Searching for "privacy"
CALL FOR CHAPTER PROPOSALS
Proposal Submission Deadline: February 12, 2019
Leveraging Technology for the Improvement of School Safety and Student Wellbeing
A book edited by Dr. Stephanie Huffman, Dr. Stacey Loyless, Dr. Shelly Allbritton, and Dr. Charlotte Green (University of Central Arkansas)
Introduction
Technology permeates all aspects of today’s school systems. An Internet search on technology in schools can generate millions of website results. The vast majority of these websites (well over 8,000,000 results for one simple search) focuses on advice, activities, and uses of technology in the classroom. Clearly teaching and learning with technology dominates the literature and conversations on how technology should or could be used in classroom settings. A search on school safety and technology can produce more than 3,000,000 results with many addressing technological tools such as video cameras, entry control devices, weapon detectors, and other such hardware. However, in recent times, cyberbullying appears to dominate the Internet conversations in references to school safety. With an increase in school violence in the past two decades, school safety is a fundamental concern in our nation’s schools. Policy makers, educators, parents, and students are seeking answers in how best to protect the physical, emotional, and social well-being of all children.
Objective of the Book
The proposed edited book covers the primary topic of P-12 school safety and the use of technology and technology used for fostering an environment in which all students can be academically successful and thrive as global citizens. School safety is defined as the physical, social, and emotional well-being of children. The book will comprise empirical, conceptual and case based (practical application) research that craft an overall understanding of the issues in creating a “safe” learning environment and the role technology can and should play; where a student’s well-being is valued and protected from external and internal entities, equitable access is treasured as a means for facilitating the growth of the whole student, and policy, practices, and procedures are implemented to build a foundation to transform the culture and climate of the school into an inclusive nurturing environment.
Target Audience
The target audience is leadership and education scholars, leadership practitioners, and technology coordinators. This book will be used as a collective body of work for the improvement of K-12 schools and as a tool for improving leadership and teacher preparation programs. School safety is a major concern for educators. Technology has played a role in creating unsafe environments for children; however it also is an avenue for addressing the challenges of school safety
Recommended topics include, but are not limited to, the following:
Section I – Digital Leadership
- Technology as a Climate and Cultural Transformation Tool
- School Leadership in the Digital Age: Building a Shared Vision for all Aspects of Learning and Teaching
- Ensuring Equity within a “One to One” Technology Framework
- Infrastructure within Communities
- Accessible WiFi for Low SES Students
- Developing Culturally Responsive Pedagogy
- Professional Development for School Leaders
Section II – Well Being
- Social Media and School Safety: Inputs and Outputs
- Tip lines: Crime, Bullying, Threats
- Communication and Transparency
- Platform for Social Justice
- Teaching Strategies to Promote Healthy Student Interactions in Cyberspace (Digital Citizenship?)
- Building Capacity and Efficacy, Platform to lower incidence of Cyber-Bullying, Boosting Instructional Engagement
- Literacy and Preparedness for the Influence and Consequence of Digital Media Marketing Campaigns directed toward Children, Adolescents, and Teens.
- Pioneering Innovative Technology Program in Curriculum: Fostering “Belonging” beyond Athletics & Arts.
Section III- Infrastructure Safety
- Campus/Facility Safety and Security
- Rural Schools vs. Urban Schools
- Digital A/V Systems
- Background Check – Visitor Registration (i.e. Raptor)
- Network Security Systems and Protocols
- User Filtering and Monitoring
- Firewalls
- Policy
- Appropriate use policies
- Digital Citizenship
- Web development policy
- Privacy
- Intellectual Property & Copyright
Section IV – Academic Success
- Professional Development for Classroom Teachers
- Pedagogical Integration of Technology
- Instructional Coaching for Student Engagement
- Increase Rigor with Technology
- Competence in the Blended/Hybrid/Flipped Classroom
- Technology to enhance learning for all
- Assistive Technology
- Accessibility issues
- Internet access for Low SES Students in the Blended/Hybrid/Flipped Classroom
- Personal Learning Design
- Differentiation for Student Efficacy
- Strategies for Increasing Depth of Knowledge
- Design Qualities for Enhanced Engagement
Submission Procedure
Researchers and practitioners are invited to submit on or before February 12, 2019, a chapter proposal of 1,000 to 2,000 words clearly explaining the purpose, methodology, and a brief summary findings of his or her proposed chapter. Authors will be notified by March 12, 2019 about the status of their proposals and sent chapter guidelines. Full chapters are expected to be submitted by June 12, 2019, and all interested authors must consult the guidelines for manuscript submissions at http://www.igi-global.com/publish/contributor-resources/before-you-write/ prior to submission. See Edited Chapter Template. All submitted chapters will be reviewed on a double-blind review basis. Contributors may also be requested to serve as reviewers for this project.
Note: There are no submission or acceptance fees for manuscripts submitted to this book publication, Leveraging Technology for the Improvement of School Safety and Student Wellbeing. All manuscripts are accepted based on a double-blind peer review editorial process.
All proposals should be submitted through the eEditorial Discovery®TM online submission manager. USE THE FOLLOWING LINK TO SUBMIT YOUR PROPOSAL. https://www.igi-global.com/publish/call-for-papers/call-details/3709
Publisher
This book is scheduled to be published by IGI Global (formerly Idea Group Inc.), an international academic publisher of the “Information Science Reference” (formerly Idea Group Reference), “Medical Information Science Reference,” “Business Science Reference,” and “Engineering Science Reference” imprints. IGI Global specializes in publishing reference books, scholarly journals, and electronic databases featuring academic research on a variety of innovative topic areas including, but not limited to, education, social science, medicine and healthcare, business and management, information science and technology, engineering, public administration, library and information science, media and communication studies, and environmental science. For additional information regarding the publisher, please visit http://www.igi-global.com. This publication is anticipated to be released in 2020.
Important Dates
February 12, 2019: Proposal Submission Deadline
March 12, 2019: Notification of Acceptance
June 12, 2019: Full Chapter Submission
August 10, 2019: Review Results Returned
August 10, 2019: Final Acceptance Notification
September 7, 2019: Final Chapter Submission
Inquiries can be forwarded to
Dr. Stephanie Huffman
University of Central Arkansas
steph@uca.edu or 501-450-5430
University Data Science Programs Turn to Ethics and the Humanities
https://www.edsurge.com/news/2019-01-11-university-data-science-programs-turn-to-ethics-and-the-humanities
“Formulating a product, you better know about ethics and understand legal frameworks.”
These days a growing number of people are concerned with bringing more talk of ethics into technology. One question is whether that will bring change to data-science curricula.
Following major data breaches and privacy scandals at tech companies like Facebook, universities including Stanford, the University of Texas and Harvard have all added ethics courses into computer science degree programs to address tech’s “ethical dark side,” the New York Times has reported.
As more college and universities consider incorporating humanities courses into technical degree programs, some are asking what kind of ethics should be taught.
++++++++++++++
more on ethics in this IMS blog
https://blog.stcloudstate.edu/ims?s=ethics
Will ‘Publish or Perish’ Become ‘Clicks or Canned’? The Rise of Academic Social Networks
https://www.edsurge.com/news/2017-08-01-will-publish-or-perish-become-clicks-or-canned-the-rise-of-academic-social-networks
Scholars want peers to find—and cite—their research, and these days that increasingly happens on social media. The old adage ‘publish or perish’ could soon go digital as ‘clicks or canned.’
Several platforms have emerged over the past decade, offering researchers the chance to share their work and connect with other scholars. But some of those services have a bad rap from academics who say commercial sites lack the integrity of institutional repositories run by traditional universities. (Among the most widely-villified are ResearchGate and Academia.edu, which is evident by griping on social media and elsewhere.)
a 2015 paper comparing services and tools offered by various academic social networks, says researchers must weigh the benefits and drawbacks of each. “They can be great tools to advance your research, especially social research,” she says. “But just like with Facebook or any other social network, we need to be aware of potential issues we might have with copyright or privacy.”
Academia.edu is the largest of the academic social networks.
Berlin-based ResearchGate
Created as a reference-management tool to help users organize their research, Mendeley also includes a number of social-networking features.
Scholabrate. The service claims to provide a more Facebook-esque, visual experience for academics seeking to network with others in their field.
Similar to Mendeley, Zotero functions primarily as a research tool, allowing users to collect, save, cite and share materials from a wide range of sources. The site also maintains a significant community of academics who can connect through groups and forums, or through their search engine.
CM/IEEE Joint Conference on Digital Libraries
June 2-6, 2019 – Urbana-Champaign, IL
Curated Knowledge. Connected People. Extraordinary Results.
UPDATED DEADLINE: January 25, 2019
JCDL welcomes interesting submissions ranging across theories, systems,
services, and applications. We invite those managing, operating, developing,
curating, evaluating, or utilizing digital libraries broadly defined, covering
academic or public institutions, including archives, museums, and social
networks. We seek involvement of those in iSchools, as well as working in
computer or information or social sciences and technologies. Multiple tracks
and sessions will ensure tailoring to researchers, practitioners, and diverse
communities including data science/analytics, data curation/stewardship,
information retrieval, human-computer interaction, hypertext (and Web/network
science), multimedia, publishing, preservation, digital humanities, machine
learning/AI, heritage/culture, health/medicine, policy, law, and privacy/
intellectual property.
Additional Topics of Interest:
In addition to the topics indicated above, the following are some of the many
topics that will be considered relevant, as long as connections are made to
digital libraries:
* Collaborative and participatory information environments
* Crowdsourcing and human computation
* Cyberinfrastructure architectures, applications, and deployments
* Distributed information systems
* Document genres
* Extracting semantics, entities, and patterns from large collections
* Information and knowledge systems
* Information visualization
* Infrastructure and service design
* Knowledge discovery
* Linked data and its applications
* Performance evaluation
* Personal digital information management
* Scientific data management
* Social media, architecture, and applications
* Social networks, virtual organizations and networked information
* User behavior and modeling
* User communities and user research
We invite submissions in many forms: short papers, long papers, panels,
posters, tutorials, and workshops. We also host a Doctoral Consortium.
Submission Deadlines:
Jan. 25, 2019 – Tutorial, workshop, full paper and short paper, and consortium
submissions
Jan. 29, 2019 – Panel, poster and demonstration submissions
Submissions are to be made in electronic format via the conference’s EasyChair
submission page. Please see the conference website for more details:
Find, vet and implement edtech – painlessly!
By Nicole Krueger 12/13/2018
Pre-vetted tools are rated in several categories
Educators seeking new technology can start by consulting a database of pre-vetted edtech tools, rated based on alignment with both child data privacy laws and the district’s instructional vision. Each entry includes notes about what the software does, how it can be used in the classroom, and the appropriate age level. Kaye is also working on aligning the database to the ISTE Standards so teachers can see at a glance which standards each tool can help them meet.
Every app falls into one of four categories:
- Tools the district approves, supports, pays for, and will train teachers to use.
- Tools that are approved and can be freely used on an independent basis.
- Tools that are approved with stipulations, such as age or parental permission requirements.
- Tools that are not approved because they don’t align with the district’s vision or data privacy needs.
Teachers can request to have a tool vetted
Teachers who choose a pre-vetted app from the approved list can start using it right away, without any further action needed. Educators who have a specific tool in mind that hasn’t yet been vetted can submit a request form that asks questions such as:
- How does the tool connect to the curriculum?
- Will students be consumers or producers when using it?
- How easy is it to learn and use?
- What are some of the things they plan on doing with it?
a survey conducted by nonprofit organization Project Tomorrow.
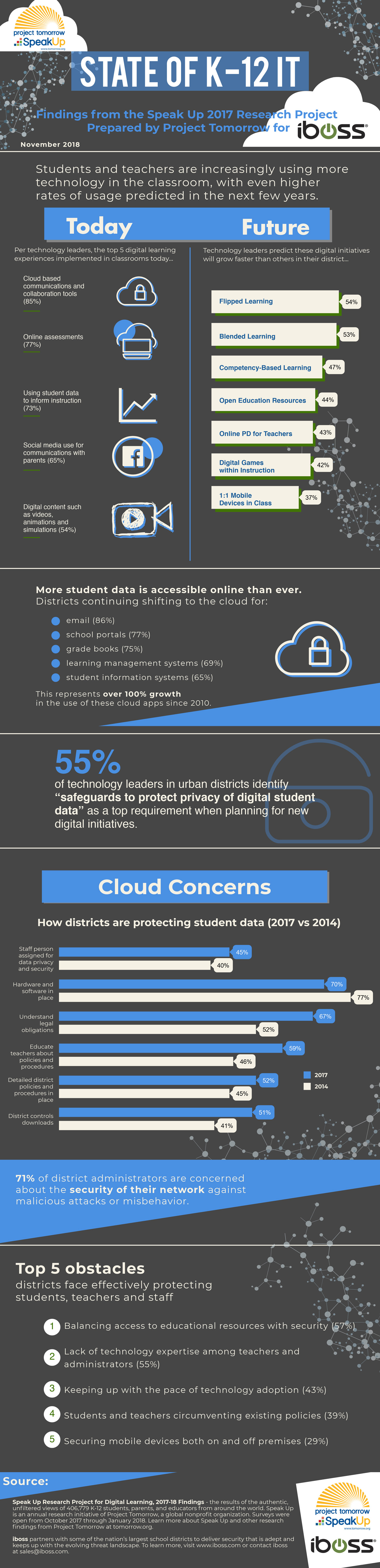
https://edtechmagazine.com/k12/article/2019/01/state-k-12-it-survey-highlights-cloud-technology-and-security-infographic
Eighty percent of K–12 districts are using cloud-based software to improve everything
With the incorporation of cloud-based tools, K–12 schools are starting to consider more effective privacy and security measures, such as identity access management and managed cloud services from third-party vendors that can take responsibility for overseeing security.
Making Media Literacy Central to Digital Citizenship
Tanner Higgin, Common Sense Education
https://www.kqed.org/mindshift/49607/making-media-literacy-central-to-digital-citizenship
While we often get distracted by the latest device or platform release, video has quietly been riding the wave of all of these advancements, benefiting from broader access to phones, displays, cameras and, most importantly, bandwidth. In fact, 68 percent of teachers are using video in their classrooms, and 74 percent of middle schoolers are watching videos for learning. From social media streams chock-full of video and GIFs to FaceTime with friends to two-hour Twitch broadcasts, video mediates students’ relationships with each other and the world. Video is a key aspect of our always-online attention economy that’s impacting voting behavior, and fueling hate speech and trolling. Put simply: Video is a contested civic space.
We need to move from a conflation of digital citizenship with internet safety and protectionism to a view of digital citizenship that’s pro-active and prioritizes media literacy and savvy. A good digital citizen doesn’t just dodge safety and privacy pitfalls, but works to remake the world, aided by digital technology like video, so it’s more thoughtful, inclusive and just.
1. Help Students Identify the Intent of What They Watch
equip students with some essential questions they can use to unpack the intentions of anything they encounter. One way to facilitate this thinking is by using a tool like EdPuzzle to edit the videos you want students to watch by inserting these questions at particularly relevant points in the video.
2. Be Aware That the Web Is a Unique Beast
Compared to traditional media (like broadcast TV or movies), the web is the Wild West.
Mike Caulfield’s e-book is a great deep dive into this topic, but as an introduction to web literacy you might first dig into the notion of reading “around” as well as “down” media — that is, encouraging students to not just analyze the specific video or site they’re looking at but related content (e.g., where else an image appears using a reverse Google image search).
3. Turn Active Viewing into Reactive Viewing
Active viewing
For this content, students shouldn’t just be working toward comprehension but critique;
using aclassroom backchannel, like TodaysMeet, during video viewings
4. Transform Students’ Video Critiques into Creations
Digital citizenship should be participatory, meaning students need to be actively contributing to culture. Unfortunately, only 3 percent of the time tweens and teens spend using social media is focused on creation.
facilitating video creation and remix, but two of my favorites are MediaBreaker and Vidcode.
5. Empower Students to Become Advocates
Blockchain Disciples Have a New Goal: Running Our Next Election
Amid vote-hacking fears, election officials are jumping on the crypto bandwagon — but cybersecurity experts are sounding an alarm
At democracy’s heart lies a set of paradoxes: a delicate interplay of identity and anonymity, secrecy and transparency. To be sure you are eligible to vote and that you do so only once, the authorities need to know who you are. But when it comes time for you to mark a ballot, the government must guarantee your privacy and anonymity. After the fact, it also needs to provide some means for a third party to audit the election, while also preventing you from obtaining definitive proof of your choice, which could lead to vote selling or coercion.
Building a system that accomplishes all this at once — and does so securely — is challenging enough in the physical world. It’s even harder online, as the recent revelation that Russian intelligence operatives
compromised voting systems in multiple states makes clear.
In the decade since the elusive Satoshi Nakamoto published an infamous
white paper outlining the idea behind bitcoin, a “peer-to-peer electronic cash system” based on a mathematical “consensus mechanism,” more than 1,500 new
cryptocurrencies have come into being.
definition: Nathan Heller in the New Yorker, in which he compares the blockchain to a scarf knit with a single ball of yarn. “It’s impossible to remove part of the fabric, or to substitute a swatch, without leaving some trace,” Heller wrote. Typically, blockchains are created by a set of stakeholders working to achieve consensus at every step, so it might be even more apt to picture a knitting collective creating that single scarf together, moving forward only when a majority agrees that a given knot is acceptable.
Unlike bitcoin, a public blockchain powered by thousands of miners around the world, most voting systems, including Votem’s, employ what’s known as a “permissioned ledger,” in which a handful of approved groups (political parties, election observers, government entities) would be allowed to validate the transactions.
there’s the issue of targeted denial-of-service (DoS) attacks, in which a hacker directs so much traffic at a server that it’s overwhelmed and ceases to function.
Although a distributed ledger itself would likely withstand such an attack, the rest of the system — from voters’ personal devices to the many servers a vote would pass through on its way to the blockchain — would remain vulnerable.
there’s the so-called penetration attack, like the University of Michigan incursion, in which an adversary gains control of a server and deliberately alters the outcome of an election.
While it’s true that information recorded on a blockchain cannot be changed, a determined hacker might well find another way to disrupt the process. Bitcoin itself has never been hacked, for instance, but numerous bitcoin “wallets” have been, resulting in
billions of dollars in losses. In early June 2018, a South Korean cryptocurrency exchange was
penetrated, causing the value of bitcoin to tumble and resulting in a loss of $42 billion in market value. So although recording the vote tally on a blockchain introduces a new obstacle to penetration attacks, it still leaves holes elsewhere in the system — like putting a new lock on your front door but leaving your basement windows open.
A blockchain is only as valuable as the data stored on it. And whereas traditional paper ballots preserve an indelible record of the actual intent of each voter, digital votes “don’t produce an original hard-copy record of any kind,”
In the end, democracy always depends on a certain leap of faith, and faith can never be reduced to a mathematical formula. The Economist Intelligence Unit
regularly ranks the world’s most democratic counties. In 2017, the United States came in 21st place, after Uruguay and Malta. Meanwhile, it’s now widely believed that John F. Kennedy owed his 1960 win to election tampering in Chicago. The Supreme Court decision granting the presidency to George W. Bush rather than calling a do-over — despite Al Gore’s popular-vote win — still seems iffy. Significant doubts remain about the 2016 presidential race.
While little doubt remains that Russia favored Trump in the 2016 election, the Kremlin’s primary target appears to have been our trust in the system itself. So if the blockchain’s trendy allure can bolster trust in American democracy, maybe that’s a net positive for our national security. If someone manages to hack the system, hopefully they’ll do so quietly. Apologies to George Orwell, but sometimes ignorance really is strength.
+++++++++++
more on blockchain in this IMS blog
https://blog.stcloudstate.edu/ims?s=blockchain
https://events.educause.edu/eli/annual-meeting/2019/programs-and-tracks
- What new kinds of leadership are required for this new teaching and learning landscape?
- What are the best methods and techniques that promote innovation and creative thinking to support student learning?
- What new educational technologies seem most promising?
- What role should data and analytics play, and what are the trade-offs between analytics and privacy?
- How can we best determine the efficacy of our learning innovations and technologies?
- What learning spaces and environments best promote active learning
2019 ELI Annual Meeting Tracks
- Accessibility and Universal Design for Learning (UDL)
- Analytics: Privacy, Learning Data, Student Advising, and Interventions
- Digital and Information Literacy
- Faculty Development and Engagement
- Innovation in Instructional Design and Course Models
- Leadership and Academic Transformation
- Learning Efficacy: Impact Evaluation, Learning Research and Science
- Learning Environments and Spaces
- Learning Horizons: Emerging Technology, Ground-Breaking Practices, and Educational Futures
- Open Education
- Student Success
Key Issues in Teaching and Learning
https://www.educause.edu/eli/initiatives/key-issues-in-teaching-and-learning
A roster of results since 2011 is here.

1. Academic Transformation
2. Accessibility and UDL
3. Faculty Development
4. Privacy and Security
5. Digital and Information Literacies
https://cdn.nmc.org/media/2017-nmc-strategic-brief-digital-literacy-in-higher-education-II.pdf
Three Models of Digital Literacy: Universal, Creative, Literacy Across Disciplines
United States digital literacy frameworks tend to focus on educational policy details and personal empowerment, the latter encouraging learners to become more effective students, better creators, smarter information consumers, and more influential members of their community.
National policies are vitally important in European digital literacy work, unsurprising for a continent well populated with nation-states and struggling to redefine itself, while still trying to grow economies in the wake of the 2008 financial crisis and subsequent financial pressures
African digital literacy is more business-oriented.
Middle Eastern nations offer yet another variation, with a strong focus on media literacy. As with other regions, this can be a response to countries with strong state influence or control over local media. It can also represent a drive to produce more locally-sourced content, as opposed to consuming material from abroad, which may elicit criticism of neocolonialism or religious challenges.
p. 14 Digital literacy for Humanities: What does it mean to be digitally literate in history, literature, or philosophy? Creativity in these disciplines often involves textuality, given the large role writing plays in them, as, for example, in the Folger Shakespeare Library’s instructor’s guide. In the digital realm, this can include web-based writing through social media, along with the creation of multimedia projects through posters, presentations, and video. Information literacy remains a key part of digital literacy in the humanities. The digital humanities movement has not seen much connection with digital literacy, unfortunately, but their alignment seems likely, given the turn toward using digital technologies to explore humanities questions. That development could then foster a spread of other technologies and approaches to the rest of the humanities, including mapping, data visualization, text mining, web-based digital archives, and “distant reading” (working with very large bodies of texts). The digital humanities’ emphasis on making projects may also increase
Digital Literacy for Business: Digital literacy in this world is focused on manipulation of data, from spreadsheets to more advanced modeling software, leading up to degrees in management information systems. Management classes unsurprisingly focus on how to organize people working on and with digital tools.
Digital Literacy for Computer Science: Naturally, coding appears as a central competency within this discipline. Other aspects of the digital world feature prominently, including hardware and network architecture. Some courses housed within the computer science discipline offer a deeper examination of the impact of computing on society and politics, along with how to use digital tools. Media production plays a minor role here, beyond publications (posters, videos), as many institutions assign multimedia to other departments. Looking forward to a future when automation has become both more widespread and powerful, developing artificial intelligence projects will potentially play a role in computer science literacy.
6. Integrated Planning and Advising Systems for Student Success (iPASS)
7. Instructional Design
8. Online and Blended Learning
In traditional instruction, students’ first contact with new ideas happens in class, usually through direct instruction from the professor; after exposure to the basics, students are turned out of the classroom to tackle the most difficult tasks in learning — those that involve application, analysis, synthesis, and creativity — in their individual spaces. Flipped learning reverses this, by moving first contact with new concepts to the individual space and using the newly-expanded time in class for students to pursue difficult, higher-level tasks together, with the instructor as a guide.
Let’s take a look at some of the myths about flipped learning and try to find the facts.
Myth: Flipped learning is predicated on recording videos for students to watch before class.
Fact: Flipped learning does not require video. Although many real-life implementations of flipped learning use video, there’s nothing that says video must be used. In fact, one of the earliest instances of flipped learning — Eric Mazur’s peer instruction concept, used in Harvard physics classes — uses no video but rather an online text outfitted with social annotation software. And one of the most successful public instances of flipped learning, an edX course on numerical methods designed by Lorena Barba of George Washington University, uses precisely one video. Video is simply not necessary for flipped learning, and many alternatives to video can lead to effective flipped learning environments [http://rtalbert.org/flipped-learning-without-video/].
Myth: Flipped learning replaces face-to-face teaching.
Fact: Flipped learning optimizes face-to-face teaching. Flipped learning may (but does not always) replace lectures in class, but this is not to say that it replaces teaching. Teaching and “telling” are not the same thing.
Myth: Flipped learning has no evidence to back up its effectiveness.
Fact: Flipped learning research is growing at an exponential pace and has been since at least 2014. That research — 131 peer-reviewed articles in the first half of 2017 alone — includes results from primary, secondary, and postsecondary education in nearly every discipline, most showing significant improvements in student learning, motivation, and critical thinking skills.
Myth: Flipped learning is a fad.
Fact: Flipped learning has been with us in the form defined here for nearly 20 years.
Myth: People have been doing flipped learning for centuries.
Fact: Flipped learning is not just a rebranding of old techniques. The basic concept of students doing individually active work to encounter new ideas that are then built upon in class is almost as old as the university itself. So flipped learning is, in a real sense, a modern means of returning higher education to its roots. Even so, flipped learning is different from these time-honored techniques.
Myth: Students and professors prefer lecture over flipped learning.
Fact: Students and professors embrace flipped learning once they understand the benefits. It’s true that professors often enjoy their lectures, and students often enjoy being lectured to. But the question is not who “enjoys” what, but rather what helps students learn the best.They know what the research says about the effectiveness of active learning
Assertion: Flipped learning provides a platform for implementing active learning in a way that works powerfully for students.
9. Evaluating Technology-based Instructional Innovations

What is the total cost of my innovation, including both new spending and the use of existing resources?
What’s the unit I should measure that connects cost with a change in performance?
How might the expected change in student performance also support a more sustainable financial model?
The Exposure Approach: we don’t provide a way for participants to determine if they learned anything new or now have the confidence or competence to apply what they learned.
The Exemplar Approach: from ‘show and tell’ for adults to show, tell, do and learn.
The Tutorial Approach: Getting a group that can meet at the same time and place can be challenging. That is why many faculty report a preference for self-paced professional development.build in simple self-assessment checks. We can add prompts that invite people to engage in some sort of follow up activity with a colleague. We can also add an elective option for faculty in a tutorial to actually create or do something with what they learned and then submit it for direct or narrative feedback.
The Course Approach: a non-credit format, these have the benefits of a more structured and lengthy learning experience, even if they are just three to five-week short courses that meet online or in-person once every week or two.involve badges, portfolios, peer assessment, self-assessment, or one-on-one feedback from a facilitator
The Academy Approach: like the course approach, is one that tends to be a deeper and more extended experience. People might gather in a cohort over a year or longer.Assessment through coaching and mentoring, the use of portfolios, peer feedback and much more can be easily incorporated to add a rich assessment element to such longer-term professional development programs.
The Mentoring Approach: The mentors often don’t set specific learning goals with the mentee. Instead, it is often a set of structured meetings, but also someone to whom mentees can turn with questions and tips along the way.
The Coaching Approach: A mentor tends to be a broader type of relationship with a person.A coaching relationship tends to be more focused upon specific goals, tasks or outcomes.
The Peer Approach:This can be done on a 1:1 basis or in small groups, where those who are teaching the same courses are able to compare notes on curricula and teaching models. They might give each other feedback on how to teach certain concepts, how to write syllabi, how to handle certain teaching and learning challenges, and much more. Faculty might sit in on each other’s courses, observe, and give feedback afterward.
The Self-Directed Approach:a self-assessment strategy such as setting goals and creating simple checklists and rubrics to monitor our progress. Or, we invite feedback from colleagues, often in a narrative and/or informal format. We might also create a portfolio of our work, or engage in some sort of learning journal that documents our thoughts, experiments, experiences, and learning along the way.
The Buffet Approach:
10. Open Education
11. Learning Analytics
12. Adaptive Teaching and Learning
13. Working with Emerging Technology
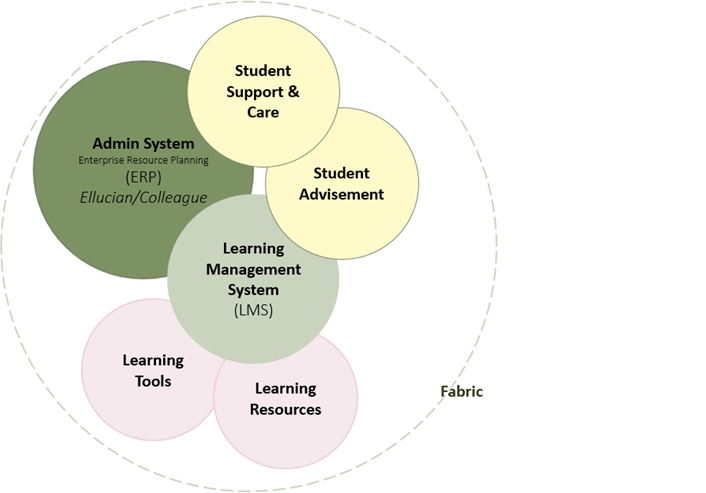
In 2014, administrators at Central Piedmont Community College (CPCC) in Charlotte, North Carolina, began talks with members of the North Carolina State Board of Community Colleges and North Carolina Community College System (NCCCS) leadership about starting a CBE program.
Building on an existing project at CPCC for identifying the elements of a digital learning environment (DLE), which was itself influenced by the EDUCAUSE publication The Next Generation Digital Learning Environment: A Report on Research,1 the committee reached consensus on a DLE concept and a shared lexicon: the “Digital Learning Environment Operational Definitions,