Archive of ‘information technology’ category
My note:
I listened to the report in my car yesterday. It is another sober reminder for being proactive rather then reactive (or punitive). We must work toward digital literacy and go beyond that comfortably numb stage of information literacy.
An Experiment Shows How Quickly The Internet Of Things Can Be Hacked
http://www.npr.org/sections/alltechconsidered/2016/11/01/500253637/an-experiment-shows-how-quickly-the-internet-of-things-can-be-hacked
We have basic security in place in modern devices that screen out the most obvious attacks. Really getting phished, if you will, is more of a problem where you are tricked in surrendering your password or username to a common service. If you plug in your webcam into your router or to your Wi-Fi, you’re relatively safe.
I think the biggest security concern for folks at home would be if their router actually is old, it might have an easily guessed password that someone could gain control. Most modern devices don’t have that problem, but that certainly is a concern for older devices.
+++++++++++
more on cybersecurity in this blog:
https://blog.stcloudstate.edu/ims?s=cybersecurity
Google Researchers Create AI That Builds Its Own Encryption
BY TOM BRANT OCTOBER 28, 2016 04:45PM EST
http://www.pcmag.com/news/349154/google-researchers-create-ai-that-builds-its-own-encryption
Alice and Bob have figured out a way to have a conversation without Eve being able to overhear, no matter how hard she tries.
They’re artificial intelligence algorithms created by Google engineers, and their ability to create an encryption protocol that Eve (also an AI algorithm) can’t hack is being hailed as an important advance in machine learning and cryptography.
Martin Abadi and David G. Andersen, explained in a paper published this week that their experiment is intended to find out if neural networks—the building blocks of AI—can learn to communicate secretly.
As the Abadi and Anderson wrote, “instead of training each of Alice and Bob separately to implement some known cryptosystem, we train Alice and Bob jointly to communicate successfully and to defeat Eve without a pre-specified notion of what cryptosystem they may discover for this purpose.”
same in German
Googles AI entwickelt eigenständig Verschlüsselung
Google-Forscher Martin Abadi und David G. Andersen des Deep-Learning-Projekts “Google Brain” eine neue Verschlüsselungsmethode entwickelt beziehungsweise entwickeln lassen. Die Forscher haben verschiedene neurale Netze damit beauftragt, eine abhörsichere Kommunikation aufzustellen.
++++++++++++++++
more on AI in this IMS blog:
https://blog.stcloudstate.edu/ims?s=artificial+intelligence
Google Arts & Culture
https://www.google.com/culturalinstitute/beta/
Android App:
https://play.google.com/store/apps/details?id=com.google.android.apps.cultural&referrer=utm_source%3Dstella%26utm_medium%3Dhome-header
iOS App:
https://itunes.apple.com/app/arts-culture/id1050970557
++++++++++++++++++
more on virtual tours of museums in this IMS blog:
https://blog.stcloudstate.edu/ims?s=museum
Zcash (ZEC), the new digital currency lauded for its privacy features, is launching today amidst some massive hype. But until enough tokens become available on exchanges, Zcash enthusiasts are poised to acquire their ZEC first-hand by mining for it, either by setting up a home rig or by signing up for a cloud mining contract.
https://plus.google.com/+PatrickUlrich/posts/JEKNvhvwUHZ
++++++++++++++++++++++++++
more on bitcoin and digital currency in this IMS blog:
https://blog.stcloudstate.edu/ims?s=bitcoin
An excellent example of practical approach to a real digital storytelling case:
https://plus.google.com/+GeorgeCohn/posts/XfaXtgp5amA
++++++++++++++++++++
more on digital storytelling in this IMS blog:
https://blog.stcloudstate.edu/ims?s=digital+storytelling
Twitter is shutting down Vine

+++++++++++++++++++++++
More on Vine in this IMS blog:
https://blog.stcloudstate.edu/ims?s=vine
Mark your calendars:
second Arduino meeting
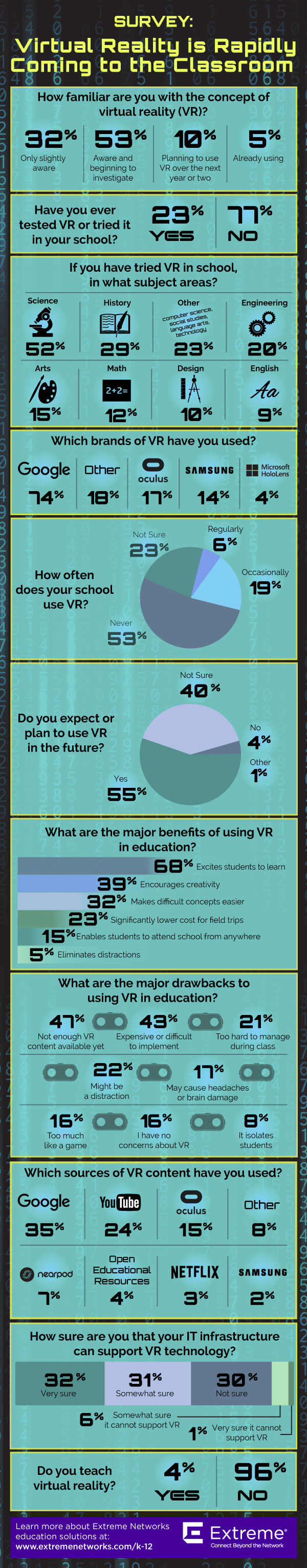
5 ways virtual reality is being used in education right now
By Meris Stansbury
1. For new research: using a state-of-the-art “haptic” floor of aeronautic metal that vibrates and moves to stimulate the physical world for research on how VR has the potential to change the way users feel and behave. There may also be implications for confronting racism, sexism, and aiding in
empathy and humanitarian efforts, says Bailenson.
2. For coding and 3D design:
According to Bob Nilsson, director of Vertical Solutions Marketing for Extreme Networking, the University of Maryland, College Park, now offers a class on virtual reality that gives students the opportunity to design their own interactive world, work with 3D audio and experiment with immersive technology through a combination of hands-on learning and case studies. Also, the University of Georgia is offering similar classes where students design and explore applications for VR. Conrad Tucker, an assistant professor of engineering at Pennsylvania State University, has received funding to build a virtual engineering lab where students hold, rotate, and fit together virtual parts as they would with their real hands.
3. For anatomy and dissection: Said one Extreme Networks survey respondent, “Our students have been developing a VR model of a cow’s anatomy for dissection and study. You have the ability to drill down to the circulatory system, brain, muscle, skeleton, etc. Our applied tech program is using VR in conjunction with Autocad for models of projects they design.”
4. For engagement: A whopping 68 percent of survey respondents said the major benefit of using VR in education is to excite students about the subject matter. 39 percent said it’s great for encouraging creativity.
5. For field trips: Google has eliminated restrictions on Expeditions, their VR field trips program. Google Expeditions was cited in the survey as one of the most popular sources of VR content, but with the complaint that it was a restricted program.
comment:
·
Virtual reality may have its place, but until traditional education moves away from their 20th century teaching methodology and replaces it with educationally innovative, 21st century learning methodology, within a blended and flipped learning environment, virtual reality is currently, much ado about nothing.
Unless any new application is educationally innovative and directly and measurably contributes to effective, efficient, consistent, affordable, relevant advanced student success outcomes for ALL students, future innovations must wait for current innovations to be implemented.
This process of appriate choice and appropriate implemention must start at the top and be beta tested for measured student success before its rolled out system wide.
+++++++++++++++
more on VR in this IMS blog
https://blog.stcloudstate.edu/ims?s=virtual+reality
Save
Internet pioneer dies at 102
https://fcw.com/blogs/fcw-insider/2016/10/beranek-dies-102-darpanet.aspx
Leo Berane, native of Solon, Iowa, passed away Oct. 10 at the age of 10.
The same year that Neil Armstrong first walked on the moon and the Beatles gave their last live performance, the ARPANET was born.
“I never dreamed the internet would come into such widespread use, because the first users of the Arpanet were large mainframe computer owners,” said Beranek in the New York Times interview.
++++++++++++++
more on Internet history in this IMS blog:
https://blog.stcloudstate.edu/ims?s=internet+history
Hayden calls Russian email hack ‘honorable state espionage’
By Matt Leonard Oct 18, 2016
https://fcw.com/articles/2016/10/18/hayden-email-espionage.aspx?
The Department of Homeland Security and the Office of the Director of National Intelligence issued a joint statement earlier this month that condemned Russia for the attacks.
“Do not drop this in the cyber problem box, drop this in the Russia problem box,” Hayden suggested, saying the focus should be on the actor, not the means. “And by the way, that Russian problem box needs a bigger box, there’s a lot of stuff going on.”
Though there are aspects of cybersecurity that only government can handle, most of it will be driven by the private industry, Hayden said. Government can help the private sector by getting out of the way — removing liability, enabling legal protections, sharing information and redoing the classification system.
And since the government too depends on the private sector for security innovation, Hayden said he sides with Apple regarding whether the company should have to create a back door for the FBI to bypass iPhone encryption.
+++++++++++++++++
more on surveillance, government in this IMS blog:
https://blog.stcloudstate.edu/ims?s=surveillance

