Tumbleson, B. E., & Burke, J. (. J. (2013). Embedding librarianship in learning management systems: A how-to-do-it manual for librarians. Neal-Schuman, an imprint of the American Library Association.
|
 |
https://scsu.mplus.mnpals.net/vufind/Record/007650037
see also:
Kvenild, C., & Calkins, K. (2011).
Embedded Librarians: Moving Beyond One-Shot Instruction – Books / Professional Development – Books for Academic Librarians – ALA Store. ACRL. Retrieved from
http://www.alastore.ala.org/detail.aspx?ID=3413
p. 20 Embedding Academic and Research Libraries in the Curriculum: 2014-nmc-horizon-report-library-EN
xi. the authors are convinced that LMS embedded librarianship is becoming he primary and most productive method for connecting with college and university students, who are increasingly mobile.
xii. reference librarians engage the individual, listen, discover what is wanted and seek to point the stakeholder in profitable directions.
Instruction librarians, in contrast, step into the classroom and attempt to lead a group of students in new ways of searching wanted information.
Sometimes that instruction librarian even designs curriculum and teaches their own credit course to guide information seekers in the ways of finding, evaluating, and using information published in various formats.
Librarians also work in systems, emerging technologies, and digital initiatives in order to provide infrastructure or improve access to collections and services for tend users through the library website, discovery layers, etc. Although these arenas seemingly differ, librarians work as one.
xiii. working as an LMS embedded librarian is both a proactive approach to library instruction using available technologies and enabling a 24/7 presence.
1. Embeddedness involves more that just gaining perspective. It also allows the outsider to become part of the group through shared learning experiences and goals. 3. Embedded librarianship in the LMS is all about being as close as possible to where students are receiving their assignments and gaining instruction and advice from faculty members. p. 6 When embedded librarians provide ready access to scholarly electronic collections, research databases, and Web 2.0 tools and tutorials, the research experience becomes less frustrating and more focused for students. Undergraduate associate this familiar online environment with the academic world.
p. 7 describes embedding a reference librarian, which LRS reference librarians do, “partnership with the professor.” However, there is room for “Research Consultations” (p. 8). While “One-Shot Library Instruction Sessions” and “Information Literacy Credit Courses” are addressed (p. 809), the content of these sessions remains in the old-fashioned lecturing type of delivering the information.
p. 10-11. The manuscript points out clearly the weaknesses of using a Library Web site. The authors fail to see that the efforts of the academic librarians must go beyond Web page and seek how to easy the information access by integrating the power of social media with the static information residing on the library web page.
p. 12 what becomes disturbingly clear is that faculty focus on the mechanics of the research paper over the research process. Although students are using libraries, 70 % avoid librarians. Urging academic librarians to “take an active role and initiate the dialogue with faculty to close a divide that may be growing between them and faculty and between them and students.”
Four research context with which undergraduates struggle: big picture, language, situational context and information gathering.
p. 15 ACRL standards One and Three: librarians might engage students who rely on their smartphones, while keeping in mind that “[s]tudents who retrieve information on their smartphones may also have trouble understanding or evaluating how the information on their phone is ‘produced, organized, and disseminated’ (Standard One).
Standard One by its definition seems obsolete. If information is formatted for desktops, it will be confusing when on smart phones, And by that, it is not mean to adjust the screen size, but change the information delivery from old fashioned lecturing to more constructivist forms. e.g. http://web.stcloudstate.edu/pmiltenoff/bi/
p. 15 As for Standard Two, which deals with effective search strategies, the LMS embedded librarian must go beyond Boolean operators and controlled vocabulary, since emerging technologies incorporate new means of searching. As unsuccessfully explained to me for about two years now at LRS: hashtag search, LinkedIn groups etc, QR codes, voice recognition etc.
p. 16. Standard Five. ethical and legal use of information.
p. 23 Person announced in 2011 OpenClass compete with BB, Moodle, Angel, D2L, WebCT, Sakai and other
p. 24 Common Features: content, email, discussion board, , synchronous chat and conferencing tools (Wimba and Elluminate for BB)
p. 31 information and resources which librarians could share via LMS
– post links to dbases and other resources within the course. LIB web site, LibGuides or other subject-related course guidelines
– information on research concepts can be placed in a similar fashion. brief explanation of key information literacy topics (e.g difference between scholarly and popular periodical articles, choosing or narrowing research topics, avoiding plagiarism, citing sources properly whining required citations style, understanding the merits of different types of sources (Articles book’s website etc)
– Pertinent advice the students on approaching the assignment and got to rheank needed information
– Tutorials on using databases or planning searches step-by-step screencast navigating in search and Candida bass video search of the library did you a tour of the library
p. 33 embedded librarian being copied on the blanked emails from instructor to students.
librarian monitors the discussion board
p. 35 examples: students place specific questions on the discussion board and are assured librarian to reply by a certain time
instead of F2F instruction, created a D2L module, which can be placed in any course. videos, docls, links to dbases, links to citation tools etc. Quiz, which faculty can use to asses the the students
p. 36 discussion forum just for the embedded librarian. for the students, but faculty are encouraged to monitor it and provide content- or assignment-specific input
video tutorials and searching tips
Contact information email phone active IM chat information on the library’s open hours
p. 37 questions to consider
what is the status of the embedded librarian: T2, grad assistant
p. 41 pilot program. small scale trial which is run to discover and correct potential problems before
One or two faculty members, with faculty from a single department
Pilot at Valdosta State U = a drop-in informatil session with the hope of serving the information literacy needs of distance and online students, whereas at George Washington U, librarian contacted a distance education faculty member to request embedding in his upcoming online Mater’s course
p. 43 when librarians sense that current public services are not being fully utilized, it may signal that a new approach is needed.
pilots permit tinkering. they are all about risk-taking to enhance delivery
p. 57 markeing LMS ebedded Librarianship
library collections, services and facilities because faculty may be uncertain how the service benefits their classroom teaching and learning outcomes.
my note per
“it is incumbent upon librarians to promote this new mode of information literacy instruction.” it is so passe. in the times when digital humanities is discussed and faculty across campus delves into digital humanities, which de facto absorbs digital literacy, it is shortsighted for academic librarians to still limit themselves into “information literacy,” considering that lip service is paid for for librarians being the leaders in the digital humanities movement. If academic librarians want to market themselves, they have to think broad and start with topics, which ARE of interest for the campus faculty (digital humanities included) and then “push” their agenda (information literacy). One of the reasons why academic libraries are sinking into oblivion is because they are sunk already in 1990-ish practices (information literacy) and miss the “hip” trends, which are of interest for faculty and students. The authors (also paying lip services to the 21st century necessities), remain imprisoned to archaic content. In the times, when multi (meta) literacies are discussed as the goal for library instruction, they push for more arduous marketing of limited content. Indeed, marketing is needed, but the best marketing is by delivering modern and user-sought content.
the stigma of “academic librarians keep doing what they know well, just do it better.” Lip-services to change, and life-long learning. But the truth is that the commitment to “information literacy” versus the necessity to provide multi (meta) literacites instruction (Reframing Information Literacy as a metaliteracy) is minimizing the entire idea of academic librarians reninventing themselves in the 21st century.
Here is more: NRNT-New Roles for New Times
p. 58 According to the Burke and Tumbleson national LMS embedded librarianship survey, 280 participants yielded the following data regarding embedded librarianship:
- traditional F2F LMS courses – 69%
- online courses – 70%
- hybrid courses – 54%
- undergraduate LMS courses 61%
- graduate LMS courses 42%
of those respondents in 2011, 18% had the imitative started for four or more years, which place the program in 2007. Thus, SCSU is almost a decade behind.
p. 58 promotional methods:
- word of mouth
- personal invitation by librarians
- email by librarians
- library brochures
- library blogs
four years later, the LRS reference librarians’ report https://magic.piktochart.com/output/5704744-libsmart-stats-1415 has no mentioning of online courses, less to say embedded librarianship
my note:
library blog was offered numerous times to the LRS librarians and, consequently to the LRS dean, but it was brushed away, as were brushed away the proposals for modern institutional social media approach (social media at LRS does not favor proficiency in social media but rather sees social media as learning ground for novices, as per 11:45 AM visit to LRS social media meeting of May 6, 2015). The idea of the blog advantages to static HTML page was explained in length, but it was visible that the advantages are not understood, as it is not understood the difference of Web 2.0 tools (such as social media) and Web 1.0 tools (such as static web page). The consensus among LRS staff and faculty is to keep projecting Web 1.0 ideas on Web 2.0 tools (e.g. using Facebook as a replacement of Adobe Dreamweaver: instead of learning how to create static HTML pages to broadcast static information, use Facebook for fast and dirty announcement of static information). It is flabbergasting to be rejected offering a blog to replace Web 1.0 in times when the corporate world promotes live-streaming (http://www.socialmediaexaminer.com/live-streaming-video-for-business/) as a way to promote services (academic librarians can deliver live their content)
p. 59 Marketing 2.0 in the information age is consumer-oriented. Marketing 3.0 in the values-driven era, which touches the human spirit (Kotler, Katajaya, and Setiawan 2010, 6).
The four Ps: products and services, place, price and promotion. Libraries should consider two more P’s: positioning and politics.
Mathews (2009) “library advertising should focus on the lifestyle of students. the academic library advertising to students today needs to be: “tangible, experiential, relatebale, measurable, sharable and surprising.” Leboff (2011, p. 400 agrees with Mathews: the battle in the marketplace is not longer for transaction, it is for attention. Formerly: billboards, magazines, newspapers, radio, tv, direct calls. Today: emphasize conversation, authenticity, values, establishing credibility and demonstrating expertise and knowledge by supplying good content, to enhance reputation (Leboff, 2011, 134). translated for the embedded librarians: Google goes that far; students want answers to their personal research dillemas and questions. Being a credentialed information specialist with years of experience is no longer enough to win over an admiring following. the embedded librarian must be seen as open and honest in his interaction with students.
p. 60 becoming attractive to end-users is the essential message in advertising LMS embedded librarianship. That attractivness relies upon two elements: being noticed and imparting values (Leboff, 2011, 99)
p. 61 connecting with faculty
p. 62 reaching students
- attending a synchronous chat sessions
- watching a digital tutorial
- posting a question in a discussion board
- using an instant messaging widget
be careful not to overload students with too much information. don’t make contact too frequently and be perceived as an annoyance and intruder.
p. 65. contemporary publicity and advertising is incorporating storytelling. testimonials differ from stories
p. 66 no-cost marketing. social media
low-cost marketing – print materials, fliers, bookmarks, posters, floor plans, newsletters, giveaways (pens, magnets, USB drives), events (orientations, workshops, contests, film viewings), campus media, digital media (lib web page, blogs, podcasts, social networking cites
p. 69 Instructional Content and Instructional Design
p. 70 ADDIE Model


Analysis: the requirements for the given course, assignments.
Ask instructors expectations from students vis-a-vis research or information literacy activities
students knowledge about the library already related to their assignments
which are the essential resources for this course
is this a hybrid or online course and what are the options for the librarian to interact with the students.
due date for the research assignment. what is the timeline for completing the assignment
when research tips or any other librarian help can be inserted
copy of the syllabus or any other assignment document
p. 72 discuss the course with faculty member. Analyze the instructional needs of a course. Analyze students needs. Create list of goals. E.g.: how to find navigate and use the PschInfo dbase; how to create citations in APA format; be able to identify scholarly sources and differentiate them from popular sources; know other subject-related dbases to search; be able to create a bibliography and use in-text citations in APA format
p. 74 Design (Addie)
the embedded component is a course within a course. Add pre-developed IL components to the broader content of the course. multiple means of contact information for the librarians and /or other library staff. link to dbases. link to citation guidance and or tutorial on APA citations. information on how to distinguish scholarly and popular sources. links to other dbases. information and guidance on bibliographic and in-text citations n APA either through link, content written within the course a tutorial or combination. forum or a discussion board topic to take questions. f2f lib instruction session with students
p. 76 decide which resources to focus on and which skills to teach and reinforce. focus on key resources
p. 77 development (Addie).
-building content;the “landing” page at LRS is the subject guides page. resources integrated into the assignment pages. video tutorials and screencasts
-finding existing content; google search of e.g.: “library handout narrowing topic” or “library quiz evaluating sources,” “avoiding plagiarism,” scholarly vs popular periodicals etc
-writing narrative content. p. 85
p. 87 Evaluation (Addie)
formative: to change what the embedded librarian offers to improve h/er services to students for the reminder of the course
summative at the end of the course:
p. 89 Online, F2F and Hybrid Courses
p. 97 assessment impact of embedded librarian.
what is the purpose of the assessment; who is the audience; what will focus on; what resources are available
p. 98 surveys of faculty; of students; analysis of student research assignments; focus groups of students and faculty
p. 100 assessment methods: p. 103/4 survey template
https://www.ets.org/iskills/about
https://www.projectsails.org/ (paid)
http://www.trails-9.org/
http://www.library.ualberta.ca/augustana/infolit/wassail/
p. 106 gathering LMS stats. Usability testing
examples: p. 108-9, UofFL : pre-survey and post-survey of studs perceptions of library skills, discussion forum analysis and interview with the instructor
p. 122 create an LMS module for reuse (standardized template)
p. 123 subject and course LibGuides, digital tutorials, PPTs,
research mind maps, charts, logs, or rubrics
http://creately.com/blog/wp-content/uploads/2012/12/Research-Proposal-mind-map-example.png
http://www.library.arizona.edu/help/tutorials/mindMap/sample.php (excellent)
or paper-based if needed: Concept Map Worksheet
Productivity Tools for Graduate Students: MindMapping http://libguides.gatech.edu/c.php
rubrics:
http://www.cornellcollege.edu/LIBRARY/faculty/focusing-on-assignments/tools-for-assessment/research-paper-rubric.shtml
http://gvsu.edu/library/instruction/research-guidance-rubric-for-assignment-design-4.htm
Creating Effective Information Literacy Assignments http://www.lib.jmu.edu/instruction/assignments.aspx
course handouts
guides on research concepts http://library.olivet.edu/subject-guides/english/college-writing-ii/research-concepts/
http://louisville.libguides.com/c.php
Popular versus scholar http://www.library.arizona.edu/help/tutorials/scholarly/guide.html
list of frequently asked q/s:
blog posts
banks of reference q/s
p. 124. Resistance or Receptivity
p. 133 getting admin access to LMS for the librarians.
p. 136 mobile students, dominance of born-digital resources
———————-
Summey T, Valenti S. But we don’t have an instructional designer: Designing online library instruction using isd techniques. Journal Of Library & Information Services In Distance Learning [serial online]. January 1, 2013;Available from: Scopus®, Ipswich, MA. Accessed May 11, 2015.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dedselc%26AN%3dedselc.2-52.0-84869866367%26site%3deds-live%26scope%3dsite
instructional designer library instruction using ISD techniques
Shank, J. (2006). The blended librarian: A job announcement analysis of the newly emerging position of instructional design librarian. College And Research Libraries, 67(6), 515-524.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dedselc%26AN%3dedselc.2-52.0-33845291135%26site%3deds-live%26scope%3dsite
The Blended Librarian_ A Job Announcement Analysis of the Newly Emerging Position of Instructional Design Librarian
Macklin, A. (2003). Theory into practice: Applying David Jonassen’s work in instructional design to instruction programs in academic libraries. College And Research Libraries, 64(6), 494-500.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dedselc%26AN%3dedselc.2-52.0-7044266019%26site%3deds-live%26scope%3dsite
Theory into Practice_ Applying David Jonassen_s Work in Instructional Design to Instruction Programs in Academic Libraries
Walster, D. (1995). Using Instructional Design Theories in Library and Information Science Education. Journal of Education for Library and Information Science, (3). 239.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dedsjsr%26AN%3dedsjsr.10.2307.40323743%26site%3deds-live%26scope%3dsite
Using Instructional Design Theories in Library and Information Science Education
Mackey, T. )., & Jacobson, T. ). (2011). Reframing information literacy as a metaliteracy. College And Research Libraries, 72(1), 62-78.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dedselc%26AN%3dedselc.2-52.0-79955018169%26site%3deds-live%26scope%3dsite
Reframing Information Literacy as a metaliteracy
Nichols, J. (2009). The 3 directions: Situated information literacy. College And Research Libraries, 70(6), 515-530.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dedselc%26AN%3dedselc.2-52.0-73949087581%26site%3deds-live%26scope%3dsite
The 3 Directions_ Situated literacy
—————
Journal of Library & Information Services in Distance Learning (J Libr Inform Serv Dist Learn)
https://www.researchgate.net/journal/1533-290X_Journal_of_Library_Information_Services_in_Distance_Learning
http://conference.acrl.org/
http://www.loex.org/conferences.php
http://www.ala.org/lita/about/igs/distance/lit-igdl
————
https://magic.piktochart.com/output/5704744-libsmart-stats-1415
Voice over presentation
Faculty request to lay voice over a presentation with pictures. Solutions:
Windows / PC

ppt voice over
Apple/Mac
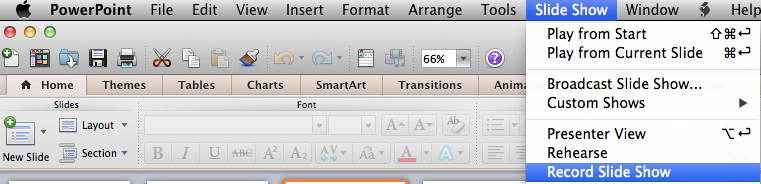
voice over PPT on Apple
advantages:
– unfortunately, faculty are way too familiar with PPT. Familiar to the point that they don’t want to try something better.
– FERPA complient
disadvantages:
– too old. PPT is pre-Internet. It does not matter how much Microsoft is trying to adapt it, the concept is old. There is a myriad of cloud-based solutions, which do better job: https://blog.stcloudstate.edu/ims/2013/09/30/the-5-best-free-slideshow-presentation-and-creation-tools-for-teachers/
– too many files, too many variations
– PPT posted in D2L displays in the D2L Viewer. The visuals are there, but the voice is not. In order to hear the voice, students must download the presentation. Faculty must reflect this in the syllabus.
– faculty need to know how to upload on their web space and figure out URL, if PPT is not place in LMS (D2L)- if faculty places PPT in LMS (D2L), then it is behind password; nearly impossible to share (can share only with SCSU and/or MnSCU members.
– faculty must remember to indicate in the syllabus and/or D2L / Content that “in order to hear the voice over, user must download presentation.”

slideshare
advantages:
– it is a “social” app, like LinkedIn and Twitter. Tagged correctly, the presentation is a platform for “same-minded” people to discuss mutual interests.
– excellent for sharing: conferences, MOOCs etc.
– it has discussion group in LinkedIn.
disadvantages:
– voice over presentation: way to cumbersome compared to PPT. Watch their presentation
– by FERPA regulations, if the presentation contains personal data about students, it cannot be shared on SlideShare
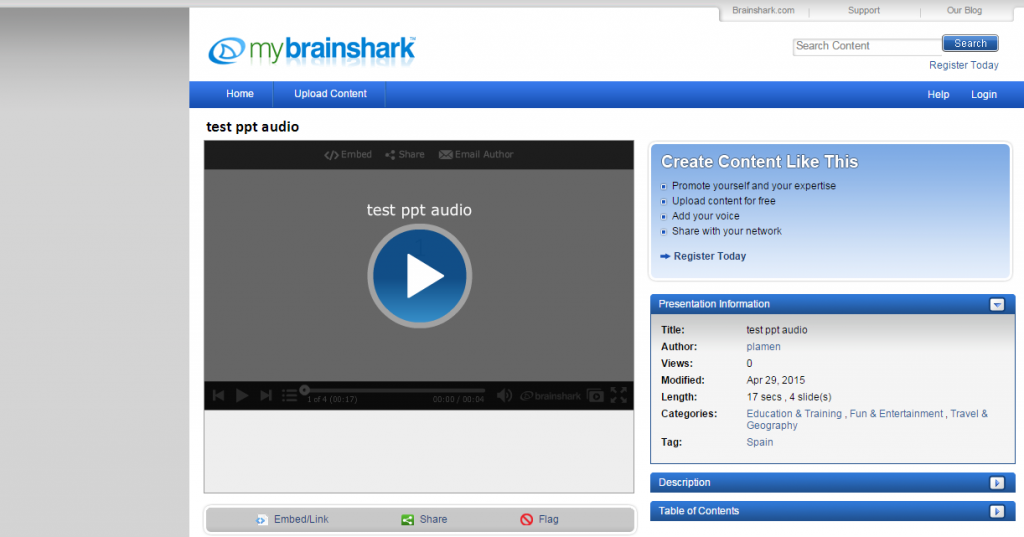
mybrainshaark
advantages:
– it is a “social” app, like LinkedIn and Twitter. Tagged correctly, the presentation is a platform for “same-minded” people to discuss mutual interests.
– excellent for sharing: conferences, MOOCs etc.
– like PPT, very easy upload of pix and voice over. Better the PPT, since it is online and easy to distribute.
– easy to upload PPT and easy to voice over each slide
disadvantages:
– does not embed in D2L (it is D2L issue, not the app), but works perfectly as a link
– faculty must remember to indicate in the syllabus and/or D2L / Content that when clicking on the URL to the PPT, user must simultaneously press “Ctrl” key to open PPT in a separate browser window or tab
– by FERPA regulations, if the presentation contains personal data about students, it cannot be shared on SlideShare
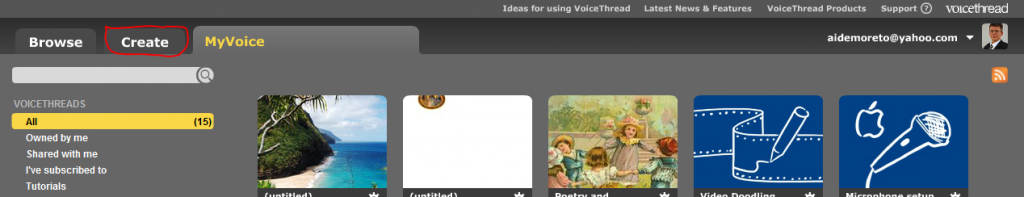
voicethread
advantages:
– consistently voted through last 5 years by K12 educators as great interactive tool.
– video, images, audio and text.
– “constructivist” premiss: teacher and students can exchange asynchronously ideas by using images, video, text and audio.
disadvantages:
– free option has limited features.
– by FERPA regulations, if the presentation contains personal data about students, it cannot be shared on on this site.
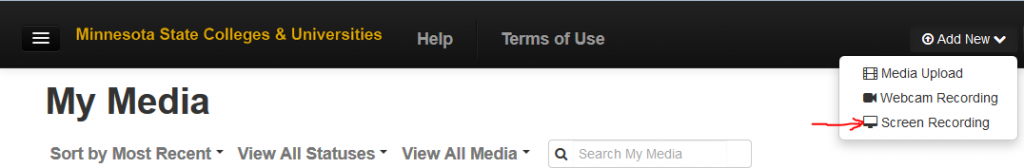
mediasite
advantages:
– crude screen capture: faculty can run the PPT manually and narrate over it.
– dirty but fast
– easily shared online (URL ready)
– FERPA compliant
disadvantages:
– students cannot comment (compared to VoiceThread)
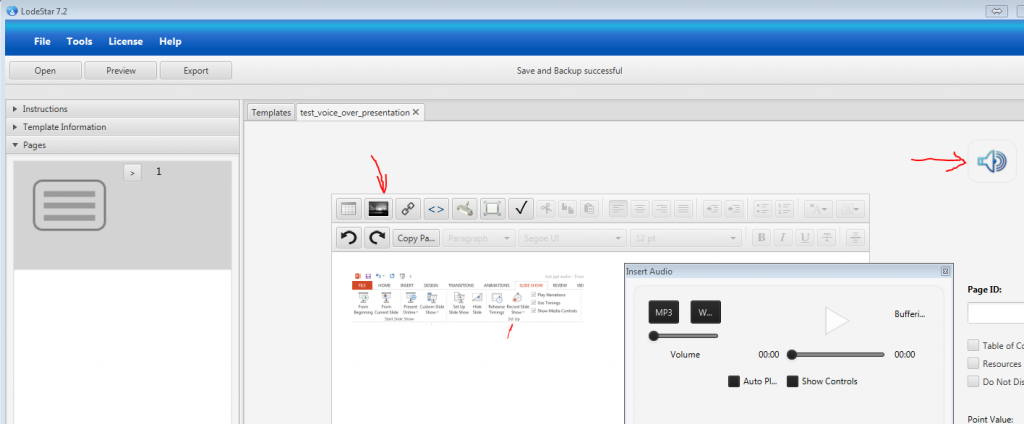
- lodestar
advantages:
– free: http://lodestarlearning.com/downloads/lodeStar7.2/en/LodeStar-7.0.exe
– easy to use
– FERPA compliant; endorsed by MnSCU
disadvantages:
– voice over too complex (very much the same as with SlideShare)
advantages:
– FERPA compliant; endorsed by MnSCU
disadvantages:
–
I have not included TechSmit’s Jing https://www.techsmith.com/jing.html, because their video output (Flash file) is obsolete and impossible to convert for free. While it still can be played, shall faculty want to upload the video file on Youtube or similar social media, it will be impossible.
———————————-
Related IMS blog entries:
https://blog.stcloudstate.edu/ims/2014/06/01/social-media-and-presentations-free-image-sources/
https://blog.stcloudstate.edu/ims/2013/09/30/the-5-best-free-slideshow-presentation-and-creation-tools-for-teachers/
5 Essential Insights About Mobile Learning
http://ww2.kqed.org/mindshift/2014/07/15/5-essential-insights-about-mobile-learning/
1. Set goals and expectations for teaching and learning with mobile devices before worrying about the device itself.
St. Vrain Valley School District in Colorado,
Mooresville Graded School District
Consolidated High School District 230
2. Develop a strong community of support for the initiative early and keep up transparent communication with parents and community members throughout the process.
Forsyth County Schools in Georgia.
3. Think about equity, but don’t let it stop forward motion.
includes both urban and rural areas,
4. Evaluate the effectiveness of a mobile learning initiative based on the goals set at the beginning of the rollout.
5. Some of the biggest lessons learned include giving up control and trusting students.
included students in the discussions
STAY NIMBLE
While these mobile learning pioneers have seen some of the pitfalls and can help districts new to the game avoid the same stumbles, this space is changing quickly and every community’s needs will be different.
“It’s no longer just something you implement; it’s evolving and it’s unique in each location,” Bjerede said. “If you try to be cookie cutter about it you won’t meet the needs of every kid in every classroom.”
The technology will change, students will surprise their teachers and the best advice to district leaders is to stay open to all the possibilities and allow students to take control of the tremendous learning opportunity that having a device at all times could offer them.
=====================================
My note: Kathrina Schwartz offers an opinion, which reflects the second wave (withdrawl) in the 3 steps of innovation
The Struggles and Realities of Student-Driven Learning and BYOD
http://ww2.kqed.org/mindshift/2014/07/07/the-struggles-and-realities-of-student-driven-learning-and-byod/
A 2013 Pew study revealed that only 35 percent of teachers at the lowest income schools allow their students to look up information on their mobile devices, as compared to 52 percent of teachers at wealthier schools.
Many advocates of using mobile technologies say the often cited issues of student distraction are just excuses not to try something new.
“The way you discourage it is engage them in the activity so they don’t even think of sending a text. You’ve got to jump in and play their game or you’re going to lose them.”
Angela Crawford has heard all the arguments of BYOD evangelists, but doesn’t see how they match the reality of her classroom. “BYOD is very problematic in many schools, mine included, because we have a prominent engagement problem,” Crawford said.
Tactics to improve engagement like making work relevant to her students’ lives or letting them use their phones in class to look up information, haven’t worked for Crawford, although she’s tried.
When she first started, Crawford was enthusiastic about jumping into collaborative, project-based learning. “I thought my colleagues were monsters because of how they were teaching,” she said of a school where she previously worked and where teachers lectured all the time. She tried to teach students through projects, but found it was a disaster. To her students’ parents, her efforts to make the classroom “student-centered” looked like she wasn’t teaching. “There is a different perception of what a teacher should be in different cultures,” Crawford said. “And in the African-American community in the South the teacher is supposed to do direct instruction.”
“What works best for each student is really the heart of student-centered learning,” Crawford said. “Sometimes what the student needs best is direct instruction. They need that authoritative, in-control figure who is directing their learning and will get them where they need to go.” Many of Crawford’s students come from homes run by single mothers who rule with an iron hand. She tries to replicate that attitude and presence. “They respond to that; they like it,” Crawford said. “It’s comforting to them.”
Still, Crawford will not be experimenting with a bring-your-own-device program. “My problem with education innovation is we tend to want to take a new technology or a new idea and go forth with it as if it’s the silver bullet,” Crawford said. “What happens is that teachers who teach in my type of environment realize this would be a disaster in my classroom.”
Crawford is skeptical that kids in higher income areas aren’t misusing technology too. Her children attend school in a more affluent district and they tell her that kids are constantly messing around on their devices. They just switch screens when a teacher comes by. They get away with it because their teachers trust them to do their work.
“I think kids in middle class or upper middle class schools are equally distracted as low-income students,” said Bob Lenz, director of innovation at Envision Schools, a small charter network that’s part of the deeper learning movement. “It’s just that because of the privilege of their background the content and the skills that they need to gain in school — they’re coming with a lot of those skills already– so it’s not as urgently needed.”










