Susan Grajek and the 2016–2017 EDUCAUSE IT Issues Panel Tuesday, January 17, 2017http://er.educause.edu/articles/2017/1/top-10-it-issues-2017-foundations-for-student-successThe 2017 EDUCAUSE Top 10 IT Issues are all about student success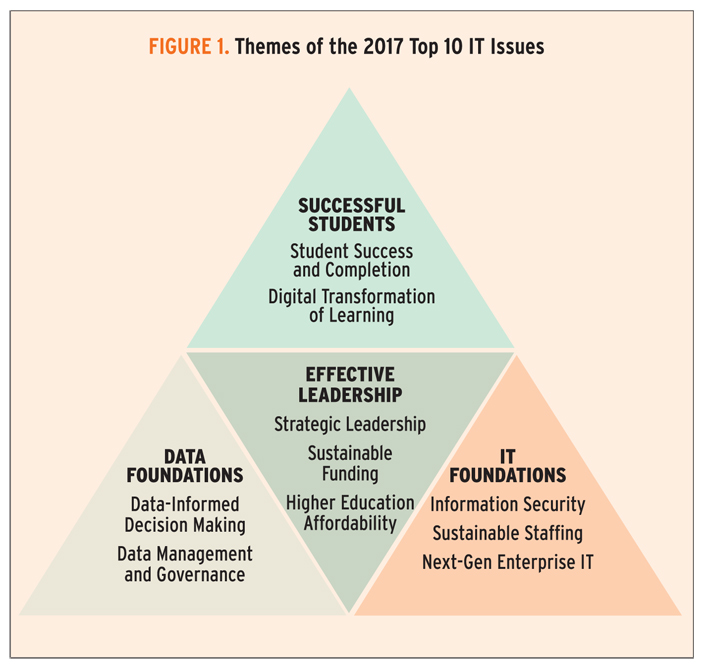
EDUCAUSE supports early adopters in this area through the Integrated Planning and Advising for Student Success (iPASS) grant challenge, a program in which EDUCAUSE helps develop models for the field by working closely with a small number of institutions that are pioneering iPASS systems.
Issue #1: Information Security
Developing a holistic, agile approach to reduce institutional exposure to information security threats
That program should encompass people, process, and technologies:
- Educate users
- Develop processes to identify and protect the most sensitive data
- Implement technologies to encrypt data and find and block advanced threats coming from outside the network via from any type of device
Who Outside the IT Department Should Care Most about This Issue?
- End-users, to understand how to avoid exposing their credentials
- Unit heads, to protect institutional data
- Senior leaders, to hold people accountable
- Institutional leadership, to endorse, fund, and advocate for good information security
Issue #2: Student Success and Completion
Effectively applying data and predictive analytics to improve student success and completion
Predictive analytics allows us to track trends, discover gaps and inefficiencies, and displace “best guess” scenarios based on implicitly developed stories about students.
Issue #3: Data-Informed Decision Making
Ensuring that business intelligence, reporting, and analytics are relevant, convenient, and used by administrators, faculty, and students
Higher education information systems generate vast amounts of data daily (including the classroom/LMS). This potentially rich source of information is underused. Even though most institutions have created reports, dashboards, and other distillations of data, these are not necessarily useful or used to inform strategic objectives such as student success or institutional efficiency.
Issue #4: Strategic Leadership
Repositioning or reinforcing the role of IT leadership as a strategic partner with institutional leadership
CIOs have two challenges in this regard. The first is getting to the table. Contemporary requirements for IT leaders position them well for strategic leadership.18 Those requirements include expertise in management and business practices, project portfolio management, negotiation, and change leadership. However, business-savvy CIOs can alienate some academics, particularly those opposed to administrators as leaders. Worse, not all CIOs are well-equipped for a position at the executive table.
Issue #5: Sustainable Funding
Developing IT funding models that sustain core services, support innovation, and facilitate growth
Two complications have deepened the IT funding challenge in recent years. The first is that information technology is now incontrovertibly core to the mission and function of colleges and universities. The second complication is that at most institutions, digital investments and technology refreshes have been funded with capital expenditures. Yet IT services and infrastructure are moving outside the institution, generally to the cloud, and cloud funding depends on ongoing expenditures rather than one-time investments.
Issue #6: Data Management and Governance
Improving the management of institutional data through data standards, integration, protection, and governance
Data management and governance is not an IT issue. It requires a broad, top-down approach because all departments need to buy in and agree. All stakeholders (data owners as well as IR, IT, and institutional leaders) must collaboratively develop a common set of data definitions and a common understanding of what data is needed, in what format, and for what purposes. This coordination, or governance, will enable constituents to communicate with confidence about the data (e.g., “the single version of truth”) and the standards (e.g., APLU, IPEDS, CDS) under which it is collected.
Institutions often choose to approach data management from three perspectives: (1) accuracy, (2) usability, and (3) privacy. The IT organization has a role to play in creating and maintaining data warehouses, integrating systems to facilitate data exchange, and maintaining standards for data privacy and security.
Issue #7: Higher Education Affordability
Prioritizing IT investments and resources in the context of increasing demand and limited resources
Uncoordinated, redundant expenditures supplant other needed investments, such as consistent classroom technology or dedicated information security staff. Planning needs to occur at the institutional or departmental level, but it also needs a place to coalesce and be assessed regionally, nationally, and in some cases, globally, because there isn’t enough money to do everything that institutional leaders, faculty, and others want or even need to do. Public systems are making some headway in sharing services, but for the most part, local optimization supersedes collaboration and compromise.
Issue #8: Sustainable Staffing
Ensuring adequate staffing capacity and staff retention as budgets shrink or remain flat and as external competition grows
As institutions become more dependent on their IT organizations, IT organizations are more dependent on the expertise and quality of their workforce. New hires need to be great hires, and great staff need to want to stay. Each new hire can change the culture and effectiveness of the IT organizations
Issue #9: Next-Gen Enterprise IT
Developing and implementing enterprise IT applications, architectures, and sourcing strategies to achieve agility, scalability, cost-effectiveness, and effective analytics
Buildings should outlive alumni; technology shouldn’t. IT leaders are examining core enterprise applications, including ERPs (traditionally, suites of financial, HR, and student information systems) and LMSs, for their ability to meet current and future needs.
Issue #10: Digital Transformation of Learning
Collaborating with faculty and academic leadership to apply technology to teaching and learning in ways that reflect innovations in pedagogy and the institutional mission
According to Michael Feldstein and Phil Hill, personalized learning applies technology to three processes: content (moving content delivery out of the classroom and allowing students to set their pace of learning); tutoring (allowing interactive feedback to both students and faculty); and contact time (enabling faculty to observe students’ work and coach them more).
+++++++++++++++++++++
more on IT in this IMS blog
https://blog.stcloudstate.edu/ims?s=information+technology