Searching for "library"
Privacy & Security in Today’s Library by Amigos Library Services
From: Jodie Borgerding [mailto:Borgerding@amigos.org]
Sent: Wednesday, July 05, 2017 3:07 PM
To: Miltenoff, Plamen <pmiltenoff@stcloudstate.edu>
Cc: Nicole Walsh <WALSH@AMIGOS.ORG>
Subject: Proposal Submission for Privacy & Security Conference
Hi Plamen,
Thank you for your recent presentation proposal for the online conference, Privacy & Security in Today’s Library, presented by Amigos Library Services. Your proposal, The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party,” has been accepted. I just wanted to confirm that you are still available to present on September 21, 2017 and if you have a time preference for your presentation (11 am, 12 pm, or 2 pm Central). If you are no longer able to participate, please let me know.
Nicole will be touch with you shortly with additional details and a speaker’s agreement.
Please let me know if you have any questions.
Thanks!
___________________
Jodie Borgerding Consulting & Education Services Manager Amigos Library Services 1190 Meramec Station Road, Suite 207 | Ballwin, MO 63021-6902 800-843-8482 x2897 | 972-340-2897(direct) http://www.amigos.org | borgerding@amigos.org
+++++++++++++++++
Bio
Dr. Plamen Miltenoff is an Information Specialist and Professor at St. Cloud State University. His education includes several graduate degrees in history and Library and Information Science and terminal degrees in education and psychology.
His professional interests encompass social media, multimedia, Web development and design, gaming and gamification, and learning environments (LEs).
Dr. Miltenoff organized and taught classes such as LIB 290 “Social Media in Global Context” (http://web.stcloudstate.edu/pmiltenoff/lib290/) and LIB 490/590 “Digital Storytelling” (http://web.stcloudstate.edu/pmiltenoff/lib490/) where issues of privacy and security are discussed.
Twitter handle @SCSUtechinstruc
Facebook page: https://www.facebook.com/InforMediaServices/
The virtuality of privacy and security on the modern campus:
The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party software” teaching and learning
Abstract/Summary of Your Proposed Session
The virtualization reality changes rapidly all aspects of learning and teaching: from equipment to methodology, just when faculty have finalized their syllabus, they have to start a new, if they want to keep abreast with content changes and upgrades and engagement of a very different student fabric – Millennials.
Mainframes are replaced by microcomputers, microcomputers by smart phones and tablets, hard drives by cloud storage and wearables by IoT. The pace of hardware, software and application upgrade is becoming unbearable for students and faculty. Content creation and methodology becomes useless by the speed of becoming obsolete. In such environment, faculty students and IT staff barely can devote time and energy to deal with the rapidly increasing vulnerability connected with privacy and security.
In an effort to streamline ever-becoming-scarce resources, campus IT “standardizes” campus use of applications. Those are the applications, which IT chooses to troubleshoot campus-wide. Those are the applications recommended to faculty and students to use.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal, attention on campuses is drown to the fact that cyberattacks shift now from mobile devices to IoT and campus often are struggling even with their capability to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party application might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
Abstract
The pace of changes in teaching and learning is becoming impossible to sustain: equipment evolves in accelerated pace, the methodology of teaching and learning cannot catch up with the equipment changes and atop, there are constant content updates. In an even-shrinking budget, faculty, students and IT staff barely can address the issues above, less time and energy left to address the increasing concerns about privacy and security.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal (https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/), attention on campuses is drawn to the fact of cyberattacks shifting from mobile devices to IoT but campus still struggling to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party applications might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/
Anything else you would like to add
3 take-aways from this session:
- Discuss and form an opinion about the education-pertinent issues of privacy and security from the broad campus perspective, versus the narrow library one
- Discuss and form an opinion about the role of the library on campus in terms of the greater issues of privacy and security
Re-examine the thin red line of the balance between standardization and innovation; between the need for security and privacy protection a
++++++++++++++
presentation:
https://www.slideshare.net/aidemoreto/the-virtuality-of-privacy-and-security-on-the
chat – slide 4, privacy. please take 2 min and share your definition of privacy on campus. Does it differ between faculty and students? what are the main characteristics to determine privacy
chat – slide 5, security. please take 2 min and share your definition of security on campus regarding electronic activities. Who’s responsibility is security? IT issue [only]?
poles: slide 6, technology unsupported by campus IT, is it worth considering? 1. i am a great believer in my freedom of choice 2. I firmly follow rules and this applies to the use of computer tools and applications 3. Whatever…
chat – slide 6, why third party applications? pros and cons. E.g. pros – familiarity with third party versus campus-required
pole, slide 6, appsmashing. App smashing is the ability to combine mobile apps in your teaching process. How do you feel about it? 1. The force is with us 2. Nonsense…
pole slide 7 third party apps and the comfort of faculty. How do you see the freedom of using third party apps? 1. All I want, thank you 2. I would rather follow the rules 3. Indifference is my middle name
pole slide 8 Technology standardization? 1. yes, 2. no, 3. indifferent
chat slide 9 if the two major issues colliding in this instance are: standardization versus third party and they have impact on privacy and security, how would you argue for the one or the other?
++++++++++++++++
notes from the conference
Speaker: Dr. Steve Albrecht – drsteve@drstevealbrecht.com
Follow @DrSteveAlbrecht
Dr. Steve Albrecht, author of Library Security: Better Communication, Safer Facilities, manages a training, coaching, and management consulting firm, using a dedicated and experienced team of subcontractor specialists. He is internationally known for his consulting and training work in workplace violence prevention training programs, school violence prevention, and high-risk human resources. Dr. Albrecht provides HR consulting, site security assessments, coaching, and training workshops in supervisory improvement, workplace violence prevention, harassment prevention, drug and alcohol awareness, team building, and more. He holds a B.A. in English, B.S. in Psychology, M.A. in Security Management, and a doctoral degree in Business Administration (D.B.A.). He has been a trainer for over 26 years and is a certified Professional in Human Resources (PHR), a Certified Protection Professional (CPP), a Board Certified Coach (BCC), and a Certified Threat Manager (CTM).
Session Description: Libraries don’t always need to hire a consultant to review the level of facility security. Using a structured assessment process, librarians can create a report that will help to make their building, staff, and patrons safer.
Chris Markman, MSLIS, MSIT Public Services Librarian Worcester Public Library
https://mycourses.amigos.org/mod/url/view.php?id=19623
Measuring Library Vendor Cyber Security: Seven Easy Questions Every Librarian Can Ask
http://journal.code4lib.org/articles/11413
Bill Walker: http://www.amigos.org/innovating_metadata
+++++++++++++++
more on security in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=security
more on privacy in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=privacy
My note:
I pushed this idea four years ago (e.g. https://youtu.be/4vw0iID0huE) for the SCSU library and it was shut down
Rocking the Small Screen without Losing Your Mind
http://www.davidleeking.com/rocking-the-small-screen-without-losing-your-mind
++++++++++++++++++++++++++++++
More on videos in the library in this IMS blog
Developing a Website Content Strategy
Instructor: Shoshana Mayden, Dates: July 3-28, 2017
http://libraryjuiceacademy.com/049-content-strategy.php
Shoshana Mayden is a content strategist with the University of Arizona Libraries in Tucson, Arizona. She advises on issues related to website content and contributes to developing a content strategy across multiple channels for the library. She works with content managers and library stakeholders to re-write, re-think and re-organize content for the main library website, as well as develop workflows related to the lifecycle of content. She also a copy editor for Weave: the Journal of Library User Experience.
++++++++++++++++++++++++
Information Architecture: Designing Navigation for Library Websites
Instructor: Laura-Edythe Coleman
http://libraryjuiceacademy.com/046-designing-navigation.php
Information Architecture is an essential component of user-centered design of information spaces, especially websites. Website navigation is a key design device to help users search and browse library websites and information systems. The design of Website navigation can be simple or complex, flat or deep. In all cases, website navigation should take into account information architecture (IA) best practices, common user tasks in the library domain, user research, analytics and information seeking models.
Laura-Edythe Coleman is a Museum Informaticist: her focus is on the point of convergence for museums, information, people, and technology. Knowing that societies need museums for creating and sustaining cultural memory, she strives to help communities co-create heritage collections with museums. She holds a PhD in Information Science, a Masters of Library and Information Science and a Bachelors of Fine Arts. She can be reached via Twitter: @lauraedythe, website: http://www.lauraedythe.com, or by email lauraedythecoleman@gmail.com
+++++++++++++++++++++++++
+++++++++++++++++++++
+++++++++++++++++
more on Libary web site in this IMS blog
https://www.lib.umich.edu/blog-tags/web-content-strategy
https://blog.stcloudstate.edu/ims?s=library+web+page
Bornett, C. C. (2016). Leseförderung digital genial: WieTablets die Bibliothekspädagogik verändern / Tipps nicht nur für Bilderbuch-Apps. (German). Bub: Forum Bibliothek Und Information, 68(10), 606-608.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d118913547%26site%3dehost-live%26scope%3dsite
Šorgo, A., Bartol, T., Dolničar, D., & Podgornik, B. B. (2017). Attributes of digital natives as predictors of information literacy in higher education. British Journal Of Educational Technology, 48(3), 749-767. doi:10.1111/bjet.12451 http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d122273174%26site%3dehost-live%26scope%3dsite
(PDF available through ILL)
Biology, IT faculty Maribor, Slovenia. None of them is a librarian
Correlation and regression analysis based on survey data revealed that the attributes of digital natives are poor predictors of IL. information and communication technologies (ICT) experiences expressed as the sum of the use of different applications do not necessarily contribute to IL; some applications have a positive and some a negative effect; personal ownership of smartphones, portable computers and desktop computers has no direct effect on IL, while ownership of a tablet computer is actually a negative predictor; personal ownership of ICT devices has an impact on ICT experiences and Internet confidence, and, therefore, an indirect impact on IL; and ICT-rich university courses (if not designed to cultivate IL) have only a marginal impact on IL, although they may have some impact on ICT experiences and Internet confidence. The overall conclusion is that digital natives are not necessarily information literate, and that IL should be promoted with hands-on and minds-on courses based on IL standards.
Sharman, A. (2014). Roving Librarian: The Suitability of Tablets in Providing Personalized Help Outside of the Traditional Library. New Review Of Academic Librarianship, 20(2), 185-203. doi:10.1080/13614533.2014.914959
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d96764510%26site%3dehost-live%26scope%3dsite
McRae, L. l. (2015). TEACHING IN AN AGE OF UBIQUITOUS COMPUTING: A DECELERATED CURRICULUM. Digital Culture & Education, 7131-145.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d110123216%26site%3dehost-live%26scope%3dsite
+++++++++++++++++
more on mobile devices in the library in this IMS blog
https://blog.stcloudstate.edu/ims?s=mobile+devices+library
Survey Highlights Digitization’s Impact on Campus Libraries
By David Raths 05/22/17
https://campustechnology.com/articles/2017/05/22/survey-highlights-digitizations-impact-on-campus-libraries.aspx
nonprofit Ithaka S+R. The study, Ithaka S+R Library Survey 2016, highlighted a number of challenges facing library directors in an era of increased digitization. Future Trends Forum video chat May 19 hosted by Bryan Alexander.
Alexander zeroed in on the finding that library directors feel increasingly less valued by supervisors such as chief academic officers.
Not surprisingly, the survey illustrates a broad shift toward electronic resources, Wolff-Eisenberg noted, with an increasing number of libraries developing policies for de-accessioning print materials that are also available digitally.
library directors are increasingly recognizing that discovery does not always happen in the library. Compared to the 2013 survey results, fewer library directors believe that it is important that the library is seen by its users as the first place that they go to discover content, and fewer believe that the library is always the best place for researchers at their institution to start their research.
There is also a substantial gap between how faculty members and library directors perceive the library’s contribution in supporting student learning. Both tend to agree that students have poor research skills, Wolff-Eisenberg noted. The faculty members see it as more of a problem, but they are less likely than library directors to see librarians contributing to student learning by helping them to develop research skills
The positions for which respondents anticipate the most growth in the next five years are related to instructional design (my note: this is IMS), information literacy and specialized faculty research support involving digital humanities, geographical information systems (GIS) and data management.
++++++++++++++++++++++
more on digitization in academic libraries in this IMS blog
https://blog.stcloudstate.edu/ims?s=digitization+library
6 Ways to Feed Innovation in Your Library
04/19/17 Dian Schaffhauser
https://campustechnology.com/Articles/2017/04/19/6-Ways-to-Feed-Innovation-in-Your-Library.aspx
2014 Stanford Prize for Innovation in Research Libraries
Rising Star Award\
1) Play “Hopscotch” on Campus
a 360-degree projection space, getting ready to open a virtual reality studio with “room-scale” VR sporting Oculus Rift and Vive gear, the idea of the “graduate students’ commons,” with access limited to those students as well as faculty
2) Sometimes Innovation Just Comes Knocking
3) Hire People With New Ideas
Rather than innovation being directed from the top down, it bubbles from the bottom up.
4) Plan on “Making” Your Own Resources
5) Make Tech as Accessible as Possible
Another intention is to bring different disciplines together in the hopes of sparking new ideas.
6) Learn How to Tell the Story
+++++++++++++++++
more on academic library in this IMS blog
https://blog.stcloudstate.edu/ims?s=academic+library
The Library in the Life of the User. Engaging with People Where They Live and Learn
p. 18
Library staff
The roles of librarians change with changes in user needs and demands and the technology employed. A survey conducted for Research Libraries UK found skill gaps in nine key areas in which subject librarians could be supporting researchers’ needs. Even though many librarians may want to hire new staff with these skills, a survey found that the reality for most will be training existing staff.
Definitions of library services will change. We need to grow the ways users can engage with whatever they value from libraries, whether papyrus rolls, maker spaces or data management instruction.
p. 19
What is the Unique Selling Point (USP) of libraries vis-à-vis other information service providers?
p. 21
Librarians should measure the effectiveness of services based on the users’ perceptions of success. Librarians also should move beyond surveys of how library space is being used and should conduct structured observations and interviews with the people using the space. It is not enough to know that the various spaces, whether physical or virtual, are busy. Librarians need to understand when and how the spaces are being used.
p. 33 What is Enough? Satisficing Information Needs
Role theory explains that: “When people occupy social positions their behavior is determined mainly by what is expected of that position rather than by their own individual characteristics” (Abercrombie et al., 1994, p. 360).
Rational choice theory is based on the premise that complex social behavior can be understood in terms of elementary individual actions because individual action is the elementary unit of social life. Rational choice theory posits that individuals choose or prefer what is best to achieve their objectives or pursue their interests, acting in their self-interest (Green, 2002). Stated another way, “When faced with several courses of action, people usually do what they believe is likely to have the best overall outcome” (Scott, 2000).
When individuals satisfice, they compare the benefits of obtaining “more information” against the additional cost and effort of continuing to search (Schmid, 2004)
p. 38
This paper examines the theoretical concepts—role theory, rational choice, and satisficing—by attempting to explain the parameters within which users navigate the complex information-rich environment and determine what and how much information will meet their needs.
p. 39
The information-seeking and -searching research that explicitly addresses the topic of “what is good enough” is scant, though several studies make oblique references to the stopping stage, or to the shifting of directions for want of adequate information. Kraft and Lee (1979, p. 50) propose three stopping rules:
1. The satiation rule, “where the scan is terminated only when the user becomes satiated by finding all the desired number of relevant documents”;
2. The disgust rule, which “allows the scan to be terminated only when the user becomes disgusted by having to examine too many irrelevant documents”; and
3. The combination rule, “which allows the user to be seen as stopping the scan if he/she is satiated by finding the desired number of relevant documents or disgusted by having to examine too many irrelevant documents, whichever comes first.”
p. 42
Ellis characterizes six different types of information activities: starting, chaining, browsing, differentiating, monitoring and extracting. He emphasizes the information- seeking activities, rather than the nature of the problems or criteria used for determining when to stop the information search process. In a subsequent article, Ellis (1997) observes that even in the final stages of writing, individuals may continue the search for information in an attempt to answer unresolved questions or to look for new literature.
p. 43
Undergraduate and graduate students
Situations creating the need to look for information (meeting assignment requirements):
• Writing research reports; and
• Preparing presentations.
Criteria used for stopping the information search (fulfilling assignment requirements):
1. Quantitative criteria:
— Required number of citations was gathered;
— Required number of pages was reached;
— All the research questions were answered; and
— Time available for preparing.
2. Qualitative criteria:
— Accuracy of information;
— Same information repeated in several sources;
— Sufficient information was gathered; and
— Concept understood.
Criteria used for stopping the information search (fulfilling assignment requirements):
1. Quantitative criteria:
— Required number of citations was gathered;
— Required number of pages was reached;
— All the research questions were answered; and
— Time available for preparing.
2. Qualitative criteria:
— Accuracy of information;
— Same information repeated in several sources;
— Sufficient information was gathered; and
— Concept understood.
p. 44
Faculty
Situations creating the need to look for information (meeting teaching needs):
• Preparing lectures and presentations;
• Delivering lectures and presentations;
• Designing and conducting workshops;
• Meeting scholarly and research needs; and
• Writing journal articles, books and grant proposals.
Criteria used for stopping the information search (fulfilling teaching needs):
1. Quantitative criteria:
— Time available for: preparing lectures and presentations; delivering lectures
— And presentations; and designing and conducting workshops; and
— Fulfilling scholarly and research needs.
2. Qualitative criteria:
— Every possible synonym and every combination were searched;
— Representative sample of research was identified;
— Current or cutting-edge research was found;
— Same information was repeated;
— Exhaustive collection of information sources was discovered;
— Colleagues’ feedback was addressed;
— Journal reviewers’ comments were addressed; and
— Publisher’s requirements were met.
1. Quantitative criteria for stopping:
— Requirements are met;
— Time constraints are limited; and
— Coverage of material for publication is verified by colleagues or reviewers.
2. Qualitative criteria for stopping:
— Trustworthy information was located;
— A representative sample of sources was gathered;
— Current information was located;
— Cutting-edge material was located;
— Exhaustive search was performed; and
— Exhaustive collection of information sources was discovered.
p. 53
“Screenagers” and Live Chat Reference: Living Up to the Promise
p. 81
Sense-Making and Synchronicity: Information-Seeking Behaviors of Millennials and Baby Boomers
p. 84 Millennials specific generational features pertinent to libraries and information-seeking include the following:
Immediacy. Collaboration. Experiential learning. Visual orientation. Results orientation. Confidence.
Rushkoff (1996) described the non-linearity of the thinking patterns of those he terms “children of chaos,” coining the term “screenagers” to describe those who grew up surrounded by television and computers (p. 3).
p. 85
Rational choice theory describes a purposive action whereby individuals judge the costs and benefits of achieving a desired goal (Allingham 1999; Cook and Levi 1990; Coleman and Fararo 1992). Humans, as rational actors, are capable of recognizing and desiring a certain outcome, and of taking action to achieve it. This suggests that information seekers rationally evaluate the benefits of information’s usefulness and credibility, versus the costs in time and effort to find and access it.
Role theory offers a person-in-context framework within the information-seeking situation which situates behaviors in the context of a social system (Mead 1934; Marks 1996). Abercrombie, et al. (1994, p. 360) state, “When people occupy social positions their behavior is determined mainly by what is expected of that position rather than by their own individual characteristics.” Thus the roles of information-seekers in the academic environment influence the expectations for performance and outcomes. For example, faculty would be expected to look for information differently than undergraduate students. Faculty members are considered researchers and experts in their disciplines, while undergraduate students are novices and protégés, roles that place them differently within the organizational structure of the academy (Blumer, 2004; Biddle, 1979; Mead, 1934; Marks, 1996; Marks, 1977).
+++++++++++++++++
more on research in this IMS blog
https://blog.stcloudstate.edu/ims?s=research
NMC Horizon Report > 2017 Library Edition
http://www.nmc.org/publication/nmc-horizon-report-2017-library-edition/
PDF file 2017-nmc-horizon-report-library-EN-20ml00b
p. 26 Improving Digital Literacy
As social networking platforms proliferate and more interactions take place digitally, there are more opportunities for propagation of misinformation, copyright infringement, and privacy breaches.
p. 34 Embracing the need for radical change
40% of faculty report that their students ” rarely” interact with campus librarians.
Empathy as the Leader’s Path to Change | Leading From the Library, By Steven Bell on October 27, 2016, http://lj.libraryjournal.com/2016/10/opinion/leading-from-the-library/empathy-as-the-leaders-path-to-change-leading-from-the-library/
Empathy as a critical quality for leaders was popularized in Daniel Goleman’s work about emotional intelligence. It is also a core component of Karol Wasylyshyn’s formula for achieving remarkable leadership. Elizabeth Borges, a women’s leadership program organizer and leadership consultant, recommends a particular practice, cognitive empathy.
Leadership in disruptive times, James M. Matarazzo, Toby Pearlstein, First Published September 27, 2016, http://journals.sagepub.com/doi/full/10.1177/0340035216658911
What is library leadership? a library leader is defined as the individual who articulates a vision for the organization/task and is able to inspire support and action to achieve the vision. A manager, on the other hand, is the individual tasked with organizing and carrying out the day-to-day operational activities to achieve the vision.Work places are organized in hierarchical and in team structures. Managers are appointed to administer business units or organizations whereas leaders may emerge from all levels of the hierarchical structures. Within a volatile climate the need for strong leadership is essential.
Leaders are developed and educated within the working environment where they act and co-work with their partners and colleagues. Effective leadership complies with the mission and goals of the organization. Several assets distinguish qualitative leadership:
Mentoring. Motivation. Personal development and skills. Inspiration and collaboration. Engagement. Success and failure. Risk taking. Attributes of leaders.
Leaders require having creative minds in shaping strategies and solving problems. They are mentors for the staff, work hard and inspire them to do more with less and to start small and grow big. Staff need to be motivated to work at their optimum performance level. Leadership entails awareness of the responsibilities inherent to the roles of a leader. However, effective leadership requires the support of the upper management.
p. 36. Developments in Technology for Academic and Research Libraries
http://horizon.wiki.nmc.org/Horizon+Topics
- consumer technologies
- Digital strategies are not so much technologies as they are ways of using devices and software to enrich teaching, learning, research and information management, whether inside or outside the library. Effective Digital strategies can be used in both information and formal learning; what makes them interesting is that they transcended conventional ideas to create something that feels new, meaningful, and 21st century.
- enabling technologies
this group of technologies is where substantive technological innovation begins to be visible.
- Internet technologies.
- learning technologies
- social media technologies. could have been subsumed under the consumer technology category, but they have become so ever-present and so widely used in every part of society that they have been elevated to their own category. As well-established as social media is, it continues to evolve at a rapid pace, with new ideas, tools, and developments coming online constantly.
- Visualization technologies. from simple infographics to complex forms of visual data analysis. What they have in common is that they tap the brain’s inherent ability to rapidly process visual information, identify patterns, and sense order in complex situations. These technologies are a growing cluster of tools and processes for mining large data sets, exploring dynamic processes, and generally making the complex simple.

p. 38 Big Data
Big data has significant implications for academic libraries in their roles as facilitators and supporters of the research process. big data use in the form of digital humanities research. Libraries are increasingly seeking to recruit for positions such as research data librarians, data curation specialists, or data visualization specialists
p. 40 Digital Scholarship Technologies
digital humanities scholars are leveraging new tools to aid in their work. ubiquity of new forms of communication including social media, text analysis software such as Umigon is helping researchers gauge public sentiment. The tool aggregates and classifies tweets as negative, positive, or neutral.
p. 42 Library Services Platforms
Diversity of format and materials, in turn, required new approaches to content collection and curation that were unavailable in the incumbent integrated library systems (ILS), which are primarily designed for print materials. LSP is different from ILS in numerous ways. Conceptually, LSPs are modeled on the idea of software as a service (SaaS),which entails delivering software applications over the internet.
p. 44 Online Identity.
incorporated the management of digital footprints into their programming and resources
simplify the idea of digital footprint as“data about the data” that people are searching or using online. As resident champions for advancing digital literacy,304 academic and research libraries are well-positioned to guide the process of understanding and crafting online identities.
Libraries are becoming integral players in helping students understand how to create and manage their online identities. website includes a social media skills portal that enables students to view their digital presence through the lens in which others see them, and then learn how they compare to their peers.
p. 46 Artificial Intelligence
https://www.semanticscholar.org/
p. 48 IoT
beacons are another iteration of the IoT that libraries have adopted; these small wireless devices transmit a small package of data continuously so that when devices come into proximity of the beacon’s transmission, functions are triggered based on a related application.340 Aruba Bluetooth low-energy beacons to link digital resources to physical locations, guiding patrons to these resources through their custom navigation app and augmenting the user experience with location-based information, tutorials, and videos.
students and their computer science professor have partnered with Bavaria’s State Library to develop a library app that triggers supplementary information about its art collection or other points of interest as users explore the space
+++++++++++++++++++++++++++
more on Horizon Reports in this IMS blog
https://blog.stcloudstate.edu/ims?s=horizon+report
LibTechConf
http://libtechconf.org/2017schedule/
The Next Generation of Library Orientation: http://libtechconf.org/2017schedule/
Please have a link to the presentation: https://tinyurl.com/vr360lib
#LTC2017 #vrlib
Join us online, Thursday, March 16, 2:15PM via:
Adobe Connect archived recording: http://scsuconnect.stcloudstate.edu/p7qm3hg7u0h/
or via
Facebook Live: https://www.facebook.com/InforMediaServices/
++++++++++++++++++++
more on LibTech conferences:
https://blog.stcloudstate.edu/ims?s=library+technology+conference
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
notes from the conference
Keynote speaker: Lauren Di Monte http://sched.co/955P
Debating Data Science – a roundtable http://rhr.dukejournals.org/content/2017/127/133.abstract

Lauren
how data is produced, collected and analyzed. make accessible all kind of data and info
ask good q/s and find good answers, share finding in meaningful ways. this is where digital literacy overshadows information literacy and this the fact that SCSU library does not understand; besides teaching students how to find and evaluate data, I also teach them how to communicate effectively using electronic tools.
connecting people tools and resources and making it easier for everybody. building collaborative, open and interdisciplinary
robust data computational literates. developing workshops, project and events to practice new skills. to position the library as the interdisciplinary nexus
what are data: definition. items of information, facts, traces of content and form. higher level, conception discussion about data in terms of social effects: matadata capturing information about the world, social political and economic changes. move away the mystic conceptions about data. nothing objective about data.
the emergence of IoT – digital meets physical. cyber physical systems. smart objects driven by industry. . proliferation of sensor and device – smart devices.
what does privacy looks like ? what is netneutrality when IoT? library must restructure : collaborate across institutions about collections of data in opien and participatory ways. put IoT in the hands of make and break things (she is maker space aficionado)
make and break things hackathons – use cheap devices such as Arduino and Pi.
data literacy programs with higher level conception exploration; libraries empower the campus in data collection. data science norms, store and share data to existing repositories and even catalogs. commercial services to store and connect data, but very restrictive and this is why libraries must be involved.
linked data and dark data
linked data – draw connections around online data most of the data are locked. linked data uses metadata to link related information in ways computers can understand.
libraries take advantage of link data. link data opportunity for semantics, natural language processing etc. if hidden data is relative to our communities, it is a library responsibility to provide it. community data practitioners
dark data
massive data, which cannot be analyzed by relational processing. data not yield significant findings. might be valuable for researchers: one persons trash is another persons’ treasure. preserving data and providing access to info. collaborate with researchers across disciplines and assist decide what is worth keeping and what discarding and how to study.
rich learning experience working with lined and dark data enable fresh perspective and learning how to work with data architecture. data literacy programming.
open practices https://www.data.gov/
in context of data is different from open source and open projects. the social side of data science . advising researchers on navigation data, ethical compilations.
open science movement .https://cos.io/ pushing beyond licences and reframe, position ourselves as collaborators
analysis and publishing ; use tools that can be shared and include data, code and executable files.
reproducibility and contestability https://www.lib.ncsu.edu/events/series/summer-of-open-science
Python and Raspberry Pi. jupitor notebook server,
she is advocating for faculty not only being the leader but the DOERs of basic fucntions, which SCSU IT is rigorously fighting to keep for themselves. The sad part is that the rest of the nation is moving in this direction and SCSU continues to sink in an old 90ish campus structure of leaving IT as the gatekeeprs to functions now widely democratized.
public libraries: citizen science projects.
her undergrad is visual studies and her grad studies is interdisciplinary studies. only in the information school she got into science.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
social media for the library
http://sched.co/954Z
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Library Website Redesign: Turning Awful into Awesome
http://sched.co/953o dysfunctional committee
Here is the Facebook Live link to the session:
lib guides versus curation : https://blog.stcloudstate.edu/ims/2016/12/06/digital-curation/
crazyegg:
Putting it all together: a holistic approach to utilizing your library’s user data for making informed web design decisions (2016 conference)
In the age of Big Data, there is an abundance of free or cheap data sources available to libraries about their users’ behavior across the many components that make up their web presence. Data from vendors, data from Google Analytics or other third-party tracking software, and data from user testing are all things libraries have access to at little or no cost. However, just like many students can become overloaded when they do not know how to navigate the many information sources available to them, many libraries can become overloaded by the continuous stream of data pouring in from these sources. This session will aim to help librarians understand 1) what sorts of data their library already has (or easily could have) access to about how their users use their various web tools, 2) what that data can and cannot tell them, and 3) how to use the datasets they are collecting in a holistic manner to help them make design decisions. The presentation will feature examples from the presenters’ own experience of incorporating user data in decisions related to design the Bethel University Libraries’ web presence.
http://tinyurl.com/jbchapf

!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Making Something Out of Nothing: Building Digital Humanities Partnerships
Facebook Live https://www.facebook.com/InforMediaServices/videos/1136610906449405/
what is digital humanities?
3 questions to rotate the conversation around them
bit.ly/DHLibQ1
bit.ly/DHLibQ2
group discussions
silos, IT barrier, focusing on student success, retention, server space is cheap, if
promotion and tenure for faculty can include incentive to work with the librarian
being perceived as a “no” person
How can we can help one another build partnerships within and across institutions?
bit.ly/DHLibQ3
Midwest consortium for grants among liberal colleges to distribute support
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
badges CSS and Java Script generate links, which can be used for the course
server is external so it is independent from IT constrains.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
March 16
3d virtual picture of disastrous areas. unlock the digital information to be digitally accessible to all people who might be interested.
they opened the maps of Katmandu for the local community and they were coming up with the strategies to recover. democracy in action
http://werobotics.org/
mountain tsunami: http://www.natgeotv.com/uk/seconds-from-disaster/videos/mountain-tsunami
i can’t stop thinking that the keynote speaker efforts are mere follow up of what Naomi Klein explains in her Shock Doctrine: http://www.naomiklein.org/shock-doctrine: a government country seeks reasons to destroy another country or area and then NGOs from the same country go to remedy the disasters
A question from a librarian from the U about the use of drones. My note: why did the SCSU library have to give up its drone?
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
http://sched.co/953l
Building an Ebook Platform from Scratch: Are You Daft?
Douglas County Library model. too resource intensive to continue
Marmot Library Network
ILS integrated library system – shared with other counties, same sever for the entire consortium. they have a programmer, viewfind, open source, discovery player, he customized viewfind community to viewfind plus. instead of using the ILS public access catalogue, they are using the Vufind interface
Caiifa Enki. public library – single access collection. they purchase ebooks from the publisher and they are using also the viewfind interface. but not integrated with the library catalogs. Kansas public library went from OverDrive to Viewfind. CA State library is funding for the time being this effort.
publisher agreement needed
metadata is a big issue. it can come in any format – spreadsheet, HTML and need to be able to convert into MARC
Amigos is a consortium of schools, but also academic and public. small public library could not handle the spreadsheet
types of content – publisher will not understand issue, which clear for librarians
PDF and epub formats
purchase content –
title by title selection – academia is tired of selections. although it is intended to buy also collections
library – owned ( and shared collections)
host content from libraries – papers in academic lib, genealogy in pub lib.
options in license models .
e resource content. not only ebooks, after it is taken care of, add other types of digital objects.
instead of replicate, replacement of the commercial aggregators,
Amigos Shelf interface is the product of the presenter
instead of having a young reader collection as SCSU has on the third floor, an academic library is outsourcing through AMigos shelf ebooks for young readers
purchasing marketing was built from scratch on PhP. https://laravel.com/
Harper Collins is too cumbersome and the reason to avoid working with them.
security issues. some of the material sent over ftp and immediately moved to sftp
decisions – use of internal resources only, if now – amazon
programmer used for the pilot. contracted programmers. lack of the ability to see the large picture. eventually hired a full time person, instead of outsourcing. RDA compliant MARC.
ONIX, spreadsheet MARC.
Decision about who to start with : public or academic.
attempt to keep pricing down –
own agreement with the customers, separate from the agreement with the Publisher
current development: web-based online reading, shared-consortial collections and SIP2 authentication
new CIO closed the project.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Tutorials
http://bit.ly/LTC2017SVC
https://docs.google.com/presentation/d/1FnlTJVdu4KkvjB21NXp82zHCYwQfmwpzi_dlZp4AgYU/edit#slide=id.p
http://bit.ly/LTC2017tutorial2
https://youtu.be/3MhsVN8ff0c
30 Great Educational Web Tools for Librarians
http://www.educatorstechnology.com/2016/12/30-great-educational-web-tools-for.html
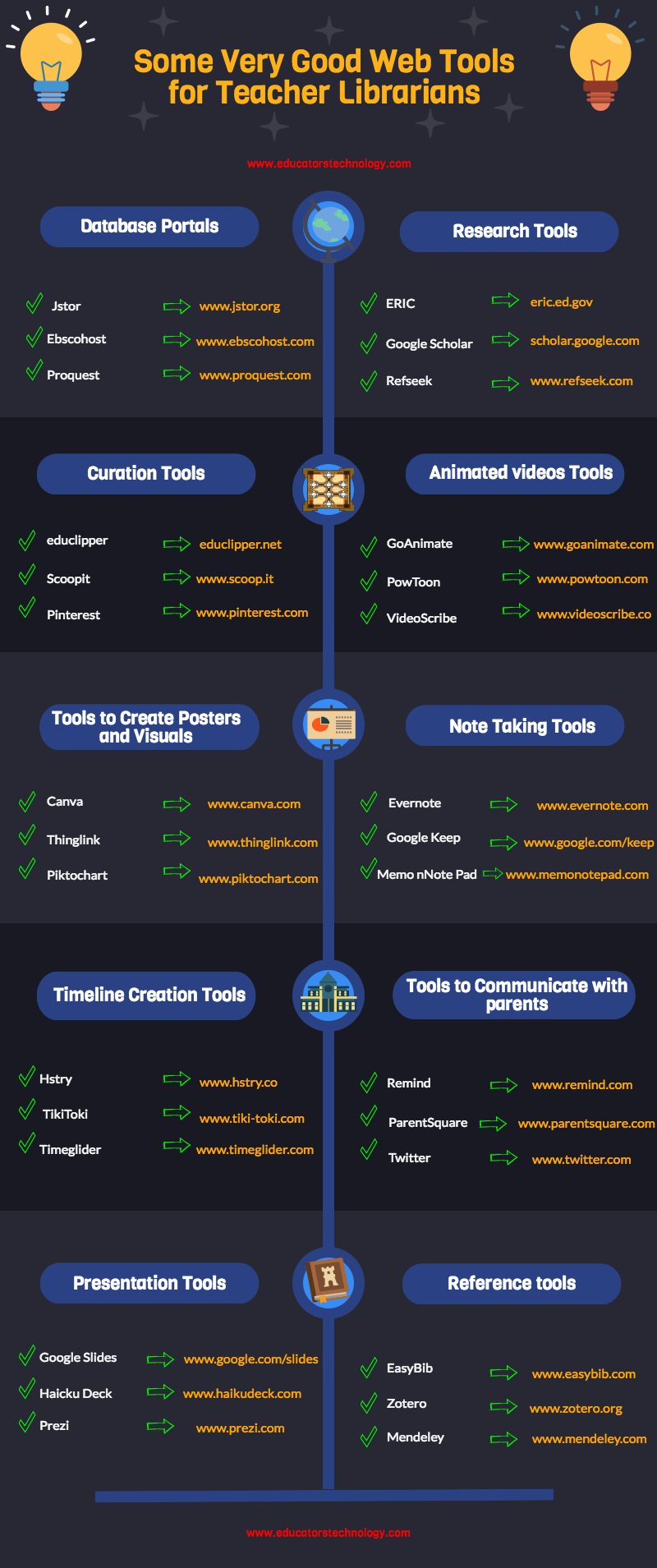
++++++++++++++++++++++
more about tools for library in this IMS blog
https://blog.stcloudstate.edu/ims?s=tools+library





