 2017, Digitorium also seeks to provide training opportunities for scholars of all levels keen to learn new digital techniques to advance their work, whether by learning a new digital mapping tool, discovering simple ways of visualizing research findings, using computers to conduct large-scale qualitative research, or experimenting with big data approaches at your desktop. There will be a stream of hands-on workshops running throughout the conference enabling participants both to share their own work, and also to expand their portfolio.
Digitorium 2017 will take place from Thursday 2nd to Saturday 4th March, and again, our primary focus is on digital methods, as this has provided fertile ground for interdisciplinary conversations to grow. There will be “tracks” through the conference based on: methods; early modern studies; American studies; and digital pedagogy. We welcome presentations on any topics engaging digital methods for scholarly purposes, whether for research, teaching, or community projects.
In 2017, the conference is expanding once more to offer not only multiple plenary sessions, panels, papers, and roundtables, but also a concerted series of workshops offering training for delegates in a variety of Digital Humanities techniques for research and teaching, from mapping to text encoding, digital data analysis, and more, to support enhanced professional development opportunities at the conference for faculty, staff, and graduate students.
This year, we are proud to present two plenary sessions and our first-ever plenary hackathon! Professor Scott Gwara (Univ. of South Carolina) will be presenting on MS-Link, a database that he created reunifying scattered manuscripts into full digital codices. Additionally, joint principal investigators of the Isabella D’Este Archive (IDEA) Project, Professor Anne MacNeil (Univ. of North Carolina at Chapel Hill) and Professor Deanna Shemek (Univ. of California Santa Cruz) will be presenting their work on a digital archive uniting music, letters, and ceramics, and will lead our first live hackathon, engaging participants in the new virtual reality component of their project.
There will once again be a discounted “group rate” for registration to enable participants to bring their team with them, as collaboration is such a hallmark in digital scholarship, and it would be great to be able to hear about projects from multiple different perspectives from the people working together on them. There are also discounted rates available for graduate student presenters, and UA faculty. I do not mean to impose, but if this is an event which would be of interest to colleagues and collaborators, I would be enormously grateful if you might be able to circulate our CFP or a link to our website with them, we really want to let as many people as possible know about the conference to ensure it will be a real success.
Here is a link to the website which includes the full-length CFP:
https://apps.lib.ua.edu/blogs/digitorium/
Methods provide the focus for our conference, both in a pragmatic sense in terms of the use of different techniques to achieve particular DH projects, but also the ways in which sharing digital methods can create new links between disciplines in the humanities and social sciences. The idea powering Digitorium is to build on the community which has emerged in the course of the previous two years’ events in order to create a space for conversations to take place between scholars, graduate students, and practitioners from many different disciplines about their shared methods and techniques which unite them in their digital work.
++++++++++++++++++
more on digital humanities in this IMS blog:
https://blog.stcloudstate.edu/ims?s=digital+humanities
An idea for online courses is that assessment should not only be a one way process where the students get grades and feedback. The examination process should also be a channel for students’ feedback to teachers and course instructors (Mardanian & Mozelius, 2011). New online methods could be combined with traditional assessment in an array of techniques aligned to the learning outcomes (Runyon and Von Holzen, 2005). Examples of summative and formative assessment in an online course could be a mix of: Biometric Belt and Braces for Authentication in Distance Education.
Authors’ suggestion is a biometric belt and braces model with a combination of scanned facial coordinates and voice recognition, where only a minimum of biometric data has to be stored. Even if the model is based on biometrics with a medium to low grade of uniqueness and permanence, it would be reliable enough for authentication in online courses if two (or more) types of biometrics are combined with the presented dialogue based examination using an interaction/obser ‐ vation process via web cameras. Biometric Belt and Braces for Authentication in Distance Education.
++++++++++++++++++
more on identification in this IMS blog
https://blog.stcloudstate.edu/ims?s=identification
http://www.wgu.edu/blogpost/innocent-red-flags-caught-by-online-exam-proctors
voices from the other side:
http://infoproc.blogspot.com/2013/04/how-to-cheat-online-exam-proctoring.html
https://campustechnology.com/articles/2016/04/06/how-students-try-to-bamboozle-online-proctors.aspx
Beating, Cheating, and Defeating Online Proctoring
http://www.executiveacademics.com/single-post/2016/1/5/Beating-Cheating-and-Defeating-Online-Proctoring
The reputations of Asian universities, and Chinese universities in particular, are on the rise. China’s World Class 2.0 project, announced in August 2015, aims to strengthen the research performance of China’s nine top-ranked universities, with the goal of having six of those institutions ranked within the world’s top 15 universities by 2030.
After two decades in which China has been largely an exporter of students to Australia, Canada, the US and the UK, it is now increasingly attracting international students to study at its universities. And what is true of China is true of other countries too. Global flows of students are an increasing feature of the world’s higher education systems.
You can see the recruitment of international students as an exercise in soft power, in global engagement , in global citizenship, a great exercise in language learning , the practical application of a challenge thrown down by the great American social anthropologist Clifford Geertz.
Certainly, my friends who lead universities in Australia, Canada and New Zealand are delighted when they read politicians’ rhetoric about making it harder for international students to come to the UK.(my note, this is a Guardian article, but applies perfectly with Bush Junior politics and with the rhetoric of Trump)
+++++++++++++++
more on globalization in this IMS blog:
Critical thinking scholars also agree that questions are central to students acquiring critical thinking skills. We must ask students challenging, open-ended questions that demand genuine inquiry, analysis, or assessment—questions like these:
Some teaching methods naturally promote inquiry, analysis, and assessment, and all of them are student-active (Abrami et al., 2008). Class discussion may be the strongest, and it includes the debriefings of complex cases, simulations, and role plays. However, debates, structured controversy, targeted journaling, inquiry-guided labs, and POGIL-type worksheets (https://pogil.org/) are also effective.
+++++++++++++++++
more on critical thinking in this IMS blog
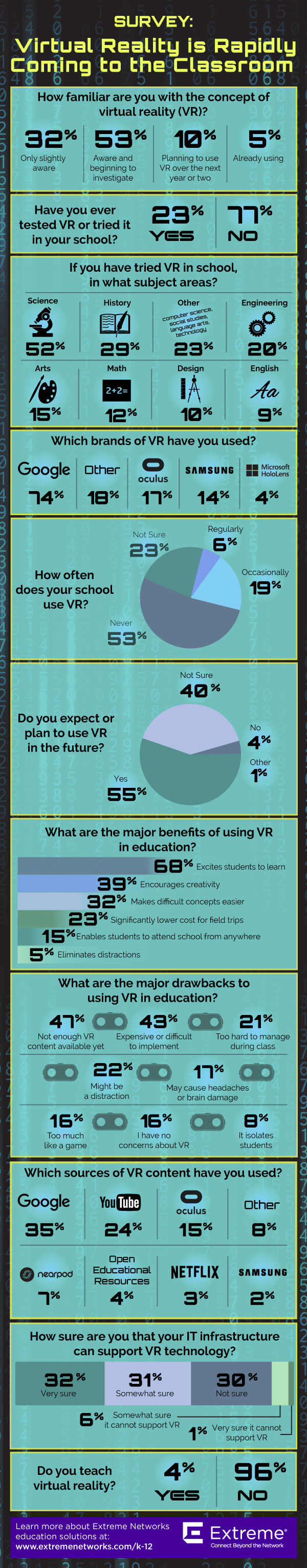
3. For anatomy and dissection: Said one Extreme Networks survey respondent, “Our students have been developing a VR model of a cow’s anatomy for dissection and study. You have the ability to drill down to the circulatory system, brain, muscle, skeleton, etc. Our applied tech program is using VR in conjunction with Autocad for models of projects they design.”
4. For engagement: A whopping 68 percent of survey respondents said the major benefit of using VR in education is to excite students about the subject matter. 39 percent said it’s great for encouraging creativity.
5. For field trips: Google has eliminated restrictions on Expeditions, their VR field trips program. Google Expeditions was cited in the survey as one of the most popular sources of VR content, but with the complaint that it was a restricted program.
comment:
Thomas S. McDonald ·
+++++++++++++++
more on VR in this IMS blog
https://blog.stcloudstate.edu/ims?s=virtual+reality
In this Business Insider video:
https://www.facebook.com/businessinsider/videos/10154001218189071/
‘Shark Tank‘ investor Robert Herjavec reveals the biggest mistakes small businesses make:
the difference between small business and academic institution, being that the library or the entire university, is that small business is reliant on itself; if it does not well, it perishes. The library and the university are reliant on external funds and can fester for a long time. But eventually it dies. In that sense, learning from the lessons for small business can help:
opportunity to user to develop a sense of ownership over the library resources.
Photo-sharing sites already have taken sharp inroads into the field of teaching-learnin encouraging a shift from teacher-led approach to user centred engagement (Kawka, et al,2012).
Introducing photo-sharing sites and integrating with other social networking sites, libraries are now making their web presence outside the “traditional web platform”. With facility of online managing and sharing of digital images, photo-sharing sites enable users to get remotely connected with others and interact with comment links. Photo-sharing sites that are commonly being used by libraries are Flickr (www.flickr.com), Instagram (instagram.com), Pinterest (in.pinterest.com), Photobucket (photobucket.com), Picasa (picasa.google.com), SmugMug (www.smugmug.com), etc (Bradley, 2007; Kroski, 2008; Salomon, 2013).
The results showed that blog and RSS are among the mostly used applications and web 0 applications are associated with overall website quality, particularly to the service quality.
Stvilia and Jörgensen (2010) suggests that controlled vocabulary terms may be
37 complemented with those user generated tags which users feel more comfortable with for information The study also reflects a growing interest among the user community to be involved in “social content creation and sharing communities in creating and enhancing the metadata of their photo collections to make the collections more accessible and visible”.
page 7-8.
2.1 Steps to increase accessibility to photo-sharing sites
a) Improve visibility: To make photo-sharing sites of the library easily visible, a direct link to library homepage is essential
p. 9
2.2 Purposes of using photo-sharing sites
a) Organising library tour
b) Community building
c) Tool for digitisation
d) Grabbing the users at their own place
e) Integrating Feeds with other application
f) Displaying new arrivals : Newly added books
g) Sharing news & events and publicize library activities
h) Archives of exhibits
i) Portal for academic and research activity: Photo-sharing sites may serve as platform tofoster teaching learning activity, particularly for those who may use these image resource sites for academic purpose
j) Experimentation : Being a relatively new approach to users service, these tools may be introduced on experimental basis to examine their proper utilisation before final implementation
k) Miscellaneous : Public library can reach out to the community physically, offer service to the traditionally underserved, homebound or people with disability, implement programmes to include marginalised section of the community and showcase its mobile outreach efforts in photo-sharing sites.
page 12-13
Before going to integrate photo-sharing site, a library should set the strategic objectives i.e., what purposes are to be served. “Purpose can provide clarity of vision when creating policies or guidelines” (Garofalo, 2013, p.28). The above discussedrange of purposes may help librarians to develop better understanding to makeinformed selection of photo-sharing utility and the nature of images to be posted through it. Goal setting should precede consideration of views of a sizeable section of all library stakeholders to know beforehand what they expect from the library.
• Once the purposes are outlined, a library should formulate policy/ guideline for photo-sharing practices, based on user requirement, staff resource, available time component and technological support base. Policy offers a clear guideline for the users and staff to decide the kind of images to be posted. A guideline is indeed essential for the optimum use of photo-sharing site. It also delineates the roles and responsibilities of the staff concerned and ensures regular monitoring of the posts. Policy may highlight fair use guidelines and allow re-use of images within the scope of copy-right.
• A best way to start is integrating an app, involving simple design with fewer images and let users be familiarized with the system. During the course of development more and more apps may be added, with more images to be posted to serve variety of purposes, depending on the institutional resource and user demand.
• Accessibility to photo-sharing site largely depends on its visibility to the audience. Icon of photo-sharing utility prominently located on website will increase the presentation of its visual identity. Library may set links to photo-sharing sites at home page or at drilled-down page.
• Being an emerging technology, photo-sharing site needs adequate exposure for optimum usage. Annotations associated to photo-sharing site will give an idea about the online tool and will guide users to better harness the application.
• Photo-sharing sites allow images to be organised in a variety of way. Categorising image resources under various topical headings at one location will improve resource identification and frees one from extensive searching.
• Regular posting of engaging images to photo-sharing site from the library and follow- up will attract users to tag and share images and strengthen community involvement with active user participation.
• “Social and informal photographs” of library staff will make them more approachable and strengthen patron-staff relationship.
• Library should seek user comments and suggestions to improve current photo-sharing application and to incorporate fresh element to library service provision. User feedback may be considered as a tool to evaluate the effectiveness of existing photo- sharing practices.
• To popularise the effort, usual promotional media like physical and online signs/ displays apart, library may use social media marketing platforms like blogs, Facebook, Twitter, etc., and increase awareness of photo-sharing tools.
• Imparting technology training may develop necessary knowledge; improve skill, and change the attitude and mindset of library professionals to handle issues related to using this web-based powered-tools and repurpose existing accessibility settings.
• To provide quick link to photo-sharing site from anywhere in the web, a library may use add-ons / plug-ins to embed image sharing tools.
• Photo-sharing site may be implemented to satisfy multiple approach options of users. A section of users use photo-sharing site to have a glimpse of the newly arrived documents, highlights of catalogue, rare books, etc. Some others may use it to find images of historical importance with context. New users may find it attractive to pay
https://www.facebook.com/techinsider/videos/595046657360361/
+++++++++++++++++++++++++++++++
more on game consoles in this IMS blog