Code2LIB February 2018
http://2018.code4lib.org/
2018 Preconference Voting
10. The Virtualized Library: A Librarian’s Introduction to Docker and Virtual Machines
This session will introduce two major types of virtualization, virtual machines using tools like VirtualBox and Vagrant, and containers using Docker. The relative strengths and drawbacks of the two approaches will be discussed along with plenty of hands-on time. Though geared towards integrating these tools into a development workflow, the workshop should be useful for anyone interested in creating stable and reproducible computing environments, and examples will focus on library-specific tools like Archivematica and EZPaarse. With virtualization taking a lot of the pain out of installing and distributing software, alleviating many cross-platform issues, and becoming increasingly common in library and industry practices, now is a great time to get your feet wet.
(One three-hour session)
11. Digital Empathy: Creating Safe Spaces Online
User research is often focused on measures of the usability of online spaces. We look at search traffic, run card sorting and usability testing activities, and track how users navigate our spaces. Those results inform design decisions through the lens of information architecture. This is important, but doesn’t encompass everything a user needs in a space.
This workshop will focus on the other component of user experience design and user research: how to create spaces where users feel safe. Users bring their anxieties and stressors with them to our online spaces, but informed design choices can help to ameliorate that stress. This will ultimately lead to a more positive interaction between your institution and your users.
The presenters will discuss the theory behind empathetic design, delve deeply into using ethnographic research methods – including an opportunity for attendees to practice those ethnographic skills with student participants – and finish with the practical application of these results to ongoing and future projects.
(One three-hour session)
14. ARIA Basics: Making Your Web Content Sing Accessibility
https://dequeuniversity.com/assets/html/jquery-summit/html5/slides/landmarks.html
Are you a web developer or create web content? Do you add dynamic elements to your pages? If so, you should be concerned with making those dynamic elements accessible and usable to as many as possible. One of the most powerful tools currently available for making web pages accessible is ARIA, the Accessible Rich Internet Applications specification. This workshop will teach you the basics for leveraging the full power of ARIA to make great accessible web pages. Through several hands-on exercises, participants will come to understand the purpose and power of ARIA and how to apply it for a variety of different dynamic web elements. Topics will include semantic HTML, ARIA landmarks and roles, expanding/collapsing content, and modal dialog. Participants will also be taught some basic use of the screen reader NVDA for use in accessibility testing. Finally, the lessons will also emphasize learning how to keep on learning as HTML, JavaScript, and ARIA continue to evolve and expand.
Participants will need a basic background in HTML, CSS, and some JavaScript.
(One three-hour session)
18. Learning and Teaching Tech
Tech workshops pose two unique problems: finding skilled instructors for that content, and instructing that content well. Library hosted workshops are often a primary educational resource for solo learners, and many librarians utilize these workshops as a primary outreach platform. Tackling these two issues together often makes the most sense for our limited resources. Whether a programming language or software tool, learning tech to teach tech can be one of the best motivations for learning that tech skill or tool, but equally important is to learn how to teach and present tech well.
This hands-on workshop will guide participants through developing their own learning plan, reviewing essential pedagogy for teaching tech, and crafting a workshop of their choice. Each participant will leave with an actionable learning schedule, a prioritized list of resources to investigate, and an outline of a workshop they would like to teach.
(Two three-hour sessions)
23. Introduction to Omeka S
Omeka S represents a complete rewrite of Omeka Classic (aka the Omeka 2.x series), adhering to our fundamental principles of encouraging use of metadata standards, easy web publishing, and sharing cultural history. New objectives in Omeka S include multisite functionality and increased interaction with other systems. This workshop will compare and contrast Omeka S with Omeka Classic to highlight our emphasis on 1) modern metadata standards, 2) interoperability with other systems including Linked Open Data, 3) use of modern web standards, and 4) web publishing to meet the goals medium- to large-sized institutions.
In this workshop we will walk through Omeka S Item creation, with emphasis on LoD principles. We will also look at the features of Omeka S that ease metadata input and facilitate project-defined usage and workflows. In accordance with our commitment to interoperability, we will describe how the API for Omeka S can be deployed for data exchange and sharing between many systems. We will also describe how Omeka S promotes multiple site creation from one installation, in the interest of easy publishing with many objects in many contexts, and simplifying the work of IT departments.
(One three-hour session)
24. Getting started with static website generators
Have you been curious about static website generators? Have you been wondering who Jekyll and Hugo are? Then this workshop is for you
My note: https://opensource.com/article/17/5/hugo-vs-jekyll
But this article isn’t about setting up a domain name and hosting for your website. It’s for the step after that, the actual making of that site. The typical choice for a lot of people would be to use something like WordPress. It’s a one-click install on most hosting providers, and there’s a gigantic market of plugins and themes available to choose from, depending on the type of site you’re trying to build. But not only is WordPress a bit overkill for most websites, it also gives you a dynamically generated site with a lot of moving parts. If you don’t keep all of those pieces up to date, they can pose a significant security risk and your site could get hijacked.
The alternative would be to have a static website, with nothing dynamically generated on the server side. Just good old HTML and CSS (and perhaps a bit of Javascript for flair). The downside to that option has been that you’ve been relegated to coding the whole thing by hand yourself. It’s doable, but you just want a place to share your work. You shouldn’t have to know all the idiosyncrasies of low-level web design (and the monumental headache of cross-browser compatibility) to do that.
Static website generators are tools used to build a website made up only of HTML, CSS, and JavaScript. Static websites, unlike dynamic sites built with tools like Drupal or WordPress, do not use databases or server-side scripting languages. Static websites have a number of benefits over dynamic sites, including reduced security vulnerabilities, simpler long-term maintenance, and easier preservation.
In this hands-on workshop, we’ll start by exploring static website generators, their components, some of the different options available, and their benefits and disadvantages. Then, we’ll work on making our own sites, and for those that would like to, get them online with GitHub pages. Familiarity with HTML, git, and command line basics will be helpful but are not required.
(One three-hour session)
26. Using Digital Media for Research and Instruction
To use digital media effectively in both research and instruction, you need to go beyond just the playback of media files. You need to be able to stream the media, divide that stream into different segments, provide descriptive analysis of each segment, order, re-order and compare different segments from the same or different streams and create web sites that can show the result of your analysis. In this workshop, we will use Omeka and several plugins for working with digital media, to show the potential of video streaming, segmentation and descriptive analysis for research and instruction.
(One three-hour session)
28. Spark in the Dark 101 https://zeppelin.apache.org/
This is an introductory session on Apache Spark, a framework for large-scale data processing (https://spark.apache.org/). We will introduce high level concepts around Spark, including how Spark execution works and it’s relationship to the other technologies for working with Big Data. Following this introduction to the theory and background, we will walk workshop participants through hands-on usage of spark-shell, Zeppelin notebooks, and Spark SQL for processing library data. The workshop will wrap up with use cases and demos for leveraging Spark within cultural heritage institutions and information organizations, connecting the building blocks learned to current projects in the real world.
(One three-hour session)
29. Introduction to Spotlight https://github.com/projectblacklight/spotlight
http://www.spotlighttechnology.com/4-OpenSource.htm
Spotlight is an open source application that extends the digital library ecosystem by providing a means for institutions to reuse digital content in easy-to-produce, attractive, and scholarly-oriented websites. Librarians, curators, and other content experts can build Spotlight exhibits to showcase digital collections using a self-service workflow for selection, arrangement, curation, and presentation.
This workshop will introduce the main features of Spotlight and present examples of Spotlight-built exhibits from the community of adopters. We’ll also describe the technical requirements for adopting Spotlight and highlight the potential to customize and extend Spotlight’s capabilities for their own needs while contributing to its growth as an open source project.
(One three-hour session)
31. Getting Started Visualizing your IoT Data in Tableau https://www.tableau.com/
The Internet of Things is a rising trend in library research. IoT sensors can be used for space assessment, service design, and environmental monitoring. IoT tools create lots of data that can be overwhelming and hard to interpret. Tableau Public (https://public.tableau.com/en-us/s/) is a data visualization tool that allows you to explore this information quickly and intuitively to find new insights.
This full-day workshop will teach you the basics of building your own own IoT sensor using a Raspberry Pi (https://www.raspberrypi.org/) in order to gather, manipulate, and visualize your data.
All are welcome, but some familiarity with Python is recommended.
(Two three-hour sessions)
32. Enabling Social Media Research and Archiving
Social media data represents a tremendous opportunity for memory institutions of all kinds, be they large academic research libraries, or small community archives. Researchers from a broad swath of disciplines have a great deal of interest in working with social media content, but they often lack access to datasets or the technical skills needed to create them. Further, it is clear that social media is already a crucial part of the historical record in areas ranging from events your local community to national elections. But attempts to build archives of social media data are largely nascent. This workshop will be both an introduction to collecting data from the APIs of social media platforms, as well as a discussion of the roles of libraries and archives in that collecting.
Assuming no prior experience, the workshop will begin with an explanation of how APIs operate. We will then focus specifically on the Twitter API, as Twitter is of significant interest to researchers and hosts an important segment of discourse. Through a combination of hands-on and demos, we will gain experience with a number of tools that support collecting social media data (e.g., Twarc, Social Feed Manager, DocNow, Twurl, and TAGS), as well as tools that enable sharing social media datasets (e.g., Hydrator, TweetSets, and the Tweet ID Catalog).
The workshop will then turn to a discussion of how to build a successful program enabling social media collecting at your institution. This might cover a variety of topics including outreach to campus researchers, collection development strategies, the relationship between social media archiving and web archiving, and how to get involved with the social media archiving community. This discussion will be framed by a focus on ethical considerations of social media data, including privacy and responsible data sharing.
Time permitting, we will provide a sampling of some approaches to social media data analysis, including Twarc Utils and Jupyter Notebooks.
(One three-hour session)
There Are Plenty Of RFID-Blocking Products, But Do You Need Them?
hackers can access your credit card data wirelessly, through something called radio frequency identification, or RFID
card has a tiny RFID sensor chip. These chips are supposed to make life easier by emitting radio signals for fast identification. The technology helps keep track of livestock and inventory. It makes automatic payment on toll roads and faster scanning of passports possible, and, starting around 2004, brought us contactless payment with certain credit cards.
REI and other companies sell a range of RFID-blocking products and say the number of customers looking for travel bags and credit card sleeves has been growing. That’s despite the fact that the percentage of credit cards with RFID chips in the U.S. is extremely small.
Still, people are worried about electronic pickpocketing — worried enough to strap on RFID-blocking fanny packs, even skinny jeans. In 2014, the San Francisco-based clothing company Betabrand partnered with Norton Security to create the first pair of denim with RFID protected pockets.
Eva Velasquez, president of the Identity Theft Resource Center, says from a consumer perspective, deciding whether to invest in RFID-blocking technology is all about evaluating risk. In the next few years, there will undoubtedly be millions more of these cards on the market.
if you’re worried about e-pickpocketing but don’t want to spend much money, you can make your own blocking wallet or wrap your cards or passport in a thick piece of aluminum foil. According to Consumer Reports, that works as well as most RFID protectors on the market.
+++++++++++++++
more on cybersecurity in this IMS blog
Survey: IoT Overtakes Mobile as Security Threat
By Rhea Kelly 06/05/17
https://campustechnology.com/articles/2017/06/05/survey-iot-overtakes-mobile-as-security-threat.aspx
a report from ISACA, a nonprofit association focused on knowledge and practices for information systems. The 2017 State of Cyber Security Study surveyed IT security leaders around the globe on security issues, the emerging threat landscape, workforce challenges and more.
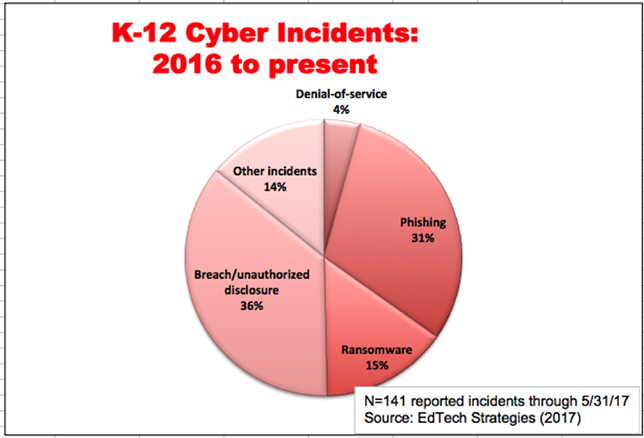
- 53 percent of survey respondents reported a year-over-year increase in cyber attacks;
- 62 percent experienced ransomware in 2016, but only 53 percent have a formal process in place to address a ransomware attack;
- 78 percent reported malicious attacks aimed at impairing an organization’s operations or user data;
- Only 31 percent said they routinely test their security controls, while 13 percent never test them; and
- 16 percent do not have an incident response plan.
- 65 percent of organizations now employ a chief information security officers, up from 50 percent in 2016, yet still struggle to fill open cyber security positions;
- 48 percent of respondents don’t feel comfortable with their staff’s ability to address complex cyber security issues;
- More than half say cyber security professionals “lack an ability to understand the business”;
- One in four organizations allot less than $1,000 per cyber security team member for training; and
- About half of the organizations surveyed will see an increase in their cyber security budget, down from 61 percent in 2016.
++++++++++++++++++++++++++
IoT to Represent More Than Half of Connected Device Landscape by 2021
By Sri Ravipati 06/09/17
https://campustechnology.com/articles/2017/06/09/iot-to-represent-more-than-half-of-connected-device-landscape-by-2021.aspx
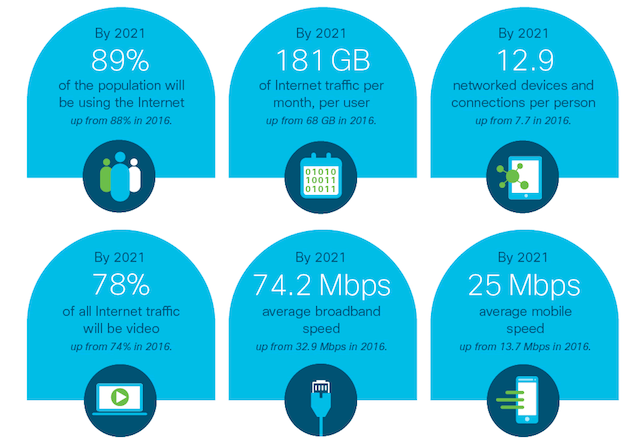
analysis comes from Cisco’s recent Visual Networking Index for the 2016-2021 forecast period.
- IP video traffic will increase from 73 percent of all internet consumer traffic in 2016 to 82 percent in 2021 (with live streaming accounting for 13 percent);
- Virtual and augmented reality traffic is expected to increase 20-fold during the forecast period at a compound annual growth rate of 82 percent; and
- Internet video surveillance traffic is anticipated to grow during the forecast period, comprising 3.4 percent of all internet traffic.
To learn more, view the full report.
+++++++++++++++++++++++++++
5 ways to use the Internet of Things in higher ed
By Danielle R. June 14th, 2017
1. Labeling and Finding
2. Booking and Availability
3. Preparation
4. Intervention
5. Research
Laboratories are often required to be completely controlled spaces with considerations made for climate, light, and sometimes even biometric data inside the lab.
+++++++++++++++++++++
https://blog.stcloudstate.edu/ims?s=internet+of+things
https://blog.stcloudstate.edu/ims?s=iot
Apps for Librarians: Empower Your Users with Mobile App Literacy eCourse
Nicole Hennig
Item Number: 1541-9076 Publisher: ALA Editions Price: $250.00
http://www.alastore.ala.org/detail.aspx?ID=11270&zbrandid=4634&zidType=CH&zid=42706629&zsubscriberId=1026665847&zbdom=http://ala-publishing.informz.net
Estimated Hours of Learning: 28
Certificate of Completion available upon request
Learning outcomes
After participating in this eCourse, you will:
- Gain experience using some of the best apps available and understand how they enable learning
- Learn how to evaluate and review mobile apps
- Learn how tablets complement laptops, and how their capabilities are creating new learning opportunities
- Learn how apps are being used by people with special needs, and where to find additional resources for learning more
- Receive guidance for creating your own app guides, offering workshops, and advising colleagues
In this 5-week eCourse, you’ll learn about the most useful apps available on tablet and mobile devices and how they can be applied in your library to create the best learning experiences for your patrons and students.
Mobile apps are empowering for people of all ages and abilities. Contrary to the popular idea that apps are only useful for “consumption,” the best apps are being used effectively as tools to enable learning and knowledge creation. In this eCourse, Nicole Hennig will show you how to incorporate apps as learning tools at your library.
eCourse Outline
Week 1 – E-Reading
The Apps
- Book reading
- Magazine reading
- Apps for Reading PDFs, web pages, and news feeds
- Individual book apps
Readings & Discussion
- Readings about e-reading & future of the book
- Your thoughts on the readings (discussion forum)
- Optional app review assignment
Week 2 – Productivity & Writing
The Apps
- Productivity
- Cloud storage, passwords, to do lists, notes
- Handwriting, speech recognition, scanning, barcodes
- Writing & Presenting
- Word processing, spreadsheets, slides
- More presentation apps
Readings & Discussion
- Readings about security, writing, mobile apps in academia
- Your thoughts on the readings (discussion forum)
- Optional app review assignment
Week 3 – Reference
The Apps
- Dictionaries, encyclopedias
- Unit converters, maps, languages
- Specialized reference apps
- Subscription databases & citations
Readings & Discussion
- Readings about jailbreaking, platforms, & mobile web
- Apple’s iOS Human Interface Guidelines
- Your thoughts on the readings (discussion forum)
- Optional app review assignment
Week 4 – Multimedia
The Apps
- Art viewing
- Art creation
- Photography and photo editing
- Music listening
- Music creation
- Video viewing and editing
Readings & Discussion
- Readings about technology & children
- Your thoughts on the readings (discussion forum)
- Optional app review assignment
Week 5 – Accessibility & More
Accessibility features of mobile devices
Readings & Discussion
- Readings about assistive technology
- Your thoughts on the readings (discussion forum)
Idea generation assignment
- Ideas for using apps in library programs & services
- Apps that wow
How this eCourse Works
The eCourse begins on June 5, 2017. Your participation will require approximately five to six hours a week, at times that fit your schedule. All activities take place on the website, and you will be expected to:
- Read, listen to or view online content
- Post to online discussion boards
- Complete weekly assignments or activities
Instructor Nicole Hennig will monitor discussion boards regularly during the five-week period, lead group discussions, and will also answer individual questions. All interaction will take place on the eCourse site, which will be available 24 hours a day, 7 days a week. It’s recommended that students log into the site on the first day of class or within a few days for an overview of the content and to begin the first lesson.
+++++++++++++
more on mobile apps in this IMS blog
https://blog.stcloudstate.edu/ims?s=mobile+apps