LEVERAGING HISTORY What Britain’s Decline and America’s Rise Can Tell Us about China’s Future
https://s3.amazonaws.com/files.cnas.org/documents/CNASReport-LeveragingHistory-final.pdf
Britain
Colonial interests compelled Great Britain to build a complex economic system that funneled resources and wealth to the home islands. Great Britain’s time as the central organizing great power came to a rapid end, with the United States filling that central role.
the United States can no longer uphold all its commitments to international laws and norms. Gaps in attention to historical American commitments have opened the door for competitor nations, including China, to challenge U.S. leadership at the margins.
p. 17 Does China have a strategic plan to replace the United States as the leader of the world? Some voices suggest that it does; however, it is important to note that they do not suggest that it is modeling its ascent upon the United States’ rise a century ago
++++++++++++++
more on history in this IMS blog
https://blog.stcloudstate.edu/ims?s=history
Tips Toward a Safe and Positive Social Media Experience
By Stephen Spengler 06/01/17
https://thejournal.com/articles/2017/06/01/tips-toward-a-safe-and-positive-social-media-experience.aspx
Family Online Safety Institute recommends that parents engage in “7 Steps to Good Digital Parenting”
1. Talk with your children.
2. Educate yourself.
3. Use parental controls. Check the safety controls on all of the Android and Apple devices that your family uses. On the iPhone, you can tap SETTINGS > GENERAL> RESTRICTIONS and you can create a password that allows you enable/disable apps and phone functions. On Android devices, you can turn on Google Play Parental Controls by going into the Google Play Store settings
parental monitoring software such as NetNanny, PhoneSherriff, Norton Family Premier and Qustodio.
4. Friend and follow your children on social media. Whether it’s musical.ly, Instagram or Twitter, chances are that your children use some form of social media. If you have not already, then create an account and get on their friends list.
5. Explore, share and celebrate.
6. Be a good digital role model.
7. Set ground rules and apply sanctions. Just like chore charts or family job lists, consider using a family social media or internet safety contract. These contracts establish ground rules for when devices are to be used; what they should and should not be doing on them; and to establish sanctions based on breaches of the family contract. A simple internet search for “family internet contract” or “family technology contract” will produce a wealth of available ideas and resources to help you implement rules and sanctions revolving around your family’s technology use. A good example of a social media contract for children can be found at imom.com/printable/social-media-contract-for-kids/.
Managing Your Digital Footprint
Your digital footprint, according to dictionary.com, is “one’s unique set of digital activities, actions, and communications that leave a data trace on the internet or on a computer or other digital device and can identify the particular user or device.” Digital footprints can be either passive or active. The passive digital footprint is created without your consent and is driven by the sites and apps that you visit. The data from a passive digital footprint could reveal one’s internet history, IP address, location and is all stored in files on your device without you knowing it. An active digital footprint is more easily managed by the user. Data from an active digital footprint shows social media postings, information sharing, online purchases and activity usage.
- Search for yourself online
- Check privacy settings.
- Use strong passwords
- Update software.
- Maintain your device.
- Think before you post
Keep These Apps on Your Radar
- Afterschool (minimum age 17) – The Afterschool App was rejected twice from the major app stores due to complaints from parents and educators. It is a well-known app that promotes cyberbullying, sexting, pornography and is filled with references to drugs and alcohol.
- Blue Whale (minimum age 10) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. It is a suicide challenge app that attempts to prod children into killing themselves.
- BurnBook (minimum age 18) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. It is a completely anonymous app for posting text, photos, and audio that promote rumors about other people. It is a notorious for cyberbullying
- Calculator% (minimum age 4) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. This is one of hundreds of “secret” calculator apps. This app is designed to help students hide photos and videos that they do not want their parents to see. This app looks and functions like a calculator, but students enter a “.”, a 4-digit passcode, and then a “.” again.
- KIK (minimum age 17) – This is a communications app that allows anyone to be contacted by anyone and it 100 percent bypasses the device’s contacts list.
- Yik Yak (minimum age 18) – This app is a location-based (most commonly schools) bulletin board app. It works anonymously with anyone pretending to be anyone they want. Many schools across the country have encountered cyberbullying and cyberthreats originating from this app.
- StreetChat (minimum age 14) – StreetChat is a photo-sharing board for middle school, high school and college-age students. Members do not need to be a student in the actual school and can impersonate students in schools across the country. It promotes cyberbullying through anonymous posts and private messaging.
- ooVoo (minimum age 13) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. ooVoo is one of the largest video and messages app. Parents should be aware that ooVoo is used by predators to contact underage children. The app can allow users to video chat with up to twelve people at one time.
- Wishbone (girls) & Slingshot (boys) (minimum age 13) – Both are comparison apps that allow users to create polls, including ones that are not appropriate for children. Many of the users create polls to shame and cyberbully other children, plus there are inappropriate apps and videos that users are forced to watch via the app’s advertising engine.
+++++++++++++++++++
Texas Teen May Be Victim in ‘Blue Whale Challenge’ That Encourages Suicide
Isaiah Gonzalez, 15, found hanging from his closet after an apparent suicide, as allegedly instructed by macabre online game
http://www.rollingstone.com/culture/news/texas-teen-latest-victim-in-challenge-that-promotes-suicide-w491939
Nationally, the Associated Press reports that educators, law enforcement officers and parents have raised concerns about the challenge, though these two back-to-back deaths mark the first allegations in the United States about deaths directly linked to the online game. Internationally, suicides in Russia, Brazil, and half a dozen other countries have already been linked to the challenge.
++++++++++++++++++++
more on social media in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=social+media+education
Privacy & Security in Today’s Library by Amigos Library Services
From: Jodie Borgerding [mailto:Borgerding@amigos.org]
Sent: Wednesday, July 05, 2017 3:07 PM
To: Miltenoff, Plamen <pmiltenoff@stcloudstate.edu>
Cc: Nicole Walsh <WALSH@AMIGOS.ORG>
Subject: Proposal Submission for Privacy & Security Conference
Hi Plamen,
Thank you for your recent presentation proposal for the online conference, Privacy & Security in Today’s Library, presented by Amigos Library Services. Your proposal, The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party,” has been accepted. I just wanted to confirm that you are still available to present on September 21, 2017 and if you have a time preference for your presentation (11 am, 12 pm, or 2 pm Central). If you are no longer able to participate, please let me know.
Nicole will be touch with you shortly with additional details and a speaker’s agreement.
Please let me know if you have any questions.
Thanks!
___________________
Jodie Borgerding Consulting & Education Services Manager Amigos Library Services 1190 Meramec Station Road, Suite 207 | Ballwin, MO 63021-6902 800-843-8482 x2897 | 972-340-2897(direct) http://www.amigos.org | borgerding@amigos.org
+++++++++++++++++
Bio
Dr. Plamen Miltenoff is an Information Specialist and Professor at St. Cloud State University. His education includes several graduate degrees in history and Library and Information Science and terminal degrees in education and psychology.
His professional interests encompass social media, multimedia, Web development and design, gaming and gamification, and learning environments (LEs).
Dr. Miltenoff organized and taught classes such as LIB 290 “Social Media in Global Context” (http://web.stcloudstate.edu/pmiltenoff/lib290/) and LIB 490/590 “Digital Storytelling” (http://web.stcloudstate.edu/pmiltenoff/lib490/) where issues of privacy and security are discussed.
Twitter handle @SCSUtechinstruc
Facebook page: https://www.facebook.com/InforMediaServices/
The virtuality of privacy and security on the modern campus:
The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party software” teaching and learning
Abstract/Summary of Your Proposed Session
The virtualization reality changes rapidly all aspects of learning and teaching: from equipment to methodology, just when faculty have finalized their syllabus, they have to start a new, if they want to keep abreast with content changes and upgrades and engagement of a very different student fabric – Millennials.
Mainframes are replaced by microcomputers, microcomputers by smart phones and tablets, hard drives by cloud storage and wearables by IoT. The pace of hardware, software and application upgrade is becoming unbearable for students and faculty. Content creation and methodology becomes useless by the speed of becoming obsolete. In such environment, faculty students and IT staff barely can devote time and energy to deal with the rapidly increasing vulnerability connected with privacy and security.
In an effort to streamline ever-becoming-scarce resources, campus IT “standardizes” campus use of applications. Those are the applications, which IT chooses to troubleshoot campus-wide. Those are the applications recommended to faculty and students to use.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal, attention on campuses is drown to the fact that cyberattacks shift now from mobile devices to IoT and campus often are struggling even with their capability to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party application might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
Abstract
The pace of changes in teaching and learning is becoming impossible to sustain: equipment evolves in accelerated pace, the methodology of teaching and learning cannot catch up with the equipment changes and atop, there are constant content updates. In an even-shrinking budget, faculty, students and IT staff barely can address the issues above, less time and energy left to address the increasing concerns about privacy and security.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal (https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/), attention on campuses is drawn to the fact of cyberattacks shifting from mobile devices to IoT but campus still struggling to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party applications might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/
Anything else you would like to add
3 take-aways from this session:
- Discuss and form an opinion about the education-pertinent issues of privacy and security from the broad campus perspective, versus the narrow library one
- Discuss and form an opinion about the role of the library on campus in terms of the greater issues of privacy and security
Re-examine the thin red line of the balance between standardization and innovation; between the need for security and privacy protection a
++++++++++++++
presentation:
https://www.slideshare.net/aidemoreto/the-virtuality-of-privacy-and-security-on-the
chat – slide 4, privacy. please take 2 min and share your definition of privacy on campus. Does it differ between faculty and students? what are the main characteristics to determine privacy
chat – slide 5, security. please take 2 min and share your definition of security on campus regarding electronic activities. Who’s responsibility is security? IT issue [only]?
poles: slide 6, technology unsupported by campus IT, is it worth considering? 1. i am a great believer in my freedom of choice 2. I firmly follow rules and this applies to the use of computer tools and applications 3. Whatever…
chat – slide 6, why third party applications? pros and cons. E.g. pros – familiarity with third party versus campus-required
pole, slide 6, appsmashing. App smashing is the ability to combine mobile apps in your teaching process. How do you feel about it? 1. The force is with us 2. Nonsense…
pole slide 7 third party apps and the comfort of faculty. How do you see the freedom of using third party apps? 1. All I want, thank you 2. I would rather follow the rules 3. Indifference is my middle name
pole slide 8 Technology standardization? 1. yes, 2. no, 3. indifferent
chat slide 9 if the two major issues colliding in this instance are: standardization versus third party and they have impact on privacy and security, how would you argue for the one or the other?
++++++++++++++++
notes from the conference
Speaker: Dr. Steve Albrecht – drsteve@drstevealbrecht.com
Follow @DrSteveAlbrecht
Dr. Steve Albrecht, author of Library Security: Better Communication, Safer Facilities, manages a training, coaching, and management consulting firm, using a dedicated and experienced team of subcontractor specialists. He is internationally known for his consulting and training work in workplace violence prevention training programs, school violence prevention, and high-risk human resources. Dr. Albrecht provides HR consulting, site security assessments, coaching, and training workshops in supervisory improvement, workplace violence prevention, harassment prevention, drug and alcohol awareness, team building, and more. He holds a B.A. in English, B.S. in Psychology, M.A. in Security Management, and a doctoral degree in Business Administration (D.B.A.). He has been a trainer for over 26 years and is a certified Professional in Human Resources (PHR), a Certified Protection Professional (CPP), a Board Certified Coach (BCC), and a Certified Threat Manager (CTM).
Session Description: Libraries don’t always need to hire a consultant to review the level of facility security. Using a structured assessment process, librarians can create a report that will help to make their building, staff, and patrons safer.
Chris Markman, MSLIS, MSIT Public Services Librarian Worcester Public Library
https://mycourses.amigos.org/mod/url/view.php?id=19623
Measuring Library Vendor Cyber Security: Seven Easy Questions Every Librarian Can Ask
http://journal.code4lib.org/articles/11413
Bill Walker: http://www.amigos.org/innovating_metadata
+++++++++++++++
more on security in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=security
more on privacy in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=privacy
Critical Factors for Implementing Blended Learning in Higher Education.
Available from: https://www.researchgate.net/publication/318191000_Critical_Factors_for_Implementing_Blended_Learning_in_Higher_Education [accessed Jul 6, 2017].
Definition of Blended learning
Blended learning is in one dimension broadly defined as “The convergence of online and face-to-face Education” as in the study by Watson (2008). At the same time it is important to also include the dimension of technology and media use as it has been depicted in the multimodal conceptual model in Figure 1 below. This conceptual model was proposed and presented in an article published by Picciano (2009). Critical Factors for Implementing Blended Learning in Higher Education.
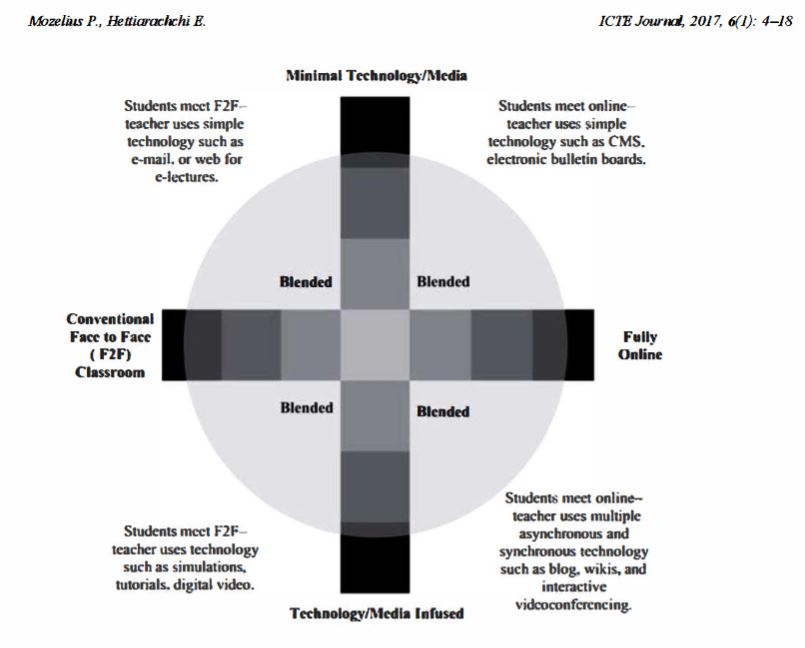
online face to face hybrid
Several studies that argue for the need to focus on pedagogy and learning objectives and not solely on technology (Hoffinan, 2006; Garrison & Vaughan, 2008; Al amm ary et al., 2014; McGee & Reis, 2012; Shand, Glassett Farrelly & Costa, 2016). Other findings in this study are that technology still is a critical issue (So & Brush, 2008; Fleming, Becker & Newton, 2017), not least in developing regions (AI Busaidi & Al-Shihi, 2012; Raphae1 & Mtebe, 2016), and also the more positive idea of technology as a supporting factor for innovative didactics and instructional design to satisfy the needs in heterogeneous student groups (Picciano, 2009). Critical Factors for Implementing Blended Learning in Higher Education.
Critical factors:
- technology
- didactics – pedagogy, instructional design and the teacher role
- Course outcomes – learning outcomes and learner satisfaction
- collaboration and social presence
- course design
- the heritage from technology enhanced distance courses
- multimodal overload
- trends and hypes
- economy
Blended learning perspectives
- the university perspective
- the Learner perspective
- the Teacher perspective
- the Global perspective
++++++++++++++++++++
more on blended learning in this IMS blog
https://blog.stcloudstate.edu/ims?s=blended+learning
Updating the Next Generation Digital Learning Environment for Better Student Learning Outcomes
- John Baker Monday, July 3, 2017
- http://er.educause.edu/articles/2017/7/updating-the-next-generation-digital-learning-environment-for-better-student-learning-outcomes
a learning management system (LMS) is never the solution to every problem in education. Edtech is just one part of the whole learning ecosystem and student experience.
Therefore, the next generation digital learning environment (NGDLE), as envisioned by EDUCAUSE in 2015 … Looking at the NGDLE requirements from an LMS perspective, I view the NGDLE as being about five areas: interoperability; personalization; analytics, advising, and learning assessment; collaboration; accessibility and universal design.
Interoperability
- Content can easily be exchanged between systems.
- Users are able to leverage the tools they love, including discipline-specific apps.
- Learning data is available to trusted systems and people who need it.
- The learning environment is “future proof” so that it can adapt and extend as the ecosystem evolves.
Personalization
- The learning environment reflects individual preferences.
- Departments, divisions, and institutions can be autonomous.
- Instructors teach the way they want and are not constrained by the software design.
- There are clear, individual learning paths.
- Students have choice in activity, expression, and engagement.
Analytics, Advising, and Learning Assessment
- Learning analytics helps to identify at-risk students, course progress, and adaptive learning pathways.
- The learning environment enables integrated planning and assessment of student performance.
- More data is made available, with greater context around the data.
- The learning environment supports platform and data standards.
Collaboration
- Individual spaces persist after courses and after graduation.
- Learners are encouraged as creators and consumers.
- Courses include public and private spaces.
Accessibility and Universal Design
- Accessibility is part of the design of the learning experience.
- The learning environment enables adaptive learning and supports different types of materials.
- Learning design includes measurement rubrics and quality control.
The core analogy used in the NGDLE paper is that each component of the learning environment is a Lego brick:
- The days of the LMS as a “walled garden” app that does everything is over.
- Today many kinds of amazing learning and collaboration tools (Lego bricks) should be accessible to educators.
- We have standards that let these tools (including an LMS) talk to each other. That is, all bricks share some properties that let them fit together.
- Students and teachers sign in once to this “ecosystem of bricks.”
- The bricks share results and data.
- These bricks fit together; they can be interchanged and swapped at will, with confidence that the learning experience will continue uninterrupted.
Any “next-gen” attempt to completely rework the pedagogical model and introduce a “mash-up of whatever” to fulfil this model would fall victim to the same criticisms levied at the LMS today: there is too little time and training to expect faculty to figure out the nuances of implementation on their own.
The Lego metaphor works only if we’re talking about “old school” Lego design — bricks of two, three, and four-post pieces that neatly fit together. Modern edtech is a lot more like the modern Lego. There are wheels and rocket launchers and belts and all kinds of amazing pieces that work well with each other, but only when they are configured properly. A user cannot simply stick together different pieces and assume they will work harmoniously in creating an environment through which each student can be successful.
As the NGDLE paper states: “Despite the high percentages of LMS adoption, relatively few instructors use its more advanced features — just 41% of faculty surveyed report using the LMS ‘to promote interaction outside the classroom.'”
But this is what the next generation LMS is good at: being a central nervous system — or learning hub — through which a variety of learning activities and tools are used. This is also where the LMS needs to go: bringing together and making sense of all the amazing innovations happening around it. This is much harder to do, perhaps even impossible, if all the pieces involved are just bricks without anything to orchestrate them or to weave them together into a meaningful, personal experience for achieving well-defined learning outcomes.
- Making a commitment to build easy, flexible, and smart technology
- Working with colleges and universities to remove barriers to adopting new tools in the ecosystem
- Standardizing the vetting of accessibility compliance (the Strategic Nonvisual Access Partner Program from the National Federation of the Blind is a great start)
- Advancing standards for data exchange while protecting individual privacy
- Building integrated components that work with the institutions using them — learning quickly about what is and is not working well and applying those lessons to the next generation of interoperability standards
- Letting people use the tools they love [SIC] and providing more ways for nontechnical individuals (including students) to easily integrate new features into learning activities
My note: something just refused to be accepted at SCSU
Technologists are often very focused on the technology, but the reality is that the more deeply and closely we understand the pedagogy and the people in the institutions — students, faculty, instructional support staff, administrators — the better suited we are to actually making the tech work for them.
++++++++++++++++++++++
Under the Hood of a Next Generation Digital Learning Environment in Progress
- by G. Alex Ambrose, Kevin Abbott and Alison Lanski Monday, July 31, 2017
- http://er.educause.edu/articles/2017/7/under-the-hood-of-a-next-generation-digital-learning-environment-in-progress
The challenge is that although 85 percent of faculty use a campus learning management system (LMS),1 a recent Blackboard report found that, out of 70,000 courses across 927 North American institutions, 53 percent of LMS usage was classified as supplemental(content-heavy, low interaction) and 24 percent as complementary (one-way communication via content/announcements/gradebook).2 Only 11 percent were characterized as social, 10 percent as evaluative (heavy use of assessment), and 2 percent as holistic (balanced use of all previous). Our FYE course required innovating beyond the supplemental course-level LMS to create a more holistic cohort-wide NGDLE in order to fully support the teaching, learning, and student success missions of the program.The key design goals for our NGDLE were to:
- Create a common platform that could deliver a standard curriculum and achieve parity in all course sections using existing systems and tools and readily available content
- Capture, store, and analyze any generated learner data to support learning assessment, continuous program improvement, and research
- Develop reports and actionable analytics for administrators, advisors, instructors, and students
++++++++++++
more on LMS in this blog
https://blog.stcloudstate.edu/ims?s=LMS
more on learning outcomes in this IMS blog
https://blog.stcloudstate.edu/ims?s=learning+outcomes
