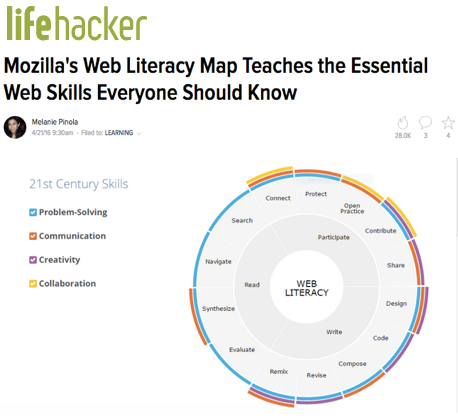
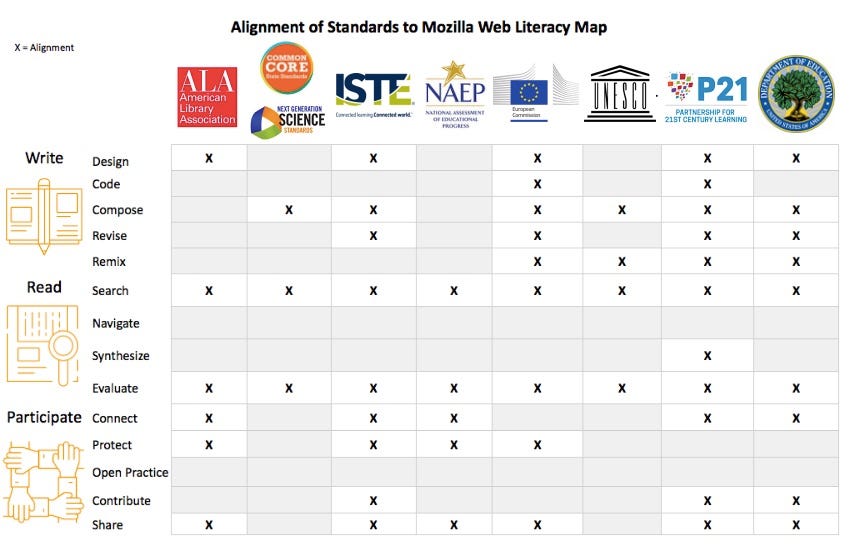
qualifications of the embedded librarian: is there any known case for an academic library to employ as embedded librarian a specialist who has both MLIS and terminal degree in a discipline, where he works as embedded librarian.
“I also think that we need to be more welcoming to people who may not have come through a traditional education program (i.e., the M.L.S.) but who bring critical skills and new perspectives into the library.”
The Changing Roles of Academic and Research Libraries – Higher Ed Careers – HigherEdJobs. (2013). Retrieved from https://www.higheredjobs.com/HigherEdCareers/interviews.cfm?ID=632
“Embedded librarian” is understood as librarians presence in traditional classroom environments and or through LMS.
Then opinions vary: According to Kvienlid (2012), http://www.cclibinstruction.org/wp-content/uploads/2012/02/CCLI2012proceedings_Kvenild.pdf
- “Their engagement can be over two or more class sessions, even co-teaching the class in some cases. This model provides in-depth knowledge of student research projects during the research and revision process.” This is for first-year experience students.
- Embedding with project teams in Business and STEM programs involves: “in – depth participation in short – term projects, aiding the team in their searches, literature review, grant preparation, data curation, or other specialized information aspects of the project. This level of embedment requires a heavy time commitment during the length of the project, as well as subject expertise and established trust with the research team.”
-
embedding in departments as a liaison.
“They are usually closely affiliated with the departme nt (maybe even more so than with the libraries) and might be paid out of departmental funds. These librarians learn the ways and needs of their patrons in their natural environment. They often work as finders of information, organizers of information, and taxonomy creators. Embedding within departments provides in – depth knowledge of the users of library services, along with potential isolation from other librarians. It involves a high degree of specialization, co – location and shared responsibility”
best practices, new opptunities (video, screencasts, social media. Adobe Connect) , Assessment
here is Kvenild 2016 article also
Kvenild, C., Tumbleson, B. E., Burke, J. J., & Calkins, K. (2016). Embedded librarianship: questions and answers from librarians in the trenches. Library Hi Tech, 34(2), 8-11.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d124513010%26site%3dehost-live%26scope%3dsite
utilizing technology tools; and providing information literacy and assessment. Technology tools continue to evolve and change, and most librarians can anticipate using multiple learning management systems over time. There is an ongoing need for professional development in online library instruction and assessment
+++++++++++++++++++++++++++++++
Tumbleson, B. E., & Burke, J. (. J. (2013). Embedding librarianship in learning management systems: A how-to-do-it manual for librarians. Neal-Schuman, an imprint of the American Library Association.
https://blog.stcloudstate.edu/ims/2015/05/04/lms-and-embedded-librarianship/
read in red my emphasis on excerpts from that book
++++++++++++++++++++++++++++++++++
Monroe-Gulick, A., O ’brien, M. S., & White, G. (2013). Librarians as Partners: Moving from Research Supporters to Research Partners. In Moving from Research Supporters to Research Partners. Indianapolis, IN. Retrieved from http://www.ala.org/acrl/sites/ala.org.acrl/files/content/conferences/confsandpreconfs/2013/papers/GulickOBrienWhite_Librarians.pdf
From Supporter to Partner
++++++++++++++++++++++
Andrews, C. (2014). An Examination of Embedded Librarian Ideas and Practices: A Critical Bibliography.
http://academicworks.cuny.edu/cgi/viewcontent.cgi?article=1000&context=bx_pubs
emphasis is on undergraduate. “a tremendous amount of literature published addressing library/faculty partnerships.”
“There will never be one golden rule when it comes to way in which a librarian networks with faculty on campus.”
++++++++++++++++
Bobish, G. (2011). Participation and Pedagogy: Connecting the Social Web to ACRL Learning Outcomes. Journal Of Academic Librarianship, 37(1), 54-63.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3daph%26AN%3d57844282%26site%3dehost-live%26scope%3dsite
https://www.researchgate.net/publication/232382226_Participation_and_Pedagogy_Connecting_the_Social_Web_to_ACRL_Learning_Outcomes
requested through researchgate
++++++++++++++++++++++
Cahoy, E. S., & Schroeder, R. (2012). EMBEDDING AFFECTIVE LEARNING OUTCOMES IN LIBRARY INSTRUCTION. Communications In Information Literacy, 6(1), 73-90.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d84110749%26site%3dehost-live%26scope%3dsite
attention must be paid to students’ affective, emotional needs throughout the research
process. My note: And this is exactly what comprise half of my service of. The relatively small amount of research into affective learning, as opposed to cognition, remains true to this day.
p. 78 As the 50-minute one-shot session is still the norm for library research sessions on the
majority of campuses, behavioral assessment can be problematic.
++++++++++++++++++++++++++++++
Cha, T., & Hsieh, P. (2009). A Case Study of Faculty Attitudes toward Collaboration with Librarians to Integrate Information Literacy into the Curriculum. (Chinese). Journal Of Educational Media & Library Sciences, 46(4), 441-467.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d502982677%26site%3dehost-live%26scope%3dsite
Meanwhile, different attitudes were revealed between teaching higher order thinking skills and lower order thinking skills. Librarian Domain Knowledge, Librarian Professionalism, Curriculum Strategies, and Student Learning were identified as factorial dimensions influencing faculty-librarian collaboration.
two major concerns of “Students Learning” and “Librarian Professionalism” from faculty provide insights that understanding pedagogy, enhancing instructional skills and continuing progress in librarian professionalism will contribute to consolidating partnerships when developing course-specific IL programs.
this proves how much right I am to develop: http://web.stcloudstate.edu/pmiltenoff/bi/
++++++++++++++++++
COVONE, N., & LAMM, M. (2010). Just Be There: Campus, Department, Classroom…and Kitchen?. Public Services Quarterly, 6(2/3), 198-207. doi:10.1080/15228959.2010.498768
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d53155456%26site%3dehost-live%26scope%3dsite
p. 199 There is also the concept of the ‘‘blended librarian’’ as described by Bell and Shank (2004) to merge the assets and abilities of a librarian with those of one versed in technology. Academic librarians are obligated and privileged to merge several strengths to meet the needs of their user population. No longer is the traditional passive role acceptable. Bell and Shank (2004) implore academic librarians ‘‘to proactively advance their integration into the teaching and learning process’’ (p. 373).
p. 200 first year experience
++++++++++++++++++++++++++++
Dewey, B. I. (2004). The Embedded Librarian: Strategic Campus Collaborations. Resource Sharing & Information Networks, 17(1-2), 5-17.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3deric%26AN%3dEJ835947%26site%3dehost-live%26scope%3dsite
p. 6 the imperative for academic librarians to become embedded in the priorities of teaching, learning, and research in truly relevant ways. Embedding as an effective mode of collaboration will be explored through examples relating to the physical and virtual environment. An analysis of current approaches and next steps for the future will be addressed, with the goal of providing food for thought as librarians assess programs and activities in terms of positive collaboration and effectiveness
p. 9 new academic salon,
p. 10 the pervasive campus librarian
The fact that we are generalists and devoted to all disciplines and all sectors of the academic user community gives us a special insight on ways to advance the university and achieve its mission
this contradicts Shumaker and Talley, who assert that the embedded librarian is NOT a generalist, but specialist
p. 11 Central administrators, along with the chief academic officer, make critical funding and policy decisions affecting the library
p. 11 librarians and teaching.
In 2011, interim dean Ruth Zietlow “gave up” classes after the messy divorce with CIM. the library faculty poled itself to reveal that a significant number of the faculty does NOT want to teach.
p. 14 influencing campus virtual space
this library’s social media is imploded in its image.
++++++++++++++++++++++++++
DREWES, K., & HOFFMAN, N. (2010). Academic Embedded Librarianship: An Introduction. Public Services Quarterly, 6(2/3), 75-82. doi:10.1080/15228959.2010.498773
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d53155443%26site%3dehost-live%26scope%3dsite
p. 75 Literature about embedded librarianship is so diverse that the definition of this term, as well as related goals and methods when embedding services and programs, can be difficult to define. What are some characteristics of an embedded program? Is embedding only achieved through an online classroom? How did embedded librarianship first begin in academic libraries?
p. 76 adopted as a term because it is a similar concept to embedded journalism.
Embedded librarian programs often locate librarians involved in the spaces of their users and colleagues, either physically or through technology, in order to become a part of their users’ culture. A librarian’s physical and metaphorical location is often what defines them as embedded.
David Shumaker and Mary Talley (see bottom of this blog entry)
Highly technical tasks, such as creating information architecture, using analytical software, and computer and network systems management were performed by less than 20% of the survey respondents. Shumaker and Talley also report embedded services are often found in tandem with specialized funding. This study also confirms embedded services are not new.
p. 77 history and evolution of the role
p. 79 methods of embedding
In North America, one would be hard-pressed to find a library that does not already electronically embed services into online reference chat, make use of Web 2.0 communication applications such as Twitter and blogs, and embed librarians and collaborators within online classrooms. These are all examples of the embedding process (Ramsay & Kinnie, 2006). The name embedded librarian in this context is a double entendre, as the insertion of widgets and multimedia files into HTML code when designing Web sites is usually called the embedding of the file.
My note: is this library actually is one that does not use Twitter and blogs in the hard-core meaning of library service
++++++++++++++++++++++++++++++
Essinger, C. c., & Ke, I. i. (2013). Outreach: What Works?. Collaborative Librarianship, 5(1), 52-58.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d87760803%26site%3dehost-live%26scope%3dsite
Recommendations:
The authors distributed their findings at a half day workshop attended by nearly all liaisons. They made the following recommendations:
- • Personalize outreach.
- • Spend more time marketing and reaching out to departments, even though it might mean having less time for other activities.
- • Find an alternative advocate who can build your reputation through word-ofmouth if your relationship with your assigned department liaison is not fruitful.
- • Seek opportunities to meet department staff in person.
- • As much as possible, administrators should commit to keeping liaisons assignments static.
p. 57 that faculty outreach is similar to other types of relationship building: it requires time to establish trust, respect and appreciation on both sides. Even a liaison’s challenging first two years can, therefore, be viewed as productive because the relationship is developing in the background. This phenomenon also signals to library administrators the benefits of maintaining a stable workforce. Frequent changes in academic assignments and staff changes can lead to a less engaged user population, and also make the outreach assignment much more frustrating.
+++++++++++++++++
Heider, K. L. (2010). Ten Tips for Implementing a Successful Embedded Librarian Program. Public Services Quarterly, 6(2-3), 110-121.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3deric%26AN%3dEJ896199%26site%3dehost-live%26scope%3dsite
embedded librarian program in the university’s College of Education and Educational Technology
p. 112 Make Sure You Have Buy-in from All Stakeholders
Include College=Department Faculty in the Interview Process
Look for the Following Qualities=Qualifications in an Embedded Librarian
Have a Physical Presence in the College=Department a Few Days Each Week
Serve as Bibliographer to College=Department
Offer Bibliographic Instruction Sessions and Guest Lectures at Main Campus, Branch Campuses, and Centers
Develop Collaborative Programs that Utilize the Library’s Resources for College=Department Improvement
#9 Offer to Teach Credit Courses for the College=Department When Department Faculty Are Not Available
#10: Publish Scholarly Works and Present at Professional Conferences with College=Department Faculty. again, Martin Lo, John Hoover,
+++++++++++++++++++
Hollister, C. V. (2008). Meeting Them where They Are: Library Instruction for Today’s Students in the World Civilizations Course. Public Services Quarterly, 4(1), 15-27.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3deric%26AN%3dEJ877341%26site%3dehost-live%26scope%3dsite
history and library. My note: can you break the silo in the history department? https://blog.stcloudstate.edu/ims/2017/05/01/history-becker/
world civilizations course
Faculty come to the world civilizations enterprise from a broad range of academic disciplines and world experiences, which has a significant impact on their interpretations of world history, their selections of course materials, their teaching styles, and their expectations for students. Moreover, faculty teach the course on a rotating basis. So, there is no single model of faculty-librarian collaboration that can be applied from section to section, or even from semester to semester. Faculty have widely differing views on the role of library instruction in their sections of the course, and the extent to which library research is required for coursework. They also differ in terms of their ability or willingness to collaborate with the libraries. As a result, student access to library instruction varies from section to section.
+++++++++++++++++
Kesselman, M. A., & Watstein, S. B. (2009). Creating Opportunities: Embedded Librarians. Journal Of Library Administration, 49(3), 383-400.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d502977425%26site%3dehost-live%26scope%3dsite
p. 384 embedded librarians in the blogosphere.
not even close to the local idea how blog must be used for library use.
p. 387 definitions
p. 389 clinical librarianship – term from the 1970s.
p. 390 Special librarians and particularly those in corporate settings tend to be more integrated within the company they serve and are often instrumental in cost-related services such as competitive intelligence, scientific, and patent research.
p. 391 Librarians Collaborating With Faculty in Scholarly Communication Activities
My note: this is what I am doing with Martin Lo and used to do with John Hoover. Attempts with the sociology department, IS department
p. 392 Role of Librarians With Multidisciplinary Collaborations
my note : my work with Mark Gill and Mark Petzhold
p. 393 social media
again, this library cannot be farther from the true meaning of Web 2.0 collaboration.
p. 396 organizational structures
Three different types of organizational structures are generally recognized—hierarchical, matrix, and flat. We suggest that each of these conventional structures promotes, to some extent, its own brand of silos—silos that inherently pose obstacles to the assumption of new roles and responsibilities. For example, we question whether the hierarchical organization structures that define many of our libraries, with their emphasis on line, lateral staff and functional relationships and the relative ranks of parts and positions or jobs, are flexible enough to support new roles and responsibilities. In contrast, matrix management offers a different type of organizational management model in which people with similar skills are pooled for work assignments. We suggest that, in contrast to hierarchical structures, matrix management allows team members to share information more readily across task boundaries and allows for specialization that can increase depth of knowledge and allow professional development and career progression to be managed. The third organizational structure mentioned—flat or horizontal organizations, refers to an organizational structure with few or no levels of intervening management between staff and managers
+++++++++++++++++
Kobzina, N. G. (2010). A Faculty—Librarian Partnership: A Unique Opportunity for Course Integration. Journal Of Library Administration, 50(4), 293-314.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d502990477%26site%3dehost-live%26scope%3dsite
my LIB 290 is such class. and I am the only one who is teaching it online by QM standards.
Can the administration encourage Global Studies to combine efforts with my LIB 290 and offer a campus-wide class?
++++++++++++++++++++
Lange, J. j., Canuel, R. r., & Fitzgibbons, M. m. (2011). Tailoring information literacy instruction and library services for continuing education. Journal Of Information Literacy, 5(2), 66-80.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d70044774%26site%3dehost-live%26scope%3dsite
McGill. p. 77 The McGill University Library’s system-wide liaison model emphasises a disciplinary approach, placing the impetus for outreach and service on individual librarians responsible for particular departments and user groups.
+++++++++++++++++
MCMILLEN, P., & FABBI, J. (2010). How to Be an E3 Librarian. Public Services Quarterly, 6(2/3), 174-186. doi:10.1080/15228959.2010.497454
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d53155458%26site%3dehost-live%26scope%3dsite
ILL
++++++++++++++++++++
Meyer, N. J., & Miller, I. R. (2008). The Library as Service-Learning Partner: A Win-Win Collaboration with Students and Faculty. College & Undergraduate Libraries, 15(4), 399-413.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d502937618%26site%3dehost-live%26scope%3dsite
ILL
I did something similar with Keith Christensen in 2012: http://bit.ly/SCSUlibGame, yet again, blocked for further consideration
+++++++++++++++++++++
Niles, P. (2011). Meeting the Needs of the 21st Century Student. Community & Junior College Libraries, 17(2), 47-51.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3deric%26AN%3dEJ947074%26site%3dehost-live%26scope%3dsite
about Millennials
millennials. p. 48 my note: the losing battle of telling the millennials the value of books
librarians need to emphasize that not all information
is found on the Web and that the information found there might not be
reliable, depending on its source
p. 49 The latest technology can be used for communication. Two examples of this modernization process are making podcasts of library lectures and using instant messaging to answer reference queries. Students need Reference Librarians to assist them in focusing their research, showing them appropriate sources and how to use those sources. The change is not how the librarians serve the students but how the service is delivered. Instead of coming to the reference desk Millennial students may choose to use e-mail, cell phones to send a text message or use a chat reference service to communicate with the librarian. Students want to have 24/7 access to library resources and librarians.
my note: and yet this library still uses 90ish communication – the facebook page is just an easy to edit web page and the concept of Web 2.0 has not arrived or shaped the current communication.
p. 50 Librarians should examine how they present library instruction and ensure that students know why it is important. Further, Lancaster and Stillman state that librarians need to “incorporate some computer-based instruction for Millennials as it allows them to go at their own speed and acknowledges their ability to manage information” (2003, 231).
and, once again, talking about inducing library instruction with technology: http://web.stcloudstate.edu/pmiltenoff/bi/
+++++++++++++++++++
Oakleaf, M., & VanScoy, A. (2010). Instructional Strategies for Digital Reference: Methods to Facilitate Student Learning. Reference & User Services Quarterly, 49(4), 380-390.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d502996462%26site%3dehost-live%26scope%3dsite
constructivism, social constructivism, active learning
they have a graph about metacognition. I wish, they had found place for metaliteracy also
p. 383. #5 Let them drive. this is EXACTLY what I am offering with:http://web.stcloudstate.edu/pmiltenoff/bi/
build their own construct
p. 386 my work with the doctoral cohorts:
In the current climate of educational accountability, reference librarians should embrace the opportunity to align reference service with the teaching and learning missions of their libraries and overarching institutions
+++++++++++++++++
Rao, S., Cameron, A., & Gaskin-Noel, S. (2009). Embedding General Education Competencies into an Online Information Literacy Course. Journal Of Library Administration, 49(1/2), 59-73.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d502963853%26site%3dehost-live%26scope%3dsite
online programs a 3-credit junior seminar course (JRSM 301) to assess general education competencies
p. 60 The 3-credit course titled LISC 260—Using Electronic Resources for Research has existed as a required course for this overseas cohort of students since the fall of 1999. The course was initially developed as a required course to introduce the Mercy College Libraries’ resources to this cohort of overseas students. Full-time librarians teach this course as an overload.
The course lasts for 8 weeks during fall and spring semesters and is divided into eight modules with five quizzes. Summer sessions are shorter; the summer version of the course runs for 6 weeks. There is no midterm exam, final exam, project, or term paper for this course. Sixty percent of the grade is based on the quizzes and assignments and 40% on discussion and class participation.
Each quiz addresses a specific competency. We identified the modules where the five competencies would fit best. A document containing the five general education competencies (critical thinking, information literacy, quantitative reasoning, critical reading, and writing) statements
Critical Thinking Competency This competency was placed in the second module covering the topic “Developing Search Strategies” in the second week of the course. In this module, students are required to select a topic and develop logical terminologies and search strings. This task requires a great deal of critical and analytical thinking and therefore lays the groundwork for the other competencies. The quizzes and assignments for this competency involve breaking or narrowing down the topic into subtopics, comparing two topics or ideas, and similar skills. It is hoped that students will be able to adopt Boolean and other search logic in clear and precise ways in their analyses and interpretations of their topic and use the search strategies they develop for continued assignments throughout the rest of the course.
p. 61. Information Literacy Competency The information literacy competency is introduced in the fourth module in the fourth week of the course. As part of the course, students are required to learn about the Mercy College Libraries’ indexes and databases, which this module addresses (“Information Literacy,” n.d.).
Quantitative Reasoning Competency
This seminar course is a library research course with no statistics or mathematics component. Many students enrolled in the course are not mathematics or statistics majors, hence some creativity was needed to evaluate their mathematical and computational skills. Students are given this competency in the fifth module during the fifth week of the course, which deals with subject-specific sources. It was decided that, to assess this competency, a quiz analyzing data obtained in a tabular format from one of the databases subscribed to by the library would fulfill the requirement. Students are given a choice of various countries and related data, and are asked to create some comparative demographic profiles. This approach has worked well because it gives students the opportunity to focus on countries and data that interest them.
++++++++++++++++++
Abrizah, A., Inuwa, S., & Afiqah-Izzati, N. (2016). Systematic Literature Review Informing LIS Professionals on Embedding Librarianship Roles. Journal Of Academic Librarianship, 42(6), 636-643. doi:10.1016/j.acalib.2016.08.010
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dlxh%26AN%3d119652419%26site%3dehost-live%26scope%3dsite
requested through research gate
+++++++++++++++++++
Summey, T. P., & Kane, C. A. (2017). Going Where They Are: Intentionally Embedding Librarians in Courses and Measuring the Impact on Student Learning. Journal Of Library & Information Services In Distance Learning, 11(1/2), 158-174. doi:10.1080/1533290X.2016.1229429
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d121839436%26site%3dehost-live%26scope%3dsite
a pilot project utilizing a variety of methods.
p. 158 The concept of embedded librarians is not new, as it has antecedents in branch librarians of the seventies and academic departmental liaisons of the 1980s and 1990s. However, it is a way to proactively reach out to the campus community (Drewes & Hoffman, 2010).
There is not a one-size-fits-all definition for embedded librarianship. As a result, librarians in academic libraries may be embedded in their communities in a variety of ways and at varying levels from course integrated instruction to being fully embedded as a member of an academic department
p. 160 my note: the authors describe the standard use of LMS for embedded librarianship.
p. 163 they managed to fight out and ensure their efforts are “credited.” Assigning credits to embedded librarian activities can be a very tough process.
p. 165 assessment
the authors utilized a pre-module and post-module survey to assess the students’ performance using library resources. The survey also helped to determine the students’ perceived self-efficacy and confidence in using the library, its resources, and services. In addition, the researchers analyzed student responses to discussion questions, studied feedback at the end of the course in the course discussion forum, and conducted interviews with the faculty members teaching the courses (
In another study, researchers analyzed bibliographies of students in the course to identify what resources they cited in their research projects. More specifically, they analyzed the type and appropriateness of sources used by the students, their currency, and noting how deeply the students delved into their topics. They also looked at the number of references cited. The authors believed that examining the bibliographies provided an incomplete picture because it provided data on the sources selected by the students but not information on how they retrieved those sources.
p. 171 survey sample
+++++++++++++++++
Wu, L., & Thornton, J. (2017). Experience, Challenges, and Opportunities of Being Fully Embedded in a User Group. Medical Reference Services Quarterly, 36(2), 138-149. doi:10.1080/02763869.2017.1293978
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d122763145%26site%3dehost-live%26scope%3dsite
this is somehow close to my role with the EDAD
Texas A&M University academic health sciences library integrating a librarian into the College of Pharmacy, approximately 250 miles away from the main library. preembedded and postembedded activities demonstrated the effectiveness and impact of
For this study, the fully embedded librarian is defined as one who is out of the traditional library and into an onsite setting to provide a full range of library services that enable collaboration with researchers or teaching faculty and support student learning. In this model, the embedded librarian is a team member of the RCOP rather than a service provider standing apart. The lines are not blurred as to the kind of services that should be embedded because the embedded librarian is 100% onsite. Very few reports in the literature describe fully embedded librarian models such as this. However, one similar model exists at the Arizona Health Sciences Library (AHSL), which is affiliated with the University of Arizona, where librarians relocated their permanent offices to the colleges of Nursing, Public Health, and Pharmacy. AHSL librarians spent close to 100% of their time in the colleges.
p. 144 The embedded librarian has gained recognition in the college and was appointed by the dean to serve on the Instructional Venues Ad Hoc Committee (IVC).
My note: This is what Tom Hergert and I have been advocating for years: the role of the librarian is not to find info and teach how to find info ONLY. The role of the librarian is to bring 21st century to School of Education: information literacy is only a fragment of metaliteracies. Information literacy is a 1990s priority. While it is still an important part of librarians goals, digital literacy, visual and media literacy, as well as technology literacy and pedagogical application of technology is imposed as integral part of the work of the embedded librarian.
p. 145 Challenges and Opportunities
Another challenge involved the librarian’s decision-making and effective communications skills, especially when deciding to implement library services or programs. Other challenges included speaking the client group’s language and knowing the information needs of each group—faculty, students, staff, postdocs, research assistants, and research scientists—to deliver the right information at the point of need. The following strategies were practiced to overcome these challenges: .
- A positive attitude can increase connectivity, networking, and collaboration beyond a limited space. Proactively seeking opportunities to participate and get involved in library events, instructional programs, training workshops, or committee work shortened the distance between the remote librarian and those in main campus. .
- As video conferencing tools or programs (e.g., Adobe Connnect, Webex, Skype, Google Hangout, Zoom) were the primary means for the remote at 18:19 24 August 2017 librarian to attend library meetings and teach in library instructional programs, spending some time learning to use these tools and embracing them greatly increased the librarian’s capacity to overcome the feelings of disconnection.
- The willingness to travel several times a year to the main campus to meet librarians face-to-face helped in understanding the system and in getting help that seemed complicated and difficult via remote resources (e.g., computer issues). .
- Actively listening to the faculty and students during the conversations helped understand their information needs. This served as the basis to initiate any targeted library services and programs.
Despite the challenges, the embedded librarian was presented with numerous opportunities that a traditional librarian might think impossible or difficult to experience, for example, attending RCOP department meetings or RCOP executive committee meetings to present library resources and services, serving on RCOP committees, co-teaching with faculty in RCOP credit courses, creating and grading assignments counting toward total course credits, and being given access to all RCOP course syllabi in eCampus. (the last is in essence what I am doing right now)
p. 147 Marketing Embedded Library Services
The “What’s in It for Me” (WIIFM) principle1 was a powerful technique to promote embedded library services. The essentials of WIIFM are understanding patron needs and ensuring the marketing effort or communications addressing those needs15—in other words, always telling patrons what is in it for them when promoting library services and resources. Different venues were used to practice WIIFM: .
- RCOP faculty email list was an effective way to reach out to all the faculty. An email message at the beginning of a semester to the faculty highlighted the embedded librarian’s services. During the semester, the librarian communicated with the faculty on specific resources and services addressing their needs, such as measuring their research impact at the time of their annual evaluation, sharing grant funding resources, and promoting MSL’s resources related to reuse of images. .
- Library orientations to new students and new faculty allowed the librarian to focus on who to contact for questions and help, available resources, and ways to access them. . Being a guest speaker for the monthly RCOP departmental faculty meetings provided another opportunity for the librarian to promote services and resources.
- Casual conversations with faculty, students, researchers, and postdocs in the hallway, at staff luncheons, and at RCOP events helped understand their information needs, which helped the librarian initiate MSL service projects and programs.
- The Facebook private group, created by Instructional Technology & MSL Resources @ Rangel COP, was used to announce MSL resources and services. The group currently has 256 members. The librarian is one of the group administrators who answers student questions related to library and MSL resources. (social media is my forte)
p. 148 This model would not have been successful without the strong support from MSL leadership team and the RCOP administration.
the next step would be to conduct a systematic assessment to get feedback from RCOP administrators, faculty, students, staff, postdocs, and research assistants. The integration of the library instructional program into the RCOP curriculum should be included in RCOP final course evaluations. Another future direction might be to conduct a curriculum map to get a better idea about the learning objectives of each course and to identity information literacy instruction needs across the curriculum. The curriculum mapping might also help better structure library instruction delivery to RCOP. Teaching content might be structured more purposefully and logically sequenced across the curriculum to ensure that what students have learned in one course prepares them for the next ones.
+++++++++++++++++++
Blake, L., Ballance, D., Davies, K., Gaines, J. K., Mears, K., Shipman, P., & … Burchfield, V. (2016). Patron perception and utilization of an embedded librarian program. Journal Of The Medical Library Association, 104(3), 226-230. doi:10.3163/1536-5050.104.3.008
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d116675007%26site%3dehost-live%26scope%3dsite
The overall satisfaction with services was encouraging, but awareness of the embedded program was low, suggesting an overall need for marketing of services.
+++++++++++++++++++
Tumbleson, B. E. (2016). Collaborating in Research: Embedded Librarianship in the Learning Management System. Reference Librarian, 57(3), 224-234. doi:10.1080/02763877.2015.1134376
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d114820440%26site%3dehost-live%26scope%3dsite
+++++++++++++++++++
O’Toole, E., Barham, R., & Monahan, J. (2016). The Impact of Physically Embedded Librarianship on Academic Departments. Portal: Libraries & The Academy, 16(3), 529-556.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d116715636%26site%3dehost-live%26scope%3dsite
++++++++++++++
Agrawal, P. p., & Kumar, A. (2016). Embedded Librarianship and Academic Setup: Going beyond the library stockades. International Journal Of Information Dissemination & Technology, 6(3), 170-173.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dllf%26AN%3d119763981%26site%3dehost-live%26scope%3dsite
India. p. 173 as of today, most of the users are not able to differentiate the library professional who have a bachelor degree, Masters degree and who are doctorate of the subject. My note: not in my case and this is my great advantage.
+++++++++++++++++
Madden, H., & Rasmussen, A. M. (2016). Embedded Librarianship: Einbindung von Wissenschafts- und Informationskompetenz in Schreibkurse / Ein US-amerikanisches Konzept. Bub: Forum Bibliothek Und Information, 68(4), 202-205.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dlxh%26AN%3d114671852%26site%3dehost-live%26scope%3dsite
ILL
+++++++++++++++++
Delaney, G., & Bates, J. (2015). Envisioning the Academic Library: A Reflection on Roles, Relevancy and Relationships. New Review Of Academic Librarianship, 21(1), 30-51. doi:10.1080/13614533.2014.911194
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d101516816%26site%3dehost-live%26scope%3dsite
overview of the literature on embedded librarianship
+++++++++++++++++++
Freiburger, G., Martin, J. R., & Nuñez, A. V. (2016). An Embedded Librarian Program: Eight Years On. Medical Reference Services Quarterly, 35(4), 388-396. doi:10.1080/02763869.2016.1220756
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d118281342%26site%3dehost-live%26scope%3dsite
close to my role with the doctoral cohorts
++++++++++++++++++++++
Wilson, G. (2015). The Process of Becoming an Embedded Curriculum Librarian in Multiple Health Sciences Programs. Medical Reference Services Quarterly, 34(4), 490-497. doi:10.1080/02763869.2015.1082386
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3dkeh%26AN%3d110525415%26site%3dehost-live%26scope%3dsite
ILL
+++++++++++++++++++++
Milbourn, A. a. (2013). A Big Picture Approach: Using Embedded Librarianship to Proactively Address the Need for Visual Literacy Instruction in Higher Education. Art Documentation: Bulletin Of The Art Libraries Society Of North America, 32(2), 274-283.
http://login.libproxy.stcloudstate.edu/login?qurl=http%3a%2f%2fsearch.ebscohost.com%2flogin.aspx%3fdirect%3dtrue%26db%3daft%26AN%3d92600699%26site%3dehost-live%26scope%3dsite
visual literacy – this is IMS area, which was de facto shot off by the omnipotence of “information literacy”
+++++++++++++++++
Talley, M. (2007). Success and the Embedded Librarian. https://www.sla.org/wp-content/uploads/2013/05/Success_and_the_Embedded.pdf
Shumaker, D., Talley, M. Models of Embedded Librarianship: A Research Summary. https://www.sla.org/wp-content/uploads/2013/05/Models_of_Embedded.pdf
Shumaker, D., Talley, M. (2009). Models of Embedded Librarianship. Final Report. Prepared under the Special Libraries Association Research Grant 2007. https://embeddedlibrarian.files.wordpress.com/2009/08/executivesummarymodels-of-embedded-librarianship.pdf
Shumaker, D. (2013). Embedded Librarianship: Digital World Future? http://www.infotoday.com/CIL2013/session.asp?ID=W30
slide 8: vision of embedded librarianship:
customer centric not library centric; located in their workplace not our workplace; focused on small groups not entire populations; composed of specialists, not generalists; dependent on domain knowledge not only library skills; aming an analysis and synthesis not simply delivery; in context, not out of context; built on trusted advice not service delivery
all of the above is embodied in my work with the doctoral cohorts
slide 9: why study? because traditional library service model is in decline
slide 11: broad analytical research on successful implementation is lacking
slide 20: large institutions more likely to offer specialized services
slide 21: domain knowledge through continuous learning, not always through formal degrees.
slide 39: what matters most
slide 40: strong leadership by library managers is critical (I will add here “by deans of other colleges)
+++++++++++++++++++++
bibliography:
Abrizah, A., Inuwa, S., & Afiqah-Izzati, N. (2016). Systematic Literature Review Informing LIS Professionals on Embedding Librarianship Roles. Journal Of Academic Librarianship, 42(6), 636-643. doi:10.1016/j.acalib.2016.08.010
Agrawal, P. p., & Kumar, A. (2016). Embedded Librarianship and Academic Setup: Going beyond the library stockades. International Journal Of Information Dissemination & Technology, 6(3), 170-173.
Andrews, C. R. (2014). CUNY Academic Works An Examination of Embedded Librarian Ideas and Practices: A Critical Bibliography. An Examination of Embedded Librarian Ideas and Practices: A Critical Bibliography. Codex, 3(1), 2150–86. Retrieved from http://academicworks.cuny.edu/bx_pubs
Blake, L., Ballance, D., Davies, K., Gaines, J. K., Mears, K., Shipman, P., & … Burchfield, V. (2016). Patron perception and utilization of an embedded librarian program. Journal Of The Medical Library Association, 104(3), 226-230. doi:10.3163/1536-5050.104.3.008
Bobish, G. (2011). Participation and Pedagogy: Connecting the Social Web to ACRL Learning Outcomes. Journal Of Academic Librarianship, 37(1), 54-63.
Cahoy, E. S., & Schroeder, R. (2012). EMBEDDING AFFECTIVE LEARNING OUTCOMES IN LIBRARY INSTRUCTION. Communications In Information Literacy, 6(1), 73-90.
Cha, T., & Hsieh, P. (2009). A Case Study of Faculty Attitudes toward Collaboration with Librarians to Integrate Information Literacy into the Curriculum. (Chinese). Journal Of Educational Media & Library Sciences, 46(4), 441-467.
COVONE, N., & LAMM, M. (2010). Just Be There: Campus, Department, Classroom…and Kitchen?. Public Services Quarterly, 6(2/3), 198-207. doi:10.1080/15228959.2010.498768
Delaney, G., & Bates, J. (2015). Envisioning the Academic Library: A Reflection on Roles, Relevancy and Relationships. New Review Of Academic Librarianship, 21(1), 30-51. doi:10.1080/13614533.2014.911194
Dewey, B. I. (2004). The Embedded Librarian: Strategic Campus Collaborations. Resource Sharing & Information Networks, 17(1-2), 5-17.
DREWES, K., & HOFFMAN, N. (2010). Academic Embedded Librarianship: An Introduction. Public Services Quarterly, 6(2/3), 75-82. doi:10.1080/15228959.2010.498773
Essinger, C. c., & Ke, I. i. (2013). Outreach: What Works?. Collaborative Librarianship, 5(1), 52-58.
Freiburger, G., Martin, J. R., & Nuñez, A. V. (2016). An Embedded Librarian Program: Eight Years On. Medical Reference Services Quarterly, 35(4), 388-396. doi:10.1080/02763869.2016.1220756
Heider, K. L. (2010). Ten Tips for Implementing a Successful Embedded Librarian Program. Public Services Quarterly, 6(2-3), 110-121.
Hollister, C. V. (2008). Meeting Them where They Are: Library Instruction for Today’s Students in the World Civilizations Course. Public Services Quarterly, 4(1), 15-27.
Kesselman, M. A., & Watstein, S. B. (2009). Creating Opportunities: Embedded Librarians. Journal Of Library Administration, 49(3), 383-400.
Kobzina, N. G. (2010). A Faculty—Librarian Partnership: A Unique Opportunity for Course Integration. Journal Of Library Administration, 50(4), 293-314.
Kvenild, C. (n.d.). The Future of Embedded Librarianship: Best Practices and Opportunities. Retrieved from http://www.cclibinstruction.org/wp-content/uploads/2012/02/CCLI2012proceedings_Kvenild.pdf
Lange, J. j., Canuel, R. r., & Fitzgibbons, M. m. (2011). Tailoring information literacy instruction and library services for continuing education. Journal Of Information Literacy, 5(2), 66-80.
Madden, H., & Rasmussen, A. M. (2016). Embedded Librarianship: Einbindung von Wissenschafts- und Informationskompetenz in Schreibkurse / Ein US-amerikanisches Konzept. Bub: Forum Bibliothek Und Information, 68(4), 202-205.
MCMILLEN, P., & FABBI, J. (2010). How to Be an E3 Librarian. Public Services Quarterly, 6(2/3), 174-186. doi:10.1080/15228959.2010.497454
Meyer, N. J., & Miller, I. R. (2008). The Library as Service-Learning Partner: A Win-Win Collaboration with Students and Faculty. College & Undergraduate Libraries, 15(4), 399-413.
Milbourn, A. (2013). A Big Picture Approach: Using Embedded Librarianship to Proactively Address the Need for Visual Literacy Instruction in Higher Education. Art Documentation: Bulletin Of The Art Libraries Society Of North America, 32(2), 274-283.
The Changing Roles of Academic and Research Libraries – Higher Ed Careers – HigherEdJobs. (2013). Retrieved from https://www.higheredjobs.com/HigherEdCareers/interviews.cfm?ID=632
Niles, P. (2011). Meeting the Needs of the 21st Century Student. Community & Junior College Libraries, 17(2), 47-51.
Oakleaf, M., & VanScoy, A. (2010). Instructional Strategies for Digital Reference: Methods to Facilitate Student Learning. Reference & User Services Quarterly, 49(4), 380-390.
O’Toole, E., Barham, R., & Monahan, J. (2016). The Impact of Physically Embedded Librarianship on Academic Departments. Portal: Libraries & The Academy, 16(3), 529-556.
Rao, S., Cameron, A., & Gaskin-Noel, S. (2009). Embedding General Education Competencies into an Online Information Literacy Course. Journal Of Library Administration, 49(1/2), 59-73.
Shumaker, D., Talley, M. Models of Embedded Librarianship: A Research Summary. https://www.sla.org/wp-content/uploads/2013/05/Models_of_Embedded.pdf
Shumaker, D., Talley, M. (2009). Models of Embedded Librarianship. Final Report. Prepared under the Special Libraries Association Research Grant 2007. https://embeddedlibrarian.files.wordpress.com/2009/08/executivesummarymodels-of-embedded-librarianship.pdf
Shumaker, D. (2013). Embedded Librarianship: Digital World Future? http://www.infotoday.com/CIL2013/session.asp?ID=W30
Summey, T. P., & Kane, C. A. (2017). Going Where They Are: Intentionally Embedding Librarians in Courses and Measuring the Impact on Student Learning. Journal Of Library & Information Services In Distance Learning, 11(1/2), 158-174. doi:10.1080/1533290X.2016.1229429
Talley, M. (2007). Success and the Embedded Librarian. https://www.sla.org/wp-content/uploads/2013/05/Success_and_the_Embedded.pdf
Tumbleson, B. E., & Burke, J. (John J. . (2013). Embedding librarianship in learning management systems : a how-to-do-it manual for librarians. Retrieved from http://www.worldcat.org/title/embedding-librarianship-in-learning-management-systems-a-how-to-do-it-manual-for-librarians/oclc/836261183
Tumbleson, B. E. (2016). Collaborating in Research: Embedded Librarianship in the Learning Management System. Reference Librarian, 57(3), 224-234. doi:10.1080/02763877.2015.1134376
Wilson, G. (2015). The Process of Becoming an Embedded Curriculum Librarian in Multiple Health Sciences Programs. Medical Reference Services Quarterly, 34(4), 490-497. doi:10.1080/02763869.2015.1082386
Wu, L., & Thornton, J. (2017). Experience, Challenges, and Opportunities of Being Fully Embedded in a User Group. Medical Reference Services Quarterly, 36(2), 138-149. doi:10.1080/02763869.2017.1293978
+++++++++++++++++
more about embedded librarian in this IMS blog
https://blog.stcloudstate.edu/ims?s=embedded+librarian
Privacy & Security in Today’s Library by Amigos Library Services
From: Jodie Borgerding [mailto:Borgerding@amigos.org]
Sent: Wednesday, July 05, 2017 3:07 PM
To: Miltenoff, Plamen <pmiltenoff@stcloudstate.edu>
Cc: Nicole Walsh <WALSH@AMIGOS.ORG>
Subject: Proposal Submission for Privacy & Security Conference
Hi Plamen,
Thank you for your recent presentation proposal for the online conference, Privacy & Security in Today’s Library, presented by Amigos Library Services. Your proposal, The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party,” has been accepted. I just wanted to confirm that you are still available to present on September 21, 2017 and if you have a time preference for your presentation (11 am, 12 pm, or 2 pm Central). If you are no longer able to participate, please let me know.
Nicole will be touch with you shortly with additional details and a speaker’s agreement.
Please let me know if you have any questions.
Thanks!
___________________
Jodie Borgerding Consulting & Education Services Manager Amigos Library Services 1190 Meramec Station Road, Suite 207 | Ballwin, MO 63021-6902 800-843-8482 x2897 | 972-340-2897(direct) http://www.amigos.org | borgerding@amigos.org
+++++++++++++++++
Bio
Dr. Plamen Miltenoff is an Information Specialist and Professor at St. Cloud State University. His education includes several graduate degrees in history and Library and Information Science and terminal degrees in education and psychology.
His professional interests encompass social media, multimedia, Web development and design, gaming and gamification, and learning environments (LEs).
Dr. Miltenoff organized and taught classes such as LIB 290 “Social Media in Global Context” (http://web.stcloudstate.edu/pmiltenoff/lib290/) and LIB 490/590 “Digital Storytelling” (http://web.stcloudstate.edu/pmiltenoff/lib490/) where issues of privacy and security are discussed.
Twitter handle @SCSUtechinstruc
Facebook page: https://www.facebook.com/InforMediaServices/
The virtuality of privacy and security on the modern campus:
The role of the library in teaching with technology unsupported by campus IT: the privacy and security issues of the “third-party software” teaching and learning
Abstract/Summary of Your Proposed Session
The virtualization reality changes rapidly all aspects of learning and teaching: from equipment to methodology, just when faculty have finalized their syllabus, they have to start a new, if they want to keep abreast with content changes and upgrades and engagement of a very different student fabric – Millennials.
Mainframes are replaced by microcomputers, microcomputers by smart phones and tablets, hard drives by cloud storage and wearables by IoT. The pace of hardware, software and application upgrade is becoming unbearable for students and faculty. Content creation and methodology becomes useless by the speed of becoming obsolete. In such environment, faculty students and IT staff barely can devote time and energy to deal with the rapidly increasing vulnerability connected with privacy and security.
In an effort to streamline ever-becoming-scarce resources, campus IT “standardizes” campus use of applications. Those are the applications, which IT chooses to troubleshoot campus-wide. Those are the applications recommended to faculty and students to use.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal, attention on campuses is drown to the fact that cyberattacks shift now from mobile devices to IoT and campus often are struggling even with their capability to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party application might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
Abstract
The pace of changes in teaching and learning is becoming impossible to sustain: equipment evolves in accelerated pace, the methodology of teaching and learning cannot catch up with the equipment changes and atop, there are constant content updates. In an even-shrinking budget, faculty, students and IT staff barely can address the issues above, less time and energy left to address the increasing concerns about privacy and security.
In an unprecedented burgeoning amount of applications, specifically for mobile devices, it is difficult to constraint faculty and students to use campus IT sanctioned applications, especially considering the rapid pace of such applications becoming obsolete. Faculty and students often “stray” away and go with their own choice. Such decision exposes faculty and students, personally, and the campus, institutionally, at risk. In a recent post by THE Journal (https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/), attention on campuses is drawn to the fact of cyberattacks shifting from mobile devices to IoT but campus still struggling to guarantee cybersecurity of mobile devices on campus. Further, the use of third-party applications might be in conflict with the FERPA campus-mandated policies. Such policies are lengthy and complex to absorb, both by faculty and students and often are excessively restrictive in terms of innovative ways to improve methodology and pedagogy of teaching and learning. The current procedure of faculty and students proposing new applications is a lengthy and cumbersome bureaucratic process, which often render the end-users’ proposals obsolete by the time the process is vetted.
Where/what is the balance between safeguarding privacy on campus and fostering security without stifling innovation and creativity? Can the library be the campus hub for education about privacy and security, the sandbox for testing and innovation and the body to expedite decision-making?
https://blog.stcloudstate.edu/ims/2017/06/06/cybersecurity-and-students/
Anything else you would like to add
3 take-aways from this session:
- Discuss and form an opinion about the education-pertinent issues of privacy and security from the broad campus perspective, versus the narrow library one
- Discuss and form an opinion about the role of the library on campus in terms of the greater issues of privacy and security
Re-examine the thin red line of the balance between standardization and innovation; between the need for security and privacy protection a
++++++++++++++
presentation:
https://www.slideshare.net/aidemoreto/the-virtuality-of-privacy-and-security-on-the
chat – slide 4, privacy. please take 2 min and share your definition of privacy on campus. Does it differ between faculty and students? what are the main characteristics to determine privacy
chat – slide 5, security. please take 2 min and share your definition of security on campus regarding electronic activities. Who’s responsibility is security? IT issue [only]?
poles: slide 6, technology unsupported by campus IT, is it worth considering? 1. i am a great believer in my freedom of choice 2. I firmly follow rules and this applies to the use of computer tools and applications 3. Whatever…
chat – slide 6, why third party applications? pros and cons. E.g. pros – familiarity with third party versus campus-required
pole, slide 6, appsmashing. App smashing is the ability to combine mobile apps in your teaching process. How do you feel about it? 1. The force is with us 2. Nonsense…
pole slide 7 third party apps and the comfort of faculty. How do you see the freedom of using third party apps? 1. All I want, thank you 2. I would rather follow the rules 3. Indifference is my middle name
pole slide 8 Technology standardization? 1. yes, 2. no, 3. indifferent
chat slide 9 if the two major issues colliding in this instance are: standardization versus third party and they have impact on privacy and security, how would you argue for the one or the other?
++++++++++++++++
notes from the conference
Speaker: Dr. Steve Albrecht – drsteve@drstevealbrecht.com
Follow @DrSteveAlbrecht
Dr. Steve Albrecht, author of Library Security: Better Communication, Safer Facilities, manages a training, coaching, and management consulting firm, using a dedicated and experienced team of subcontractor specialists. He is internationally known for his consulting and training work in workplace violence prevention training programs, school violence prevention, and high-risk human resources. Dr. Albrecht provides HR consulting, site security assessments, coaching, and training workshops in supervisory improvement, workplace violence prevention, harassment prevention, drug and alcohol awareness, team building, and more. He holds a B.A. in English, B.S. in Psychology, M.A. in Security Management, and a doctoral degree in Business Administration (D.B.A.). He has been a trainer for over 26 years and is a certified Professional in Human Resources (PHR), a Certified Protection Professional (CPP), a Board Certified Coach (BCC), and a Certified Threat Manager (CTM).
Session Description: Libraries don’t always need to hire a consultant to review the level of facility security. Using a structured assessment process, librarians can create a report that will help to make their building, staff, and patrons safer.
Chris Markman, MSLIS, MSIT Public Services Librarian Worcester Public Library
https://mycourses.amigos.org/mod/url/view.php?id=19623
Measuring Library Vendor Cyber Security: Seven Easy Questions Every Librarian Can Ask
http://journal.code4lib.org/articles/11413
Bill Walker: http://www.amigos.org/innovating_metadata
+++++++++++++++
more on security in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=security
more on privacy in education in this IMS blog
https://blog.stcloudstate.edu/ims?s=privacy