Tag: phishing
hacking threats
Protect Student Data
Six Ways to Protect Student Data and Prevent Cyberattacks
By Ricky Doyle Dec 10, 2018
https://www.edsurge.com/news/2018-12-10-six-ways-to-protect-student-data-and-prevent-cyberattacks
School administrators and IT staff can be super-vigilant, but the hackers are getting better and better at sneaking through security.
the most common cybersecurity threats, and how can school staff avoid them?
Eavesdropping / Man-in-the-Middle (MiTM) Attacks
What they are: It’s likely that you sometimes use a school laptop or mobile device to gain internet access via Wi-Fi networks in public places like coffee shops or airports. If so, be aware that there may be hackers eavesdropping to try and gain entry to any two-party exchange you make so they can filter and steal data.
How to avoid them: Always use a school-verified SIM card, dongle or VPN(virtual private network) to access the internet in public places.
Social Engineering Attacks
According to Verizon’s 2018 Breach Investigations report, 92 percent of malware is delivered via email, often referred to as social engineering attacks. The aim is to interact with the user and influence and manipulate their actions to gain access to systems and install harmful software. Malware uses various guises. Here are some of the most common:
1. Phishing emails
2. Baiting attacks
3. Quid pro quo requests
4. Pretexting attacks
5. Contact with a ‘compromised’ website
Malware, Phishing, Hacking, Ransomware
Keeping Safe in a Digital World
How Not to be Hacked
Malware, Phishing, Hacking, Ransomware – oh my! Learn about the threats to you, your users and your library. During this session, we will explore the threats to online security and discuss solutions that can be implemented at any level. Most importantly, we will look at how we can educate our users on current threats and safety
Date: December 5th, 10AM
Presenter: Diana Silveira
Webinar December 5, 2017 10 AM
- create policies. e.g. changing psw routinely
- USB blockers for public computers (public libraries). like skimmers on gas stations
- do not use admin passwords
- software and firmware updates.
- policy for leaving employees
- HTTP vs HTTPS
- Cybersecurity KNowledge Quiz Pew research Center
http://www.pewinternet.org/quiz/cybersecurity-knowledge/
diana@novarelibrary.com
facebook.com/novarelibrary
twitter @Novarelibrary
+++++++++++
more on hacking in this IMS blog
https://blog.stcloudstate.edu/ims?s=hacker
fake emails
Why everyone still falls for fake emails
By Richard Matthews Jul 31, 2017
https://gcn.com/articles/2017/07/31/why-fake-emails-still-work.aspx
Phishing is likely to get only more sophisticated.
Based on my experience in Tallinn, we will see companies become more transparent in how they deal with cyber attacks. After a massive cyber attack in 2007, for example, the Estonian government reacted in the right way.
+++++++++++++++++++++
more on phishing in this IMS blog
https://blog.stcloudstate.edu/ims?s=phishing+
K12 cyber incidents
K–12 Cyber Incidents Have Been Increasing in 2017
The creator of a national K–12 Cyber Incident Map warns that schools should act now, not later, to bolster their security.
By Richard Chang 06/08/17
https://thejournal.com/articles/2017/06/08/k12-cyber-incidents-have-been-increasing-in-2017.aspx
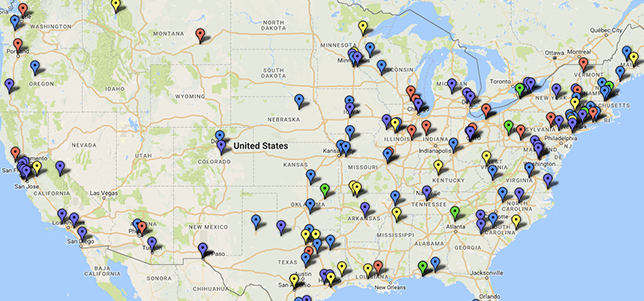
K–12 Cyber Incident Map , Doug Levin, president of Ed Tech Strategies
Levin has been tracking the publicly disclosed K–12 incidents on a color-coded map on his website, edtechstrategies.com. His sources include media reports, DataBreaches.net and the Privacy Rights Clearinghouse.
In a post published this week on the newly revamped Ferpa Sherpa education privacy site, Levin argues that not only have schools been “experiencing an increasing number of cyber incidents,” but “the range of cyber threats affecting schools appears to be diverse and shifting over time.”
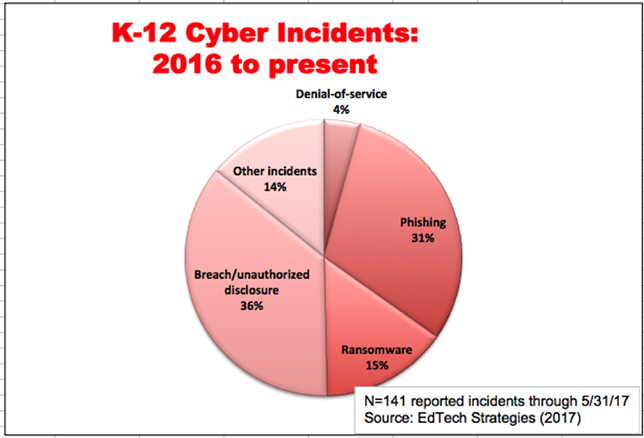
concrete steps schools can take to improve their security, such as:
- Use special software or hardware to protect data;
- Create better password and authorization policies;
- Use secondary authentication methods;
- Train school staff, particularly about phishing and downloading of unfamiliar files; and
- Hire more staff with IT security expertise.
++++++++++++++++++++
more on cyber security in this IMS blog
https://blog.stcloudstate.edu/ims?s=cybersecurity
phishing
Sneaky Exploit Allows Phishing Attacks From Sites That Look Secure
Lily Hay Newman Date of Publication: 04.18.17.
https://www.wired.com/2017/04/sneaky-exploit-allows-phishing-attacks-sites-look-secure/?mbid=synd_digg
You know by now to check your browser while visiting a site to be sure it sports the little green padlock indicating TLS encryption. https://en.wikipedia.org/wiki/Transport_Layer_Security
+++++++++++++
more on phishing in this IMS blog
https://blog.stcloudstate.edu/ims?s=phishing